You have learned how to Launch a DoS attack on Web Server. Complete the Incident Response form. You habve to fill this form assuming the DoS attack Also suggest DoS prevention techniques in this IR Form .
in this format:
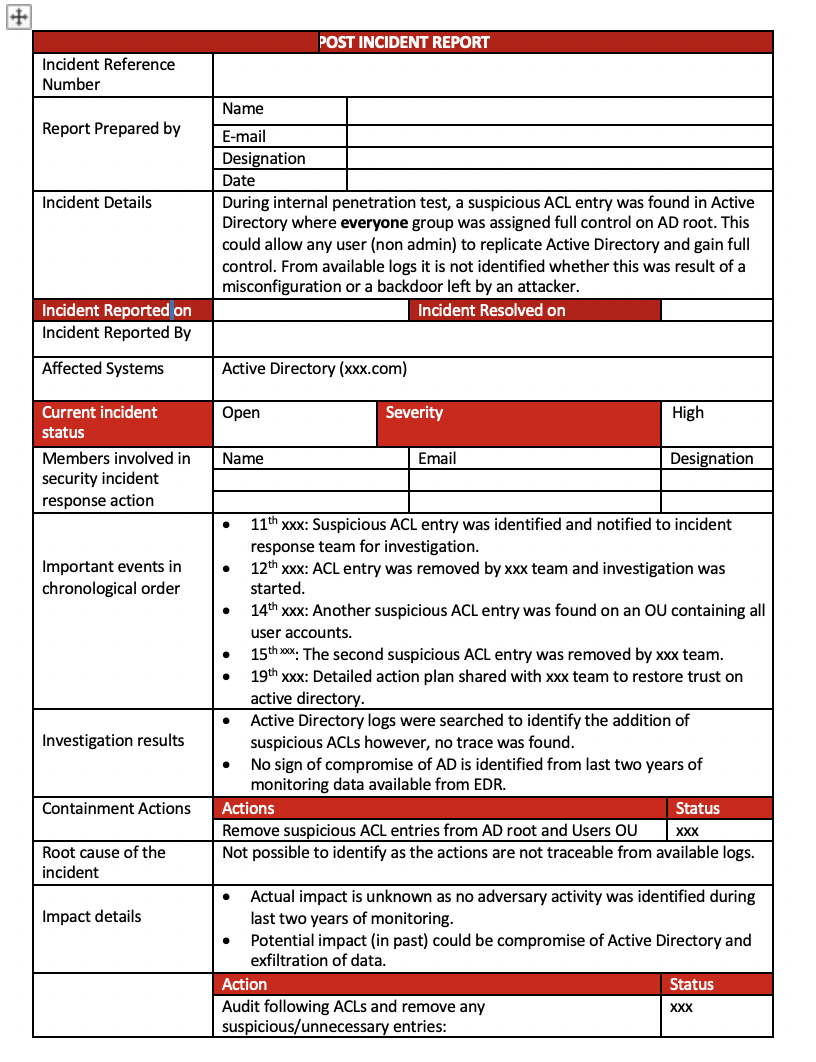
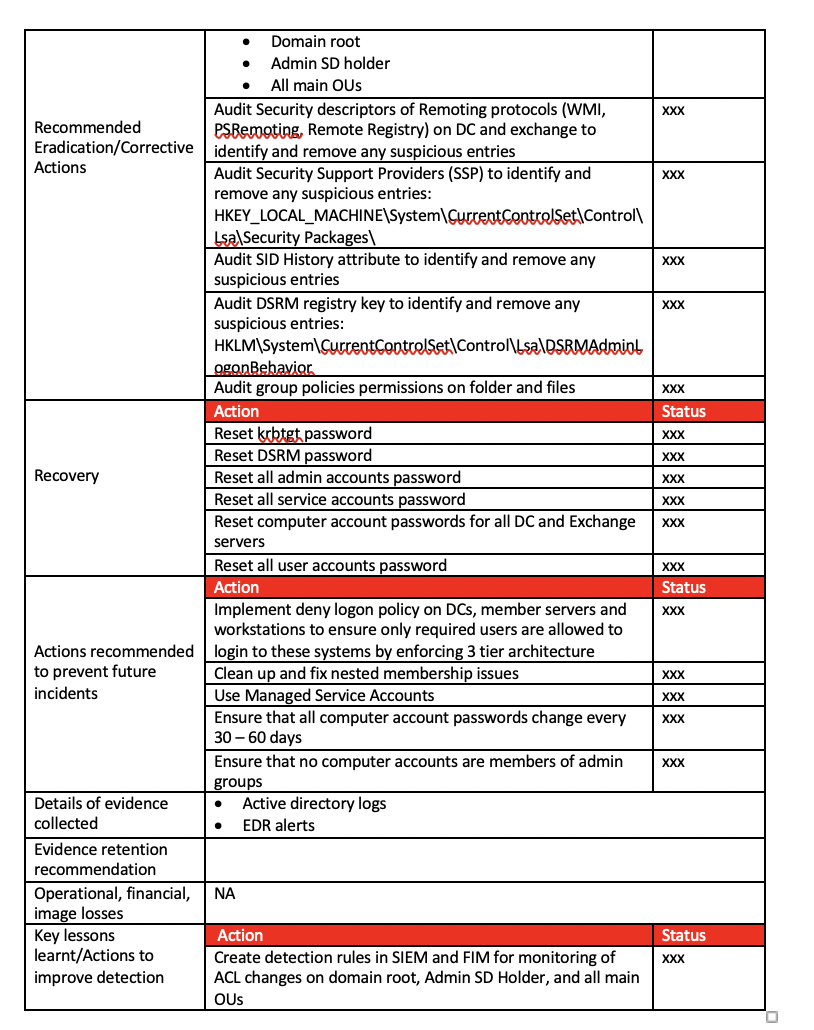
POST INCIDENT REPORT Incident Reference Number Name Report Prepared by Incident Details E-mail Designation Date During internal penetration test, a suspicious ACL entry was found in Active Directory where everyone group was assigned full control on AD root. This could allow any user (non admin) to replicate Active Directory and gain full control. From available logs it is not identified whether this was result of a misconfiguration or a backdoor left by an attacker. Incident Resolved on Incident Reported on Incident Reported By Affected Systems Active Directory (xxx.com) Open Severity High Current incident status Members involved in security incident response action Name Email Designation Important events in chronological order . 11th xxx: Suspicious ACL entry was identified and notified to incident response team for investigation. 12th xxx: ACL entry was removed by xxx team and investigation was started. 14th xxx: Another suspicious ACL entry was found on an OU containing all user accounts. 15th ox. The second suspicious ACL entry was removed by xxx team. 19th xxx: Detailed action plan shared with xxx team to restore trust on active directory. Active Directory logs were searched to identify the addition of suspicious ACLs however, no trace was found. No sign of compromise of AD is identified from last two years of monitoring data available from EDR. Actions Status Remove suspicious ACL entries from AD root and Users OU XXX Not possible to identify as the actions are not traceable from available logs. . Investigation results Containment Actions Root cause of the incident . Impact details . Actual impact is unknown as no adversary activity was identified during last two years of monitoring. Potential impact (in past) could be compromise of Active Directory and exfiltration of data. Action Status Audit following ACLs and remove any XXX suspicious/unnecessary entries: . XXX XXX XXX Domain root Admin SD holder All main OUS Audit Security descriptors of Remoting protocols (WMI, Recommended PSRemoting, Remote Registry) on DC and exchange to Eradication/Corrective identify and remove any suspicious entries Actions Audit Security Support Providers (SSP) to identify and remove any