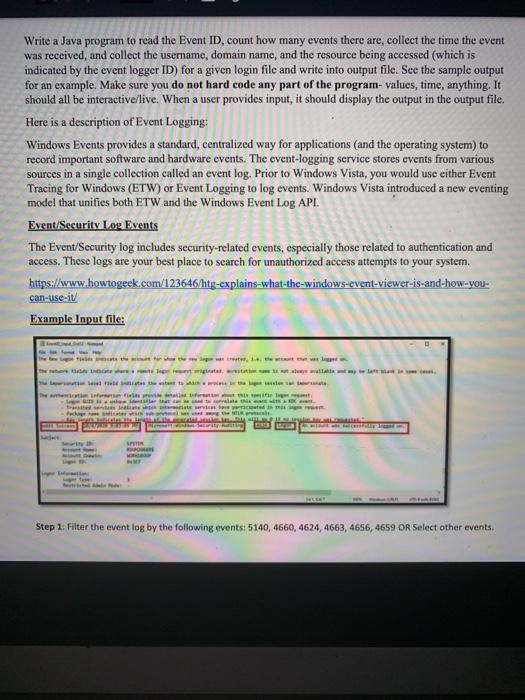
Write a program in JAVA to read the Event ID, count how many events there are, collect the time the event was received, and collect the username, domain name, and the resource being accessed (which is indicated by the event logger ID) for a given login file and write into output file. See the sample output for an example. Make sure you do not hard code any part of the program- values, time, anything. It should all be interactive/live. When a user provides input, it should display the output in the output file. Here is a description of Event Logging: Windows Events provides a standard, centralized way for applications (and the operating system) to record important software and hardware events. The event-logging service stores events from various sources in a single collection called an event log. Prior to Windows Vista, you would use either Event Tracing for Windows (ETW) or Event Logging to log events. Windows Vista introduced a new eventing model that unifies both ETW and the Windows Event Log API. Event/Security Log Events The Event/Security log includes security-related events, especially those related to authentication and access. These logs are your best place to search for unauthorized access attempts to your system.
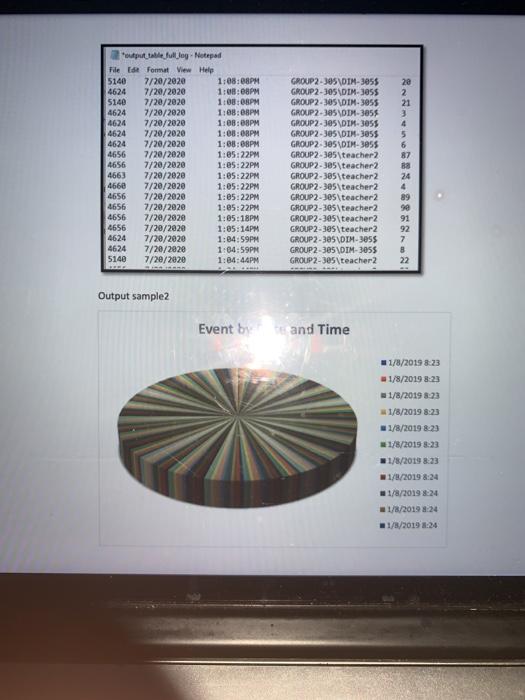
to read the Event Write a Java program to read the Event ID, count how many events there are, collect the time the event was received, and collect the username, domain name, and the resource being accessed (which is indicated by the event logger ID) for a given login file and write into output file. See the sample output for an example. Make sure you do not hard code any part of the program-values, time, anything. It should all be interactive/live. When a user provides input, it should display the output in the output file. Here is a description of Event Logging: Windows Events provides a standard, centralized way for applications (and the operating system) to record important software and hardware events. The event-logging service stores events from various sources in a single collection called an event log. Prior to Windows Vista, you would use either Event Tracing for Windows (ETW) or Event Logging to log events. Windows Vista introduced a new eventing model that unifies both ETW and the Windows Event Log API. Event/Security Log Events The Event/Security log includes security-related events, especially those related to authentication and access. These logs are your best place to search for unauthorized access attempts to your system. https:/www.howtogeek.com/123646/htg-explains-what-the-windows-event-viewer-is-and-how-you- can-use-it/ Example Input file: we will still man e tutto Norte 1 word ES STIR Step 1: Filter the event log by the following events: 5140, 4660,4624, 4663,4656, 4659 OR Select other events. 3 / 6 100% + A OS 041 Step 2: Then save filtered event log as a tab delimited, text file called input_log.txt Make sure input file and this application is in the same folder. Outputs will be created in the same folder. Step3: Search by Event ID: 5140: A network share object was accessed 4624: An account was successfully logged on 4656: A handle to an object was requested 4659: A handle to an object was requested with intent to delete 4663: An attempt was made to access an object 4660: An object was deleted output_table full deg. Notepad File Format View Help 5140 7/20/2020 1:08:08PM 4624 7/29/2020 1:08:08PM 5140 7/20/2020 1:03:08PM 4624 7/20/2020 1:08:08PM 4624 7/20/2020 1:08:08PM 4624 7/20/2020 1:08:00PM 4624 7/20/2020 1:08:08PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4663 7/20/2020 1:05:22PM 4660 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:18PM 4656 7/20/2020 1:05:14PM 4624 7/20/2020 