Computer Systems A Programmers Perspective 3rd Global Edition Randal E. Bryant, David R. O'Hallaron - Solutions
Unlock a wealth of knowledge with our comprehensive resources for "Computer Systems: A Programmer's Perspective, 3rd Global Edition" by Randal E. Bryant and David R. O'Hallaron. Dive into our online platform offering answers and a detailed solution manual to enhance your understanding. Access solutions in PDF format for solved problems, and explore questions and answers curated from the textbook. Our test bank and chapter solutions provide step-by-step answers, ideal for students and instructors alike. Benefit from the instructor manual and enjoy the convenience of a free download, bringing textbook insights right to your fingertips.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()


![Element x [0] x [1] x [2] x [3] x [4] x [5] x [6] x [7] Address 0 4 8 12 16 20 24 28 Set index 0 0 0 0 1 1 1](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/9/8/3/047659ffa07e67541704983047277.jpg)
![int short int double short P[5]; Q[2]; **R [9]; *S [10]; *T [2] ;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/3/48865379d0073bbf1698143485697.jpg)
![typedef union { struct { long u; short v; char W; } t1; struct { } int a [2]; char *p: } t2; } u_type; You](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/4/4416537a0b9d0e1e1698144439823.jpg)


![&D[i][j] = xD + L(C.i+j) (3.1)](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/3/97065379ee25355c1698143968459.jpg)
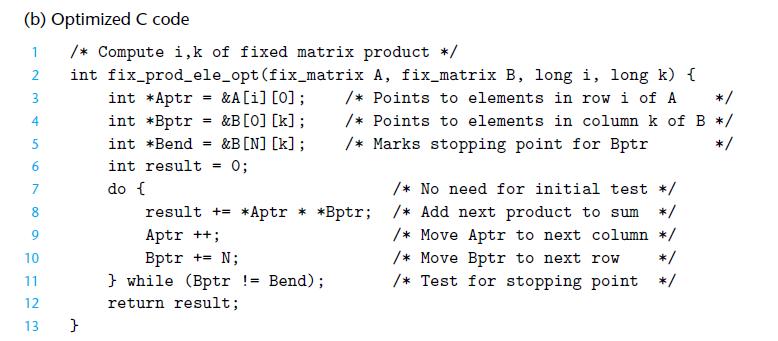
![long P [M] [N]; long Q[N] [M]; long sum_element (long i, long j) { return P[i] [j] + Q[j] [i]; }](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/3/68565379dc5bc9851698143684260.jpg)
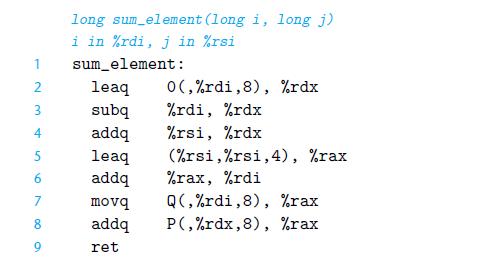
![Expression P[1] P + 3 + i P[i* 6-5] P[2] &P [i+ 2] Type Value Assembly code](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/3/62665379d8a21ec31698143624463.jpg)
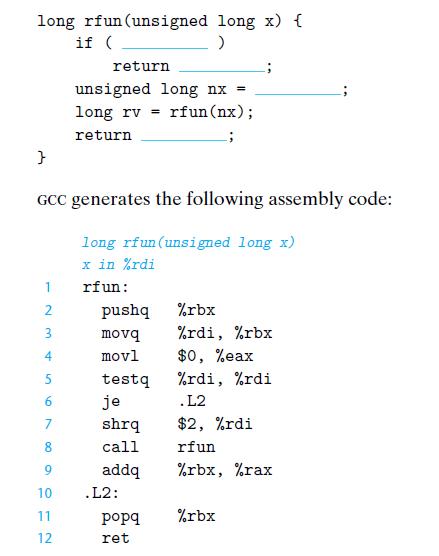
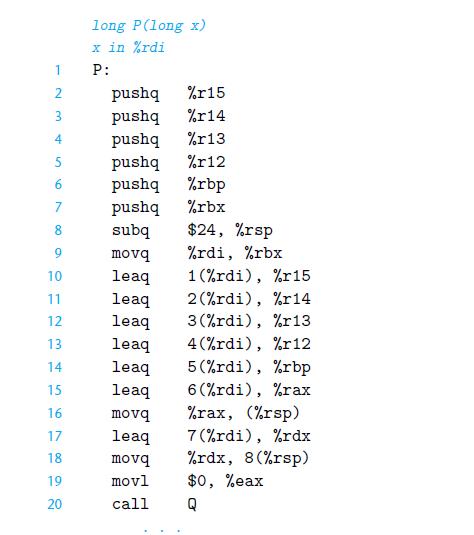

