Question: Suppose that all the switches in Figure 6.15 are replaced by hubs. All links are 100 Mbps. Now answer the questions posed in problem P23.
Suppose that all the switches in Figure 6.15 are replaced by hubs. All links are 100 Mbps. Now answer the questions posed in problem P23.
Data From Problem 6.23
Consider Figure 6.15. Suppose that all links arc loo Mbps. What is the maximum total aggregate throughput that can be achieved among the 9 hosts and 2 servers in this network? You can assume that any host or server can send to any other host or server. Why?
Figure 6.15
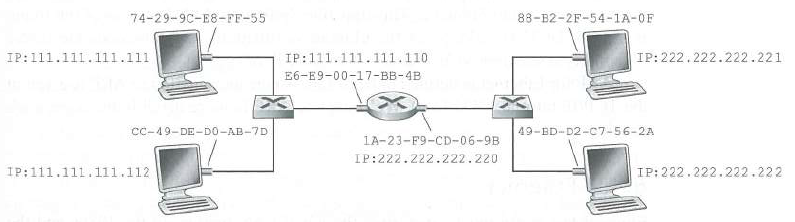
74-29-9C-E8-FF-55 88-B2-2F-54-1A-OF IP:111.111.1l1.111 IP:111.111.111.110 E6-E9-00-17-BB-4B IP:222.222.222.221 CC-49-DE-DO-AB-7D 1A-23-F9-CD-06-9B 49-BD-D2-C7-56-2A IP:222.222.222.220 IP:111.111.111.112 IP:222.222.222.222
Step by Step Solution
3.46 Rating (166 Votes )
There are 3 Steps involved in it
All of the 11 end systems will l... View full answer

Get step-by-step solutions from verified subject matter experts