1:04:59PM 4624 7/20/2020 1:04:59PM 5140 7/20/2020 1:04:44PM GROUP2-305\DIM-3055 GROUP2-305\DIM-3855 GROUP2-305\DIM-3055 GROUP2-305\DIH-3055 GROUP 2-35\DIM-3055 GROUP2-305\DIH 305$ GROUP2-305\DIM-395$ GROUP2-305\teacher2 GROUP2-385\teacher2 GROUP2-385\teacher2 GROUP2-305\teacher2 GROUP2-es teacher2 GROUP 2-305\teacher 2 GROUP2-305 \teacher2 GROUP 2-385 teacher2 GROUP2-385 VDTM-35$ GROUP 2-385\DIM-3055 GROUP2-305\teacher2 28 2 21 3 4 5 6 87 Ba 24 4 89 91 92 7 8 22 Output sample2 Eventbytte and Time 1/8/2019 8:23 1/8/2019 8:23 1/8/2019 3:23 1/8/2019 8:23 1/8/2019 8:23 1/8/2013 8:23 1/8/2019 823 w 1/8/2019 8:24 1/1/2019 824 1/8/2019 24 1/8/2019:24 to read the Event Write a Java program to read the Event ID, count how many events there are, collect the time the event was received, and collect the username, domain name, and the resource being accessed (which is indicated by the event logger ID) for a given login file and write into output file. See the sample output for an example. Make sure you do not hard code any part of the program-values, time, anything. It should all be interactive/live. When a user provides input, it should display the output in the output file. Here is a description of Event Logging: Windows Events provides a standard, centralized way for applications (and the operating system) to record important software and hardware events. The event-logging service stores events from various sources in a single collection called an event log. Prior to Windows Vista, you would use either Event Tracing for Windows (ETW) or Event Logging to log events. Windows Vista introduced a new eventing model that unifies both ETW and the Windows Event Log API. Event/Security Log Events The Event/Security log includes security-related events, especially those related to authentication and access. These logs are your best place to search for unauthorized access attempts to your system. https:/www.howtogeek.com/123646/htg-explains-what-the-windows-event-viewer-is-and-how-you- can-use-it/ Example Input file: we will still man e tutto Norte 1 word ES STIR Step 1: Filter the event log by the following events: 5140, 4660,4624, 4663,4656, 4659 OR Select other events. 3 / 6 100% + A OS 041 Step 2: Then save filtered event log as a tab delimited, text file called input_log.txt Make sure input file and this application is in the same folder. Outputs will be created in the same folder. Step3: Search by Event ID: 5140: A network share object was accessed 4624: An account was successfully logged on 4656: A handle to an object was requested 4659: A handle to an object was requested with intent to delete 4663: An attempt was made to access an object 4660: An object was deleted output_table full deg. Notepad File Format View Help 5140 7/20/2020 1:08:08PM 4624 7/29/2020 1:08:08PM 5140 7/20/2020 1:03:08PM 4624 7/20/2020 1:08:08PM 4624 7/20/2020 1:08:08PM 4624 7/20/2020 1:08:00PM 4624 7/20/2020 1:08:08PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4663 7/20/2020 1:05:22PM 4660 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:22PM 4656 7/20/2020 1:05:18PM 4656 7/20/2020 1:05:14PM 4624 7/20/2020 1:04:59PM 4624 7/20/2020 1:04:59PM 5140 7/20/2020 1:04:44PM GROUP2-305\DIM-3055 GROUP2-305\DIM-3855 GROUP2-305\DIM-3055 GROUP2-305\DIH-3055 GROUP 2-35\DIM-3055 GROUP2-305\DIH 305$ GROUP2-305\DIM-395$ GROUP2-305\teacher2 GROUP2-385\teacher2 GROUP2-385\teacher2 GROUP2-305\teacher2 GROUP2-es teacher2 GROUP 2-305\teacher 2 GROUP2-305 \teacher2 GROUP 2-385 teacher2 GROUP2-385 VDTM-35$ GROUP 2-385\DIM-3055 GROUP2-305\teacher2 28 2 21 3 4 5 6 87 Ba 24 4 89 91 92 7 8 22 Output sample2 Eventbytte and Time 1/8/2019 8:23 1/8/2019 8:23 1/8/2019 3:23 1/8/2019 8:23 1/8/2019 8:23 1/8/2013 8:23 1/8/2019 823 w 1/8/2019 8:24 1/1/2019 824 1/8/2019 24 1/8/2019:24