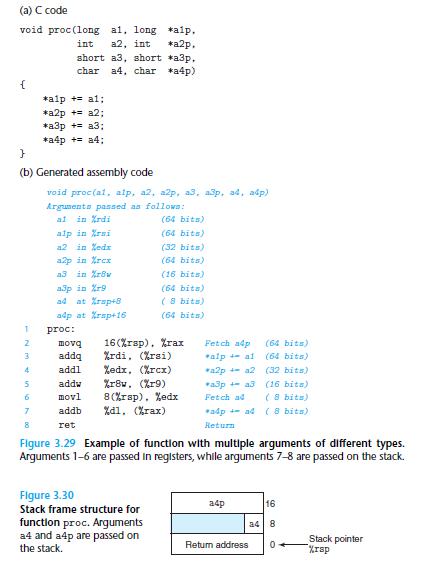
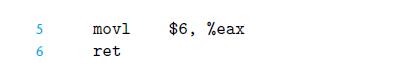
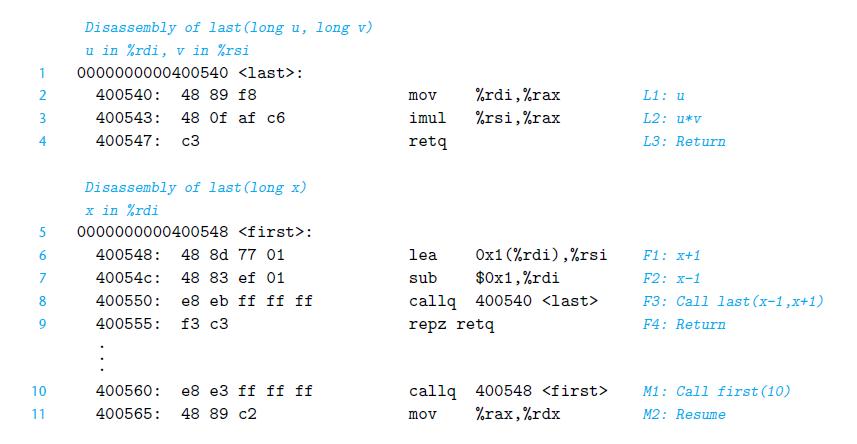
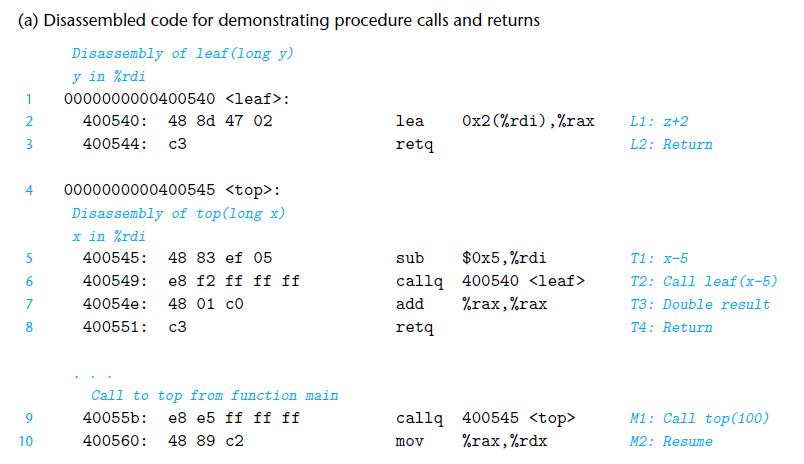
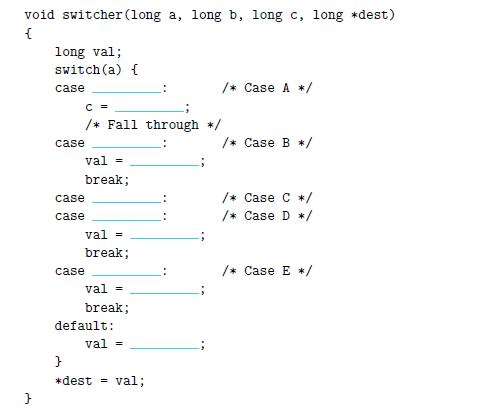
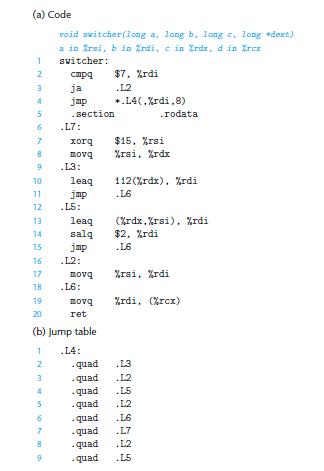
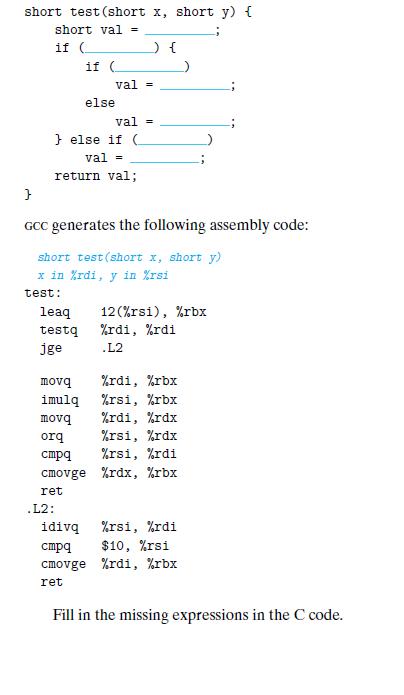
