Question: Figure 8.19 shows tie operations that Alice must perform with POP to provide confidentiality, authentication, and integrity. Diagram the corresponding operations that Bob mat perform
Figure 8.19 shows tie operations that Alice must perform with POP to provide confidentiality, authentication, and integrity. Diagram the corresponding operations that Bob mat perform on the package received from Alice.
Figure 8.19
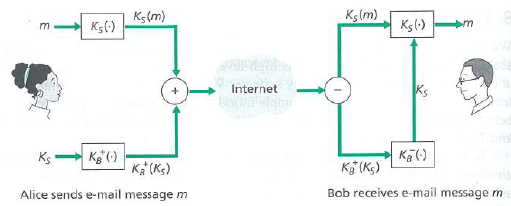
Klm) Kg(m) K5() Ksl) Internet Kg () Ks Kg (Ks) Ka (KG) Bob receives e-mail message m Alice sends e-mail message m
Step by Step Solution
3.54 Rating (168 Votes )
There are 3 Steps involved in it
Figure Operations performed b... View full answer

Get step-by-step solutions from verified subject matter experts


