![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()


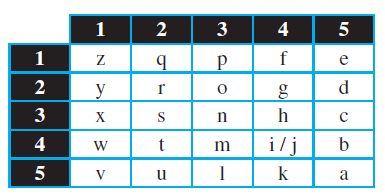
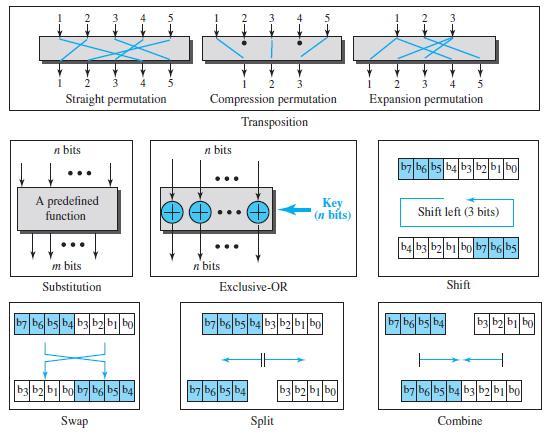
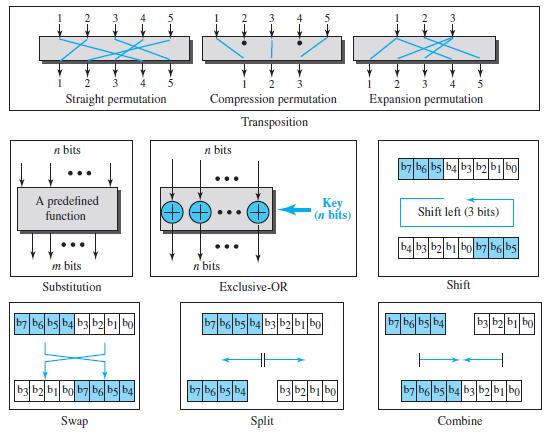
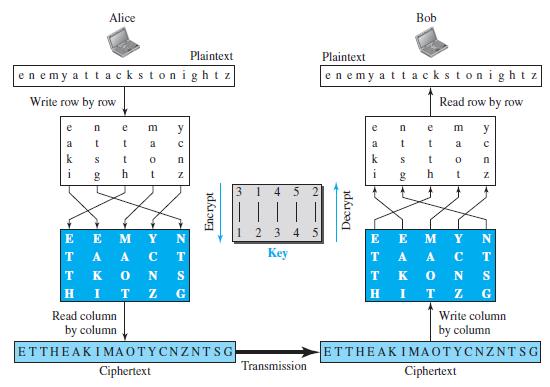
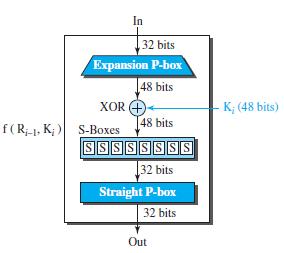
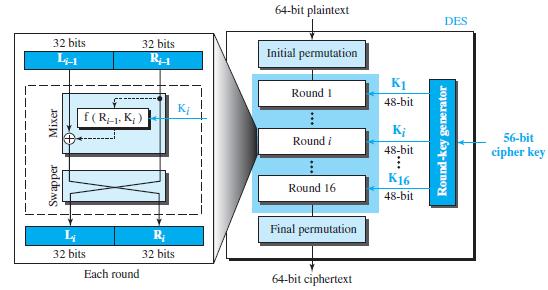
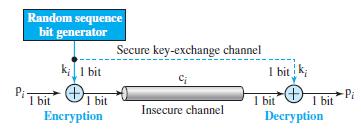
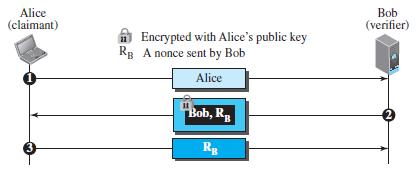
![Figure 31.17 Message authentication code Alice Bob M: Message K: A shared secret key MAC: Message authentication code K K МАС МАС Hash Hash Same?0 [no] M+ MAC Discard M + MAC Insecure channel M+ MAC [yes] Keep the message](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1607/4/9/7/0365fd0754c893c11607497036021.jpg)