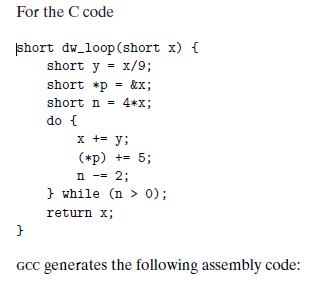
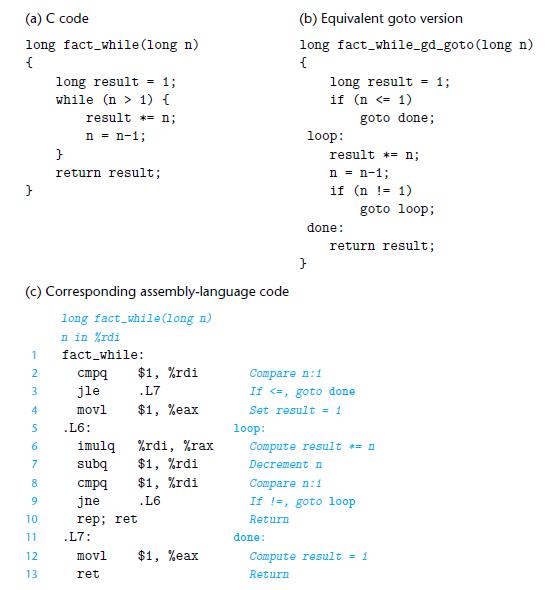
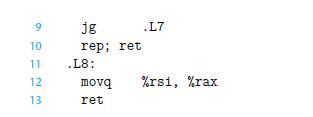
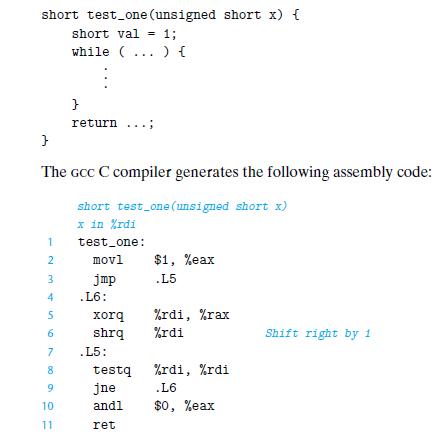
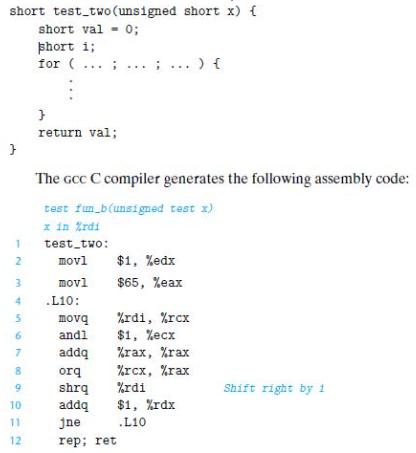
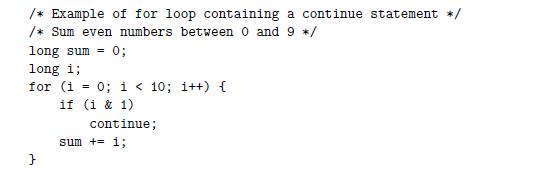

