Question: Consider our authentication protocol in Figure 8.18 in which Alice authenticates herself to Bob, which we saw works well (i.e., we found no flaws in
Consider our authentication protocol in Figure 8.18 in which Alice authenticates herself to Bob, which we saw works well (i.e., we found no flaws in hi. Now suppose that while Alice is authenticating herself to Bob, Bob must authenticate himself lo Alice. Give a scenario by which Tiudy, pretending to be Alice, can now authenticate herself to Bob as Alice. (Consider that the sequence of operations of the protocol, one with Trudy initiating and one with Bob initiating, can be arbitrarily interleaved. Pay particular attention to the fact that both Bob and Alice will use a nonce, and that if care is not taken, the same nonce can be used maliciously.)
Figure 8.18
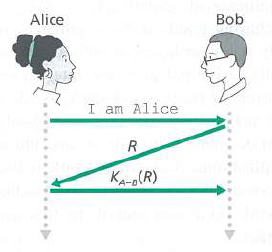
Alice Bob I am Alice KA-e(R)
Step by Step Solution
3.33 Rating (165 Votes )
There are 3 Steps involved in it
Bob does not know if he is talking to Trudy or Alice initially Bob and Alice share a secret key K AB ... View full answer

Get step-by-step solutions from verified subject matter experts


