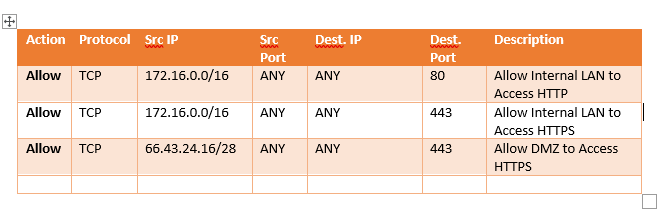
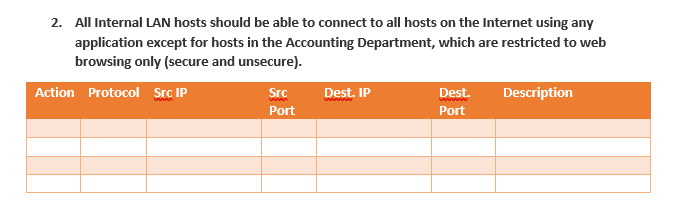
You are a network security officer who has finally convinced their company to buy a firewall to secure their network from Internet based threats. Your task is to create the rule list for this new firewall. You may make the following assumptions about this network: This will be a Triple-homed firewall with one interface connected to the Internal LAN zone, another connected to the Internet zone, and the final interface connected to a DMZ. The firewall's three IPs will be: Internal - 172.16.255.1, External - 66.43.24.1, DMZ- 66.43.24.17 The company operates a DMZ for their online services in the 66.43.24.16/28 subnet. There is an internal server farm occupying the 172.16.100.0/24 subnet. The web development team occupies the 172.16.50.0/24 subnet. The accounting department occupies the 172.16.20.0/24 and 172.16.21.0/24 subnets. Remote access users use the 172.16.10.0/24 subnet. Two business partners, ACME and Fredco, connect to the company through dedicated circuits; they use the 192.168.100.0/24 and 192.168.200.0/24 subnets respectively. The firewall is stateful and should exercise a deny-by-default policy. Your boss, the head of network security and the author of the company's security policy, has given you directives for how the traffic should be allowed to flow through this network. It is your task to translate these directives into an efficient firewall policy. For each of the directive, create firewall rules to allow only the desired traffic. Create the rules to be specific and keep in mind each directive may require more than one rule. Example: Hosts on the internal LAN should be able to connect to web servers on the Internet but hosts on the DMZ should only be allowed to connect using SSL. Action Protocol Src IP Dest. IP Dest. Description Src Port ANY Port 80 Allow TCP 172.16.0.0/16 ANY Allow TCP 172.16.0.0/16 ANY ANY 443 Allow Internal LAN to Access HTTP Allow Internal LAN to Access HTTPS Allow DMZ to Access HTTPS Allow TCP 66.43.24.16/28 ANY ANY 443 2. All Internal LAN hosts should be able to connect to all hosts on the Internet using any application except for hosts in the Accounting Department, which are restricted to web browsing only (secure and unsecure). Action Protocol Src IP Src Dest. IP Dest. Description Port Port You are a network security officer who has finally convinced their company to buy a firewall to secure their network from Internet based threats. Your task is to create the rule list for this new firewall. You may make the following assumptions about this network: This will be a Triple-homed firewall with one interface connected to the Internal LAN zone, another connected to the Internet zone, and the final interface connected to a DMZ. The firewall's three IPs will be: Internal - 172.16.255.1, External - 66.43.24.1, DMZ- 66.43.24.17 The company operates a DMZ for their online services in the 66.43.24.16/28 subnet. There is an internal server farm occupying the 172.16.100.0/24 subnet. The web development team occupies the 172.16.50.0/24 subnet. The accounting department occupies the 172.16.20.0/24 and 172.16.21.0/24 subnets. Remote access users use the 172.16.10.0/24 subnet. Two business partners, ACME and Fredco, connect to the company through dedicated circuits; they use the 192.168.100.0/24 and 192.168.200.0/24 subnets respectively. The firewall is stateful and should exercise a deny-by-default policy. Your boss, the head of network security and the author of the company's security policy, has given you directives for how the traffic should be allowed to flow through this network. It is your task to translate these directives into an efficient firewall policy. For each of the directive, create firewall rules to allow only the desired traffic. Create the rules to be specific and keep in mind each directive may require more than one rule. Example: Hosts on the internal LAN should be able to connect to web servers on the Internet but hosts on the DMZ should only be allowed to connect using SSL. Action Protocol Src IP Dest. IP Dest. Description Src Port ANY Port 80 Allow TCP 172.16.0.0/16 ANY Allow TCP 172.16.0.0/16 ANY ANY 443 Allow Internal LAN to Access HTTP Allow Internal LAN to Access HTTPS Allow DMZ to Access HTTPS Allow TCP 66.43.24.16/28 ANY ANY 443 2. All Internal LAN hosts should be able to connect to all hosts on the Internet using any application except for hosts in the Accounting Department, which are restricted to web browsing only (secure and unsecure). Action Protocol Src IP Src Dest. IP Dest. Description Port Port









