Write program classes in java that follow description:
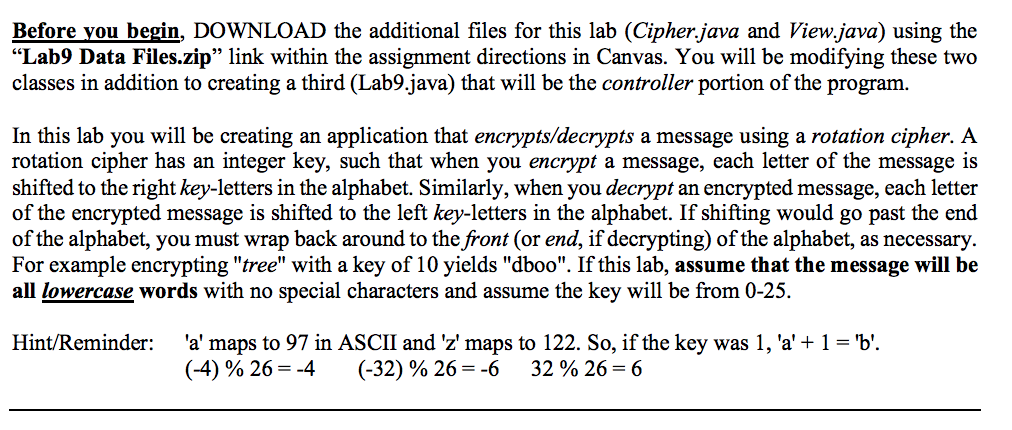
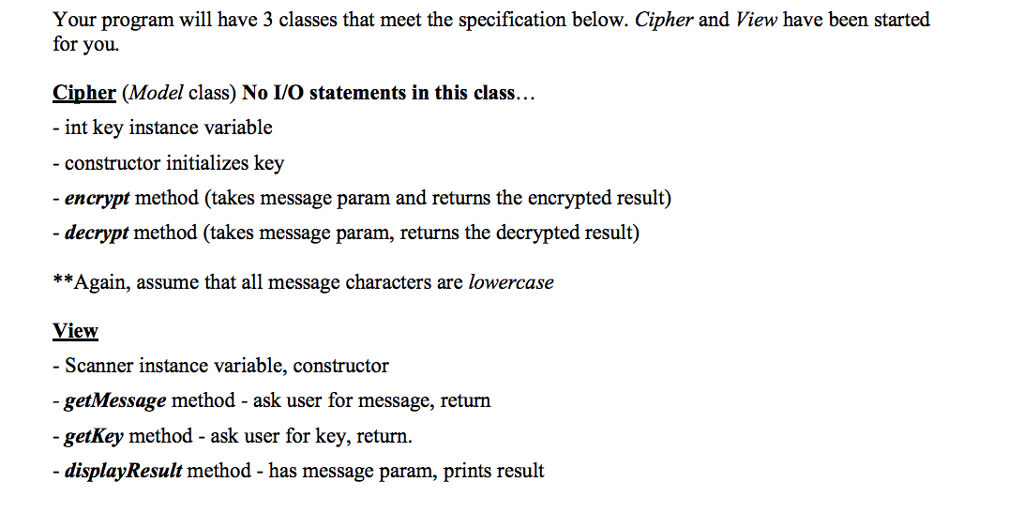
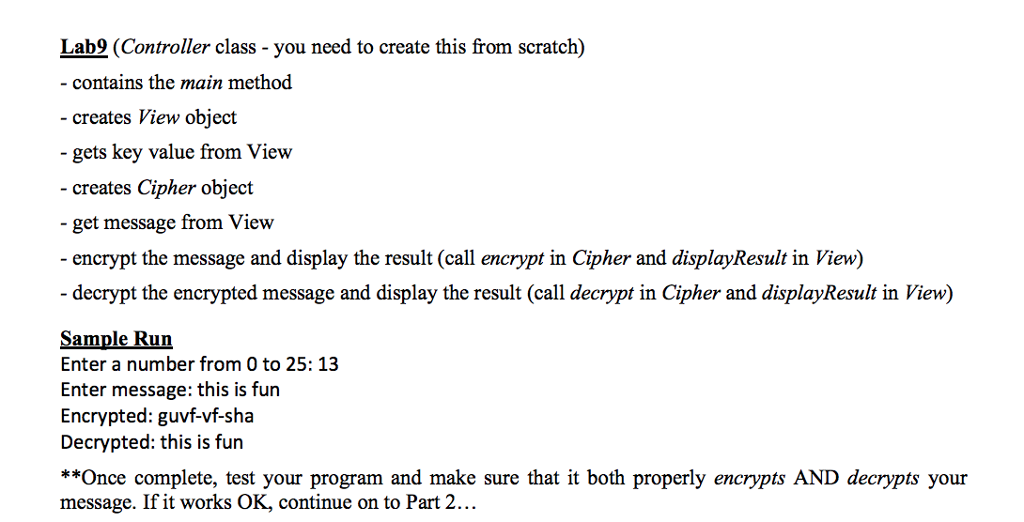
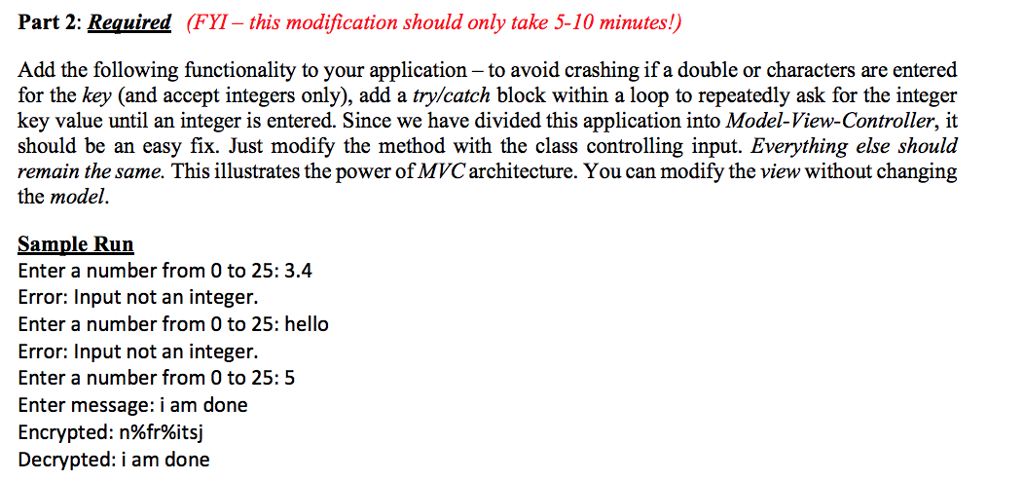
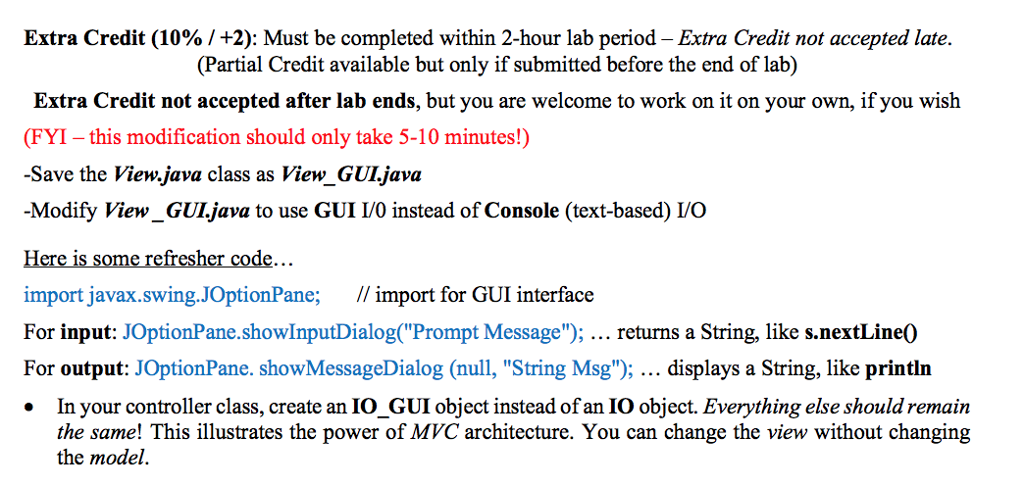
Before you begin, DOWNLOAD the additional files for this lab (Cipher.java and View.java) using the "Lab9 Data Files.zip" link within the assignment directions in Canvas. You will be modifying these two classes in addition to creating a third (Lab9.java) that will be the controller portion of the program. In this lab you will be creating an application that encrypts/decrypts a message using a rotation cipher. A rotation cipher has an integer key, such that when you encrypt a message, each letter of the message is shifted to the right key-letters in the alphabet. Similarly, when you decrypt an encrypted message, each letter of the encrypted message is shifted to the left key-letters in the alphabet. If shifting would go past the end of the alphabet, you must wrap back around to the front (or end, if decrypting) of the alphabet, as necessary. For example encrypting "tree" with a key of 10 yields "dboo". If this lab, assume that the message will be all lowercase words with no special characters and assume the key will be from 0-25. 'a' maps to 97 in ASCII and 'z' maps to 122. So, if the key was 1, 'a'+ 1-b' (4) % 26--4 Hint/Reminder: (-32) % 26--6 32 % 26-6 Before you begin, DOWNLOAD the additional files for this lab (Cipher.java and View.java) using the "Lab9 Data Files.zip" link within the assignment directions in Canvas. You will be modifying these two classes in addition to creating a third (Lab9.java) that will be the controller portion of the program. In this lab you will be creating an application that encrypts/decrypts a message using a rotation cipher. A rotation cipher has an integer key, such that when you encrypt a message, each letter of the message is shifted to the right key-letters in the alphabet. Similarly, when you decrypt an encrypted message, each letter of the encrypted message is shifted to the left key-letters in the alphabet. If shifting would go past the end of the alphabet, you must wrap back around to the front (or end, if decrypting) of the alphabet, as necessary. For example encrypting "tree" with a key of 10 yields "dboo". If this lab, assume that the message will be all lowercase words with no special characters and assume the key will be from 0-25. 'a' maps to 97 in ASCII and 'z' maps to 122. So, if the key was 1, 'a'+ 1-b' (4) % 26--4 Hint/Reminder: (-32) % 26--6 32 % 26-6











