For each of the cybercrimes cited in Table 23.1, indicate whether it falls into the category of
Question:
For each of the cybercrimes cited in Table 23.1, indicate whether it falls into the category of computer as target, computer as storage device, or computer as communications tool. In the first case, indicate whether the crime is primarily an attack on data integrity, system integrity, data confidentiality, privacy, or availability.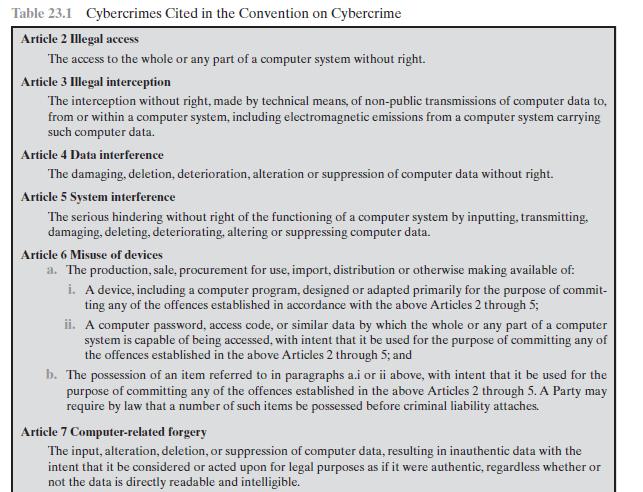

Transcribed Image Text:
Table 23.1 Cybercrimes Cited in the Convention on Cybercrime Article 2 Illegal access The access to the whole or any part of a computer system without right. Article 3 Illegal interception The interception without right, made by technical means, of non-public transmissions of computer data to, from or within a computer system, including electromagnetic emissions from a computer system carrying such computer data. Article 4 Data interference The damaging, deletion, deterioration, alteration or suppression of computer data without right. Article 5 System interference The serious hindering without right of the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data. Article 6 Misuse of devices a. The production, sale, procurement for use, import, distribution or otherwise making available of: i. A device, including a computer program, designed or adapted primarily for the purpose of commit- ting any of the offences established in accordance with the above Articles 2 through 5; ii. A computer password, access code, or similar data by which the whole or any part of a computer system is capable of being accessed, with intent that it be used for the purpose of committing any of the offences established in the above Articles 2 through 5; and b. The possession of an item referred to in paragraphs a.i or ii above, with intent that it be used for the purpose of committing any of the offences established in the above Articles 2 through 5. A Party may require by law that a number of such items be possessed before criminal liability attaches. Article 7 Computer-related forgery The input, alteration, deletion, or suppression of computer data, resulting in inauthentic data with the intent that it be considered or acted upon for legal purposes as if it were authentic, regardless whether or not the data is directly readable and intelligible.
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 75% (4 reviews)
Article 2 Illegal access This is a general threat the could fall into any of the t...View the full answer

Answered By

Felix Onchweri
I have enough knowledge to handle different assignments and projects in the computing world. Besides, I can handle essays in different fields such as business and history. I can also handle both short and long research issues as per the requirements of the client. I believe in early delivery of orders so that the client has enough time to go through the work before submitting it. Am indeed the best option that any client that can think about.
4.50+
5+ Reviews
19+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
1. How strong are the competitive forces confronting J. Crew in the market for specialty retail? Do a [Michael Porter] five-forces analysis to support your answer. (see chapter 3 in the textfor...
-
"I'm not sure we should lay out $300,000 for that automated welding machine," said Jim Alder, president of the Superior Equipment Company. "That's a lot of money, and it would cost us $84,000 for...
-
During one week, four production employees of Martinez Manufacturing Company worked the hours shown below. All these employees receive overtime pay at one and one-half times their regular hourly rate...
-
Liquid propane is burned with dry air. A volumetric analysis of the products of combustion yields the following volume percent composition on a dry basis: 8.6% CO2, 0.6% CO, 7.2% O2 and 83.6% N2....
-
A closed walk that ______________ is a circuit. Fill in the blanks to make the statement true.
-
Why is SSE not necessarily a good measure of cluster quality?
-
The complexity and uniqueness of the federal government makes it difficult to conduct a meaningful analysis of its financial condition. However, conducting a financial statement analysis does provide...
-
Problem 4 - 2 Preparation of a statement of cash flows and a balance sheet ( LO 4 - 1 , LO 4 - 5 , LO 4 - 7 ) Kay Wing. Inc, prepared the following balance sheet at December 3 1 , 2 0 0 . \ table [ [...
-
Repeat Problem 23.1 for Table 23.2. Table 23.2 CERT 2006 E-Crime Watch Survey Results Theft of intellectual property Theft of other (proprietary) info including customer records, financial records,...
-
What functions can a professional code of conduct serve to fulfill?
-
(a) Sketch a logic-gate network that implements the multiplexer MUX in Figure 6.26. (b) Relate the structure of the SWAP network in Figure 6.26 to your solution to Part (a).
-
Use as many directional terms as possible to describe therelationshipbetween: a. the antecubital region and the poplitealregion b. the acromial region and the mentalregion c. the gluteal region and...
-
Average rate of return-cost savings Maui Fabricators Inc. is considering an investment in equipment that will replace direct labor. The equipment has a cost of $114,000 with a $10,000 residual value...
-
Alan was rated as excellent on his individual work performance evaluation, earning him $2,000, provided as a merit pay increase. His annual salary this year is $48,000. He works in a team of 3...
-
Josie spends $60 at the end of each month on cigarettes. If shestops smoking and invests the same amount in an investment planpaying 6% compounded monthly, how much will she have after fiveyears? 2...
-
Say we have a Boeing 747 whose longitudinal flight dynamics for a given flight condition may be approximated using the following state equation (uncontrolled motion; thus no need to consider the...
-
Remove the terms that do not depend on and show that the maximum occurs at = . Follow the steps to show that the support has the simple quadratic form given in the text.
-
"Standard-cost procedures are particularly applicable to process-costing situations." Do you agree? Why?
-
An example of a host-based intrusion detection tool is the tripwire program. This is a file integrity checking tool that scans files and directories on the system on a regular basis and notifies the...
-
Test the vulnerability of a machine at the following site: grc.com/default.htm. Follow the ShieldsUP! link for a series of free tests listed midway down the page.
-
The tiny fragment attack is a form of firewall attack. The intruder uses the IP fragmentation option to create extremely small fragments and force the TCP header information into a separate packet...
-
The star Mira is 1.2 times the mass of the Sun and about 10,000 times more luminous than the Sun. Would Mira fit into the table above? Why or why not?
-
Which of the following was one of the most valuable benefits a company received as a sponsor of NHL games?
-
Cinder Inc. is a Canadian-controlled private corporation based in your province. The company operates a wholesale business. The following information is provided for its year ended May 31, 2023: Net...

Study smarter with the SolutionInn App


