Question
Write a C++ encryption and decryption program based on string manipulation . Given a string plaintext, it is encrypted as following: plaintext is first shifted
Write a C++ encryption and decryption program based on string manipulation. Given a string plaintext, it is encrypted as following:
plaintext is first shifted right length() / 2 positions (toward higher index).
Next each letter is transformed:
If an uppercase letter: 'A'->'Z', 'B'->'Y', ... 'M'->'N', 'N'->'M', ..., 'Y'->'B', 'Z'->'A'
If a lowercase letter: same idea as for uppercase letter. i.e. 'a' -> 'z', 'b'->'y', ..., 'y'->'b', 'z'->'a'
If a digit: same idea as for uppercase letter. i.e. '0' ->'9', '1'->'8', '2'->'7' ...
Anything else remains the same.
For example, given a plain text of Secret 12, its changed into:
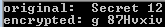
// index: 0 1 2 3 4 5 6 7 8
// S e r e c t 1 2
// length is 9, so shift 4 times toward right (9/2 is 4, int division. If length is 10, should shift 5 times)
// After shifting:
t 1 2 S e r e c
// next change each character:
g 8 7 H v x i v
Your program should include at least the following:
One function to encrypt a given plain text string as explained above. It should return a string containing the corresponding cipher text.
One function to decrypt a cipher text that has been encrypted as explained above. This function should return the decrypted text as a string.
You may add additional function(s) which is(are) necessary for your design.
Include in your main() one or more testing cases, with each testing case tests both the encryption function and the decryption function:
std::string str = "Secret 12";
std::string secretStr = encrypt(str);
std::cout
std::cout
std::cout
Your code should also contain:
Algorithms (pseudo code) for your encryption function as block comments at the beginning of your source code file. If you choose to draw flowchart, include it in your HW document instead.
/*IN*/, /*OUT*/, /*INOUT*/ comments to each function parameter.
Pre- and Post- condition comments for each function.
Do not use global variables
Provide at least three testing cases (sample input and expected output for each testing case) and explain why you pick those three. Provide screenshots of the execution matching your three testing cases.
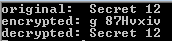
priginal Secret 12 encrypted: g 87HvxiiuStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


