Write this code in Java.

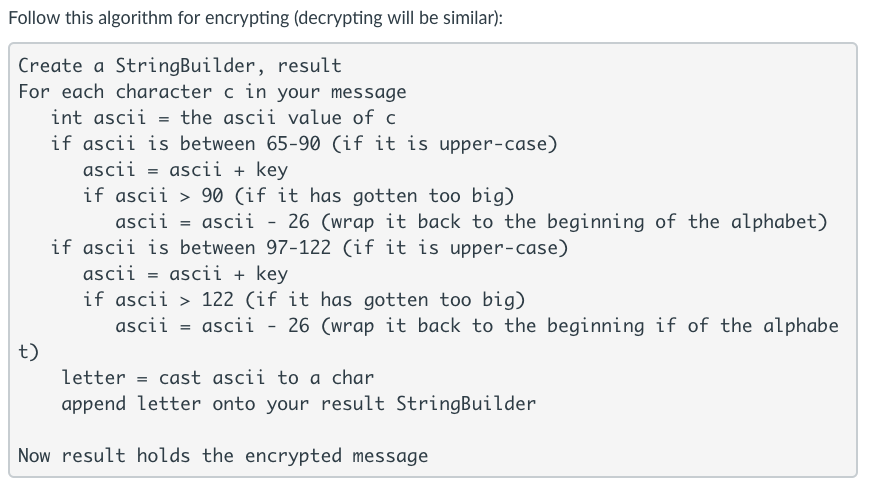
In this lab you will be making a program that encrypts/decrypts a message using a shift cipher. A shift cipher has an integer key, such that when you encrypt a message each letter of the message is shifted to the right key letters in the alphabet. Similarly, when you decrypt an encrypted message, each letter of the encrypted message is shifted to the left key letters in the alphabet. If shifting would go past the end of the alphabet, you should wrap back around to the front or end of the alphabet as necessary. For example encrypting "tree" with a key of 10 yields "dboo". You may assume that the message will be a single word (whose letters may be upper- OR lower-case) with no special characters Hint/Reminder: 'a' maps to 97 in ASCII and 'z' maps to 122. So, 'a' +1-'b A maps to 65, and 'Z' maps to 90 Your lab should have three classes that meet the specifications below Cipher int key field constructor initializes key encrypt method (takes a message as a parameter, and returns the encrypted result using the shift cipher) decrypt method (takes encrypted message as a parameter, and returns the decrypted result using the shift cipher) Again, you may assume that the messages are only alphabet characters (upper- or lower-case) View .Scanner field constructor initializes Scanner getMessage method- asks user for a message, and returns that message getKey method - asks user for a key (an int), and returns that key printResult method takes a String with either an encrypted or decrypted message as a parameter, and prints it to the screen Lab9 (contains the main method Write the code necessary to ask the user for a key and a message Encrypt the message with that key and print the result Decrypt the encrypted message with that key (to get back the original message) and print the result You will need to create Cipher and View objects to call their methods The main method should contains NO code for user input or printing that should be done by calling methods in View Hint: first create all three classes and the "shells of each methods (declared exactly as they appear above, but with no code in them). Do the Cipher class first, then the View, and finally the main method