suspicious entries: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control Lsa\Security Packages Audit SID History attribute to identify and remove any suspicious entries Audit DSRM registry key to identify and remove any suspicious entries: HKLM\System\CurrentControlSet\Control\lsa\DSRMAdmin! ogonBehavior. Audit group policies permissions on folder and files Action Reset krbtgt password Reset DSRM password Recovery Reset all admin accounts password Reset all service accounts password Reset computer account passwords for all DC and Exchange servers Reset all user accounts password XXX XXX Status XXX XXX XXX XXX XXX Action XXX Status XXX XXX XXX XXX Implement deny logon policy on DCs, member servers and workstations to ensure only required users are allowed to Actions recommended login to these systems by enforcing 3 tier architecture to prevent future Clean up and fix nested membership issues incidents Use Managed Service Accounts Ensure that all computer account passwords change every 30-60 days Ensure that no computer accounts are members of admin groups Details of evidence Active directory logs collected EDR alerts Evidence retention recommendation Operational, financial, NA image losses Key lessons Action learnt/Actions to Create detection rules in SIEM and FIM for monitoring of improve detection ACL changes on domain root, Admin SD Holder, and all main OUS . Status XXX POST INCIDENT REPORT Incident Reference Number Name Report Prepared by Incident Details E-mail Designation Date During internal penetration test, a suspicious ACL entry was found in Active Directory where everyone group was assigned full control on AD root. This could allow any user (non admin) to replicate Active Directory and gain full control. From available logs it is not identified whether this was result of a misconfiguration or a backdoor left by an attacker. Incident Resolved on Incident Reported on Incident Reported By Affected Systems Active Directory (xxx.com) Open Severity High Current incident status Members involved in security incident response action Name Email Designation Important events in chronological order . 11th xxx: Suspicious ACL entry was identified and notified to incident response team for investigation. 12th xxx: ACL entry was removed by xxx team and investigation was started. 14th xxx: Another suspicious ACL entry was found on an OU containing all user accounts. 