Consider a one-way authentication technique based on asymmetric encryption: a. Explain the protocol. b. What type of
Question:
Consider a one-way authentication technique based on asymmetric encryption: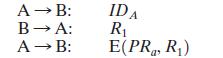
a. Explain the protocol.
b. What type of attack is this protocol susceptible to?
Transcribed Image Text:
A B: B A: A B: IDA R E(PR, R)
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 100% (2 reviews)
a This is a means of authenticating A to B R 1 serves as a challenge and only ...View the full answer

Answered By

PALASH JHANWAR
I am a Chartered Accountant with AIR 45 in CA - IPCC. I am a Merit Holder ( B.Com ). The following is my educational details.
PLEASE ACCESS MY RESUME FROM THE FOLLOWING LINK: https://drive.google.com/file/d/1hYR1uch-ff6MRC_cDB07K6VqY9kQ3SFL/view?usp=sharing
3.80+
3+ Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Consider a one-way authentication technique based on asymmetric encryption: a. Explain the protocol. b. What type of attack is this protocol susceptible to? A B: B A: A B: IDA E(PUa, R) R
-
1. Describe each of the following four kinds of access control mechanisms in terms of (a) ease of determining authorized access during execution, (b) ease of adding access for a new subject, (c) ease...
-
1- Describe each of the following four kinds of access control mechanisms in terms of a- Ease of determining authorized access during execution, b- Ease of adding access for a new subject, c- Ease of...
-
What is the square root of 3 to the square root of 2 power times the square root of 3 to the negative square root of 2 power?
-
To refresh air in a room, a counter flow heat exchanger, is mounted in the wall, drawing in outside air at 0.5C, 80% relative humidity and pushing out room air, 40C, 50% relative...
-
differentiate among the ethical models,
-
1. What are the characteristics of a partnership?
-
At the beginning of the current period, Huang Co. had a balance of $100,000 in Accounts Receivable and a $7,000 credit balance in Allowance for Doubtful Accounts. In the period, it had net credit...
-
c In 2023, Mercedes exchanged a parcel of Land ( $75,000 Fair Market Value and Adjusted Basis of $30,000) for forty percent (40\%) interest in a Partnership. The Partnership uses the Land in its...
-
In Kerberos, when Bob receives a Ticket from Alice, how does he know it is genuine?
-
In addition to providing a standard for public-key certificate formats, X.509 specifies an authentication protocol.The original version of X.509 contains a security flaw.The essence of the protocol...
-
Use the information in the adjusted trial balance reported in Exercise 4-11 to prepare Wilson Trucking Company's classified balance sheet as of December 31, 2017. In Exercise 4-11 Account Title...
-
Civil What are the challenges of using intermediate structures in the analysis of Pauli structures?
-
Civil What are the advantages of intermediate structures in the analysis of Laguerre structures?
-
Civil What are the disadvantages of using intermediate structures in the analysis of geothermal energy environmental product promotion?
-
Civil How can intermediate structures be used in the analysis of geothermal energy environmental product pulmonary toxins?
-
Civil What challenges arise when using intermediate structures in the analysis of structural robustness?
-
You wait 40 h for an exponentially distributed event to occur. The null hypothesis is that the mean wait is 1000 h with the alternative hypothesis that the mean wait is less than 1000 h. Find the...
-
Suppose that a flow network G = (V, E) violates the assumption that the network contains a path s t for all vertices V. Let u be a vertex for which there is no path s u t. Show that there must...
-
Consider the following NAMS instruction: cmp vleft, vright For signed integers, there are three status flags that are relevant. If vleft = vright, then ZF is set. If vleft > vright, ZF is unset (set...
-
Consider the following C program: /* a simple C program to average 3 integers */ main ( ) { int avg; int i1 = 20; int i2 = 13; int i3 = 82; avg = (i1 + i2 + i3)/3; } Write an NASM version of this...
-
Consider the following C code fragment: if (EAX == 0) EBX = 1; else EBX = 2; Write an equivalent NASM code fragment.
-
Which of the following concerning short-term financing methods is NOT CORRECT? Short-term bank loans typically do not require assets as collateral. Firms generally have little control over the level...
-
Kingbird Corporation is preparing its December 31, 2017, balance sheet. The following items may be reported as either a current or long-term liability. 1. On December 15, 2017, Kingbird declared a...
-
BE13.2 (LO 1), AP An inexperienced accountant for Silva Corporation showed the following in the income statement: net income \$337,500 and unrealized gain on availablefor-sale securities (before...

Study smarter with the SolutionInn App


