Answered step by step
Verified Expert Solution
Question
1 Approved Answer
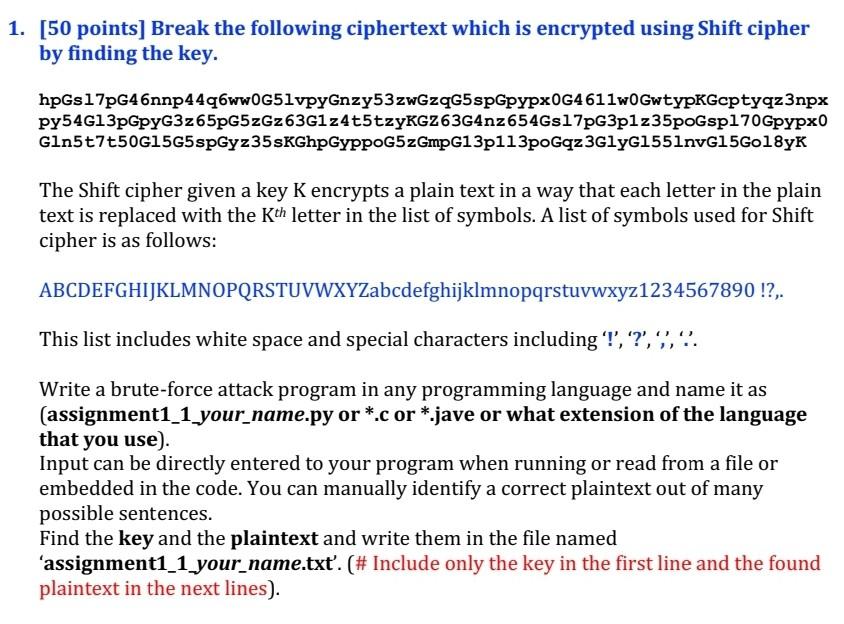
Write in Python please [50 points] Break the following ciphertext which is encrypted using Shift cipher by finding the key. hpGs17pG46nnp44q6ww0G51vpyGnzy53zwGzqG5spGpypx0G4611w0GwtypKGcptyqz3npx py54Gl3pGpyG3z65pG5zGz 63G1z4t5tzyKGz63G4nz654Gs17pG3p1z35poGspl70Gpypx0 Gln5t7t50Gl5G5spGyz35sKGhpGyppoG5zGmpG13p1l3poGqz3GlyGl55lnvGl5Gol8yK The
Write in Python please
[50 points] Break the following ciphertext which is encrypted using Shift cipher by finding the key. hpGs17pG46nnp44q6ww0G51vpyGnzy53zwGzqG5spGpypx0G4611w0GwtypKGcptyqz3npx py54Gl3pGpyG3z65pG5zGz 63G1z4t5tzyKGz63G4nz654Gs17pG3p1z35poGspl70Gpypx0 Gln5t7t50Gl5G5spGyz35sKGhpGyppoG5zGmpG13p1l3poGqz3GlyGl55lnvGl5Gol8yK The Shift cipher given a key K encrypts a plain text in a way that each letter in the plain text is replaced with the Kth letter in the list of symbols. A list of symbols used for Shift cipher is as follows: ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890 !?,. This list includes white space and special characters including '!', '?', ',, ' Write a brute-force attack program in any programming language and name it as that you use). Input can be directly entered to your program when running or read from a file or embedded in the code. You can manually identify a correct plaintext out of many possible sentences. Find the key and the plaintext and write them in the file named 'assignment1_1_your_name.txt'. (\# Include only the key in the first line and the found plaintext in the next lines)Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