15th ox. The second suspicious ACL entry was removed by xxx team. 19th xxx: Detailed action plan shared with xxx team to restore trust on active directory. Active Directory logs were searched to identify the addition of suspicious ACLs however, no trace was found. No sign of compromise of AD is identified from last two years of monitoring data available from EDR. Actions Status Remove suspicious ACL entries from AD root and Users OU XXX Not possible to identify as the actions are not traceable from available logs. . Investigation results Containment Actions Root cause of the incident . Impact details . Actual impact is unknown as no adversary activity was identified during last two years of monitoring. Potential impact (in past) could be compromise of Active Directory and exfiltration of data. Action Status Audit following ACLs and remove any XXX suspicious/unnecessary entries: . XXX XXX XXX Domain root Admin SD holder All main OUS Audit Security descriptors of Remoting protocols (WMI, Recommended PSRemoting, Remote Registry) on DC and exchange to Eradication/Corrective identify and remove any suspicious entries Actions Audit Security Support Providers (SSP) to identify and remove any suspicious entries: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control Lsa\Security Packages Audit SID History attribute to identify and remove any suspicious entries Audit DSRM registry key to identify and remove any suspicious entries: HKLM\System\CurrentControlSet\Control\lsa\DSRMAdmin! ogonBehavior. Audit group policies permissions on folder and files Action Reset krbtgt password Reset DSRM password Recovery Reset all admin accounts password Reset all service accounts password Reset computer account passwords for all DC and Exchange servers Reset all user accounts password XXX XXX Status XXX XXX XXX XXX XXX Action XXX Status XXX XXX XXX XXX Implement deny logon policy on DCs, member servers and workstations to ensure only required users are allowed to Actions recommended login to these systems by enforcing 3 tier architecture to prevent future Clean up and fix nested membership issues incidents Use Managed Service Accounts Ensure that all computer account passwords change every 30-60 days Ensure that no computer accounts are members of admin groups Details of evidence Active directory logs collected EDR alerts Evidence retention recommendation Operational, financial, NA image losses Key lessons Action learnt/Actions to Create detection rules in SIEM and FIM for monitoring of improve detection ACL changes on domain root, Admin SD Holder, and all main OUS . Status XXX