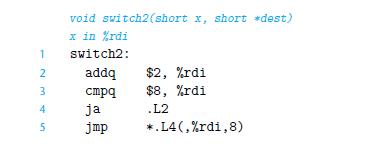

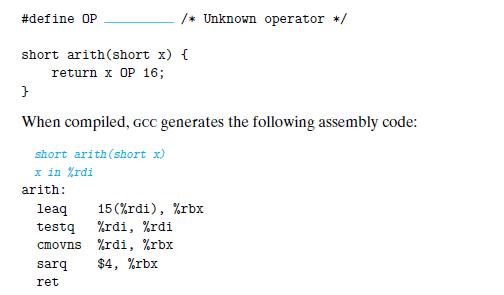
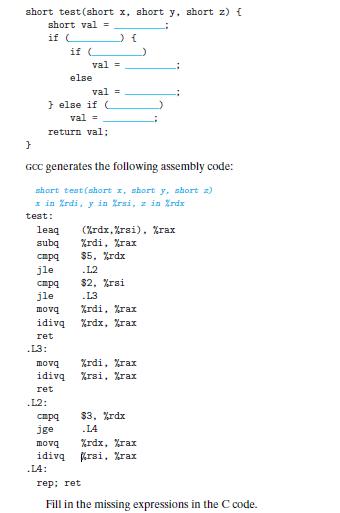

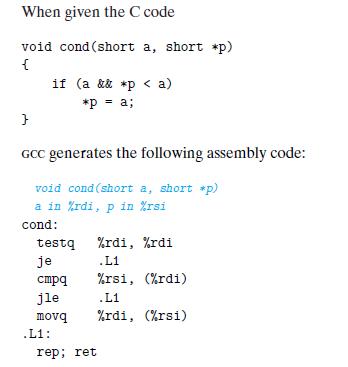
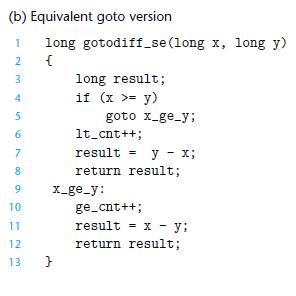



