![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()



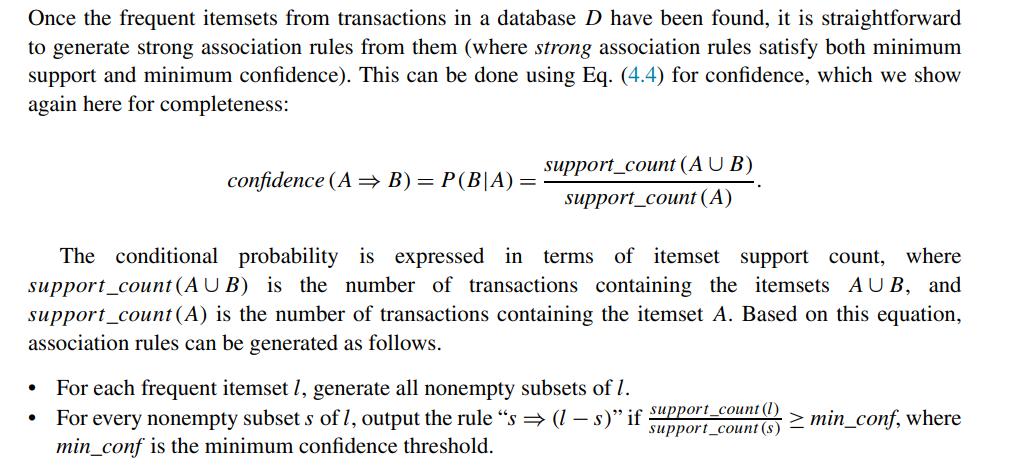
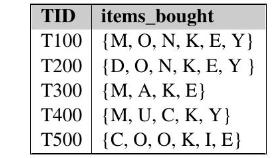

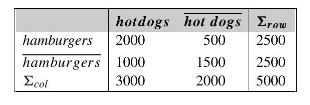
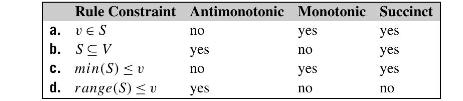
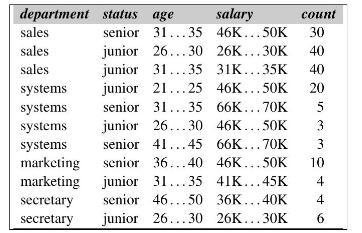
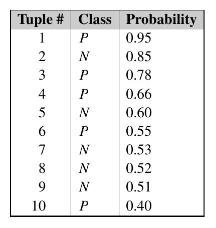
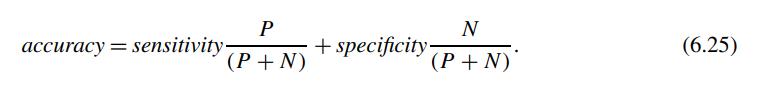
![H = || *] _i=l 72 1 12](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1705/5/8/2/98465a921880a70e1705582982622.jpg)