Consider a one-way authentication technique based on asymmetric encryption: a. Explain the protocol. b. What type of
Question:
Consider a one-way authentication technique based on asymmetric encryption: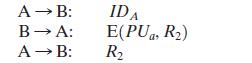
a. Explain the protocol.
b. What type of attack is this protocol susceptible to?
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Related Book For 

Question Posted:





