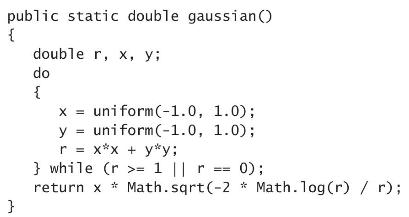
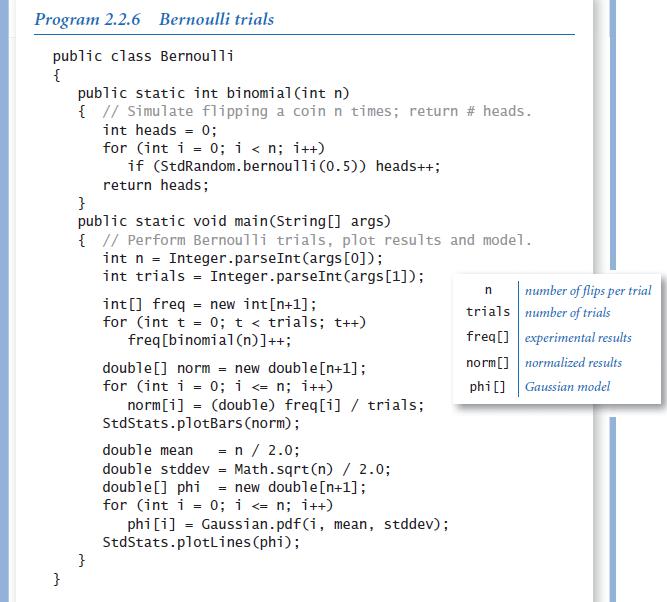
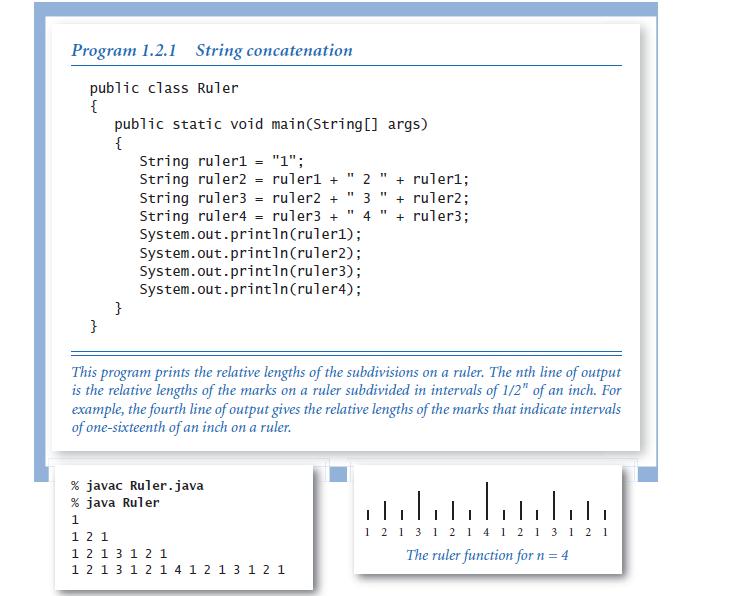
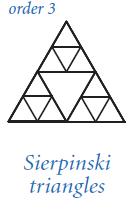Introduction To Programming In Java An Interdisciplinary Approach 2nd Edition Robert Sedgewick, Kevin Wayne - Solutions
Discover comprehensive solutions for "Introduction To Programming In Java: An Interdisciplinary Approach, 2nd Edition" by Robert Sedgewick and Kevin Wayne. Unlock a wealth of resources including answers key, solutions manual, and step-by-step answers to enhance your understanding. Explore solved problems and chapter solutions to deepen your grasp of programming concepts. Access the instructor manual and test bank to guide your learning journey. Our platform offers free download options for solutions PDFs, providing textbook solutions that cater to your academic needs. Dive into questions and answers tailored for students and educators alike, ensuring a thorough comprehension of programming principles.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()