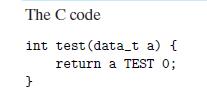

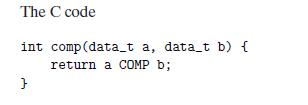




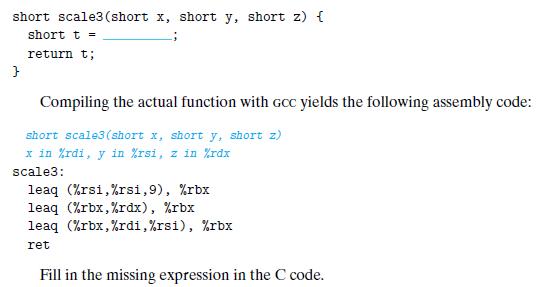
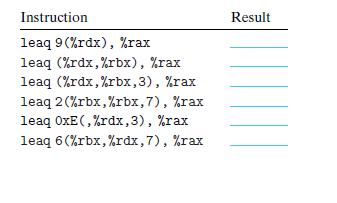
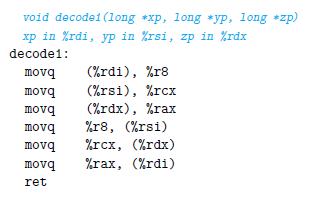
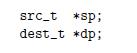
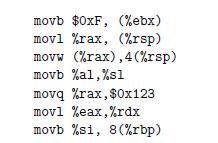
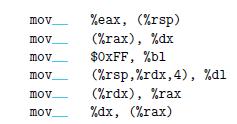
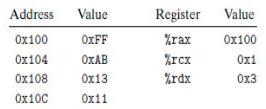
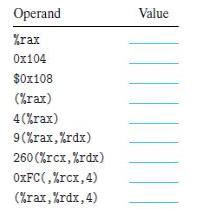

![1 2 3 void reverse_array(int a[], int cnt) { int first, last; for (first 0, last cnt-1; = first < last;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/2/91165374c9f749fb1698122909897.jpg)
![Mode Unsigned Two's complement Unsigned Two's complement Unsigned Two's complement [100] [100] [010] [010]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/8/099653760e321151Untitled.png)
![Mode Unsigned Two's complement Unsigned Two's complement Unsigned Two's complement X [101] 5 -3 [101] 4 [100]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/8/128653761009c7791698128127120.jpg)

![x Hexadecimal Binary OXA [1010] 0x1 OxB 0x2 0x7 0xC B2U4(x) 2 +2=10 B2T4(x) -2 +2=-6](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/5/2146537559e250f61698125212603.jpg)
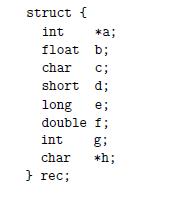
![A. struct P1 { short i; int c; int *j; short *d; }; B. struct P2 { int i[2]; char c [8]; short s [4]; long](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/4/4/5956537a153509931698144593144.jpg)
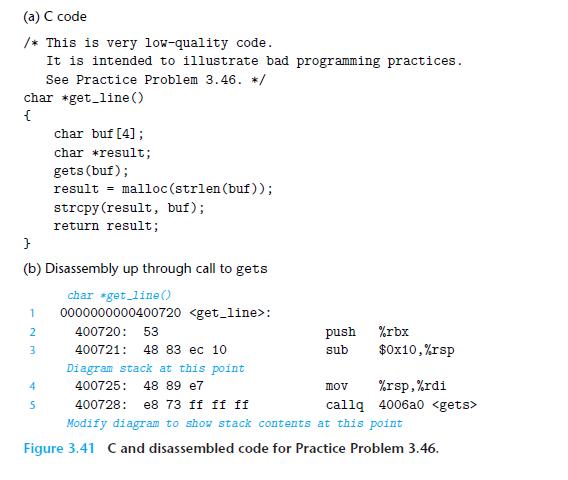
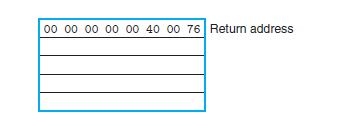
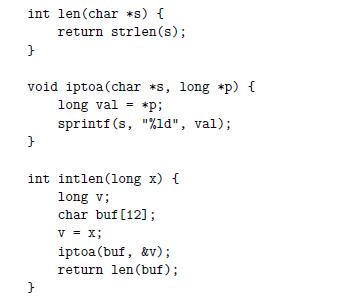

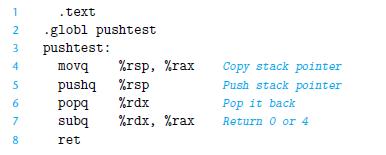
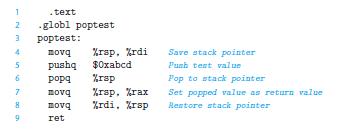
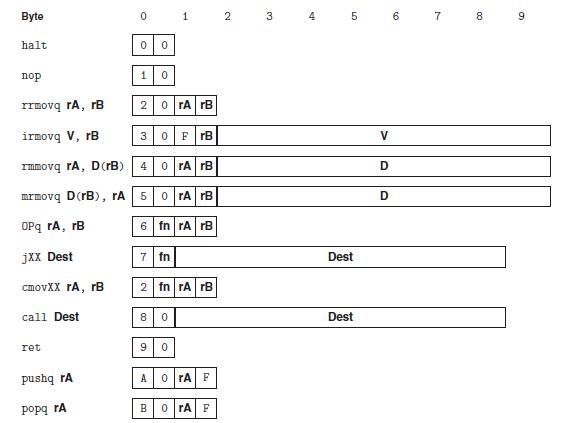
![Stage Fetch Decode Execute Memory Write back PC update cmovXX rA, rB + icode: ifun M [PC] rA:rB M[PC + 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/0/0936538a12d7b4bf1698210092483.jpg)
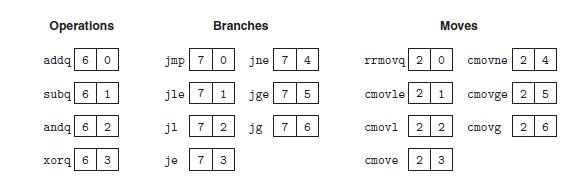
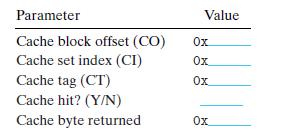
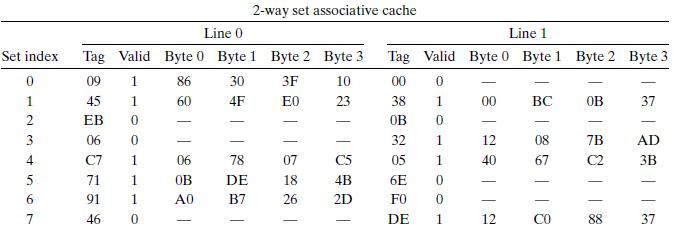
![Stage Fetch Stage Decode Execute Generic call Dest icode:ifun M [PC] valC Mg[PC +1] valP - PC +9 Generic](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/0/2876538a1ef126efUntitled.png)
![Stage Fetch Decode Execute Memory Write back PC update OPq rA, rB icode: ifun rA:B M [PC] M [PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/0/9066538a45a621c91698210905153.jpg)
![Stage Fetch Decode Execute Memory Write back PC update jXX Dest icode: ifun - M[PC] valC+ Mg[PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/0/9276538a46fc07be1698210926742.jpg)


![Stage Fetch Generic popq rA icode:ifun rA:rB M[PC] M [PC + 1] valp PC +2 Specific popq %rax](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/0/9/55565389f1368d051698209554466.jpg)
![Stage Fetch Decode Execute Generic irmov V, rB icode: ifun M [PC] rA:rB M[PC + 1] valC+ Mg[PC + 2] valp PC+](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/0/9/47665389ec4628e91698209475450.jpg)
![Stage Fetch Decode Execute Memory Write back PC update OPq rA, rB icode: ifun + M [PC] rA:rB M [PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/2216538a59575f5f1698211220407.jpg)
![Stage Fetch Decode Execute Memory Write back PC update jXX Dest icode: ifun M [PC] valC+ valp PC+9 Mg[PC + 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/2006538a5801ac401698211199072.jpg)
![Stage Fetch Decode Execute Memory Write back PC update OPq rA, rB icode: ifun rA:B M [PC] M [PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/6726538a758876ea1698211671258.jpg)
![Stage Fetch Decode Execute Memory Write back PC update jXX Dest icode: ifun - M[PC] valC+ Mg[PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/5466538a6daa3d811698211545402.jpg)
![Stage Fetch Decode Execute Memory Write back PC update OPq rA, rB icode: ifun rA:B M [PC] M [PC + 1] valp](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/9446538a86857a9f1698211943205.jpg)
![Stage Fetch Decode Execute Memory Write back PC update JXX Dest icode: ifun M[PC] valc Mg[PC + 1] valp PC +9](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/1/9286538a858e1bc71698211927596.jpg)