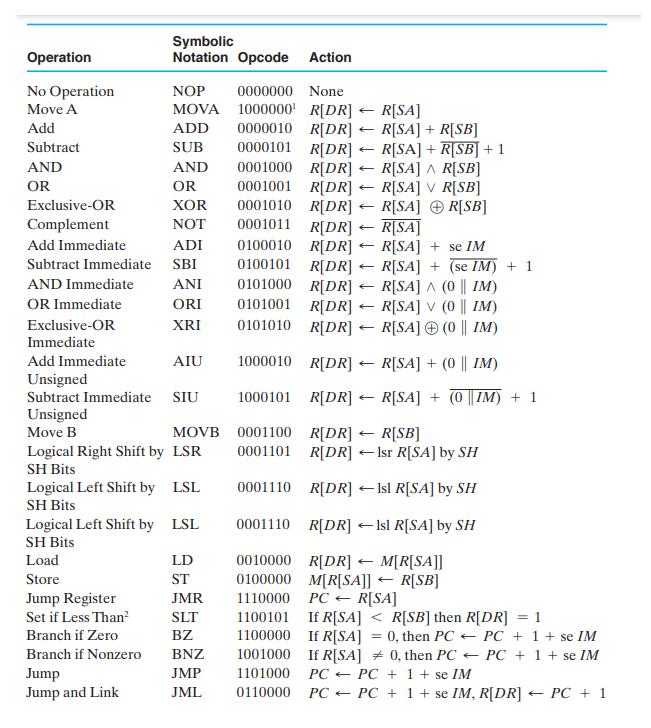
For each of the RISC operations in Table 10-1, list the addressing mode or modes used. Table
Question:
For each of the RISC operations in Table 10-1, list the addressing mode or modes used.
Table 10-1
Transcribed Image Text:
Operation No Operation Move A Add Subtract AND OR Exclusive-OR Complement Add Immediate Subtract Immediate AND Immediate OR Immediate Exclusive-OR Immediate Symbolic Notation Opcode Action NOP 0000000 None MOVA 1000000 R[DR] ADD 0000010 R[DR] SUB 0000101 R[DR] AND OR Branch if Zero Branch if Nonzero XOR NOT Add Immediate Unsigned Subtract Immediate SIU Unsigned Move B MOVB Logical Right Shift by LSR SH Bits Jump Jump and Link ADI SBI ANI ORI XRI Logical Left Shift by LSL SH Bits AIU Logical Left Shift by LSL SH Bits Load Store Jump Register Set if Less Than LD ST JMR SLT BZ BNZ JMP JML 0001000 0001001 R[DR] R[SA] ^ R[SB] R[DR] 0001010 R[DR] R[SA] 0001011 R[DR] R[SA] 0100010 R[DR] R[SA] + 0100101 R[DR] R[SA] 0101000 R[DR] R[SA] ^ (0 || IM) 0101001 R[DR] R[SA] V (0 || IM) 0101010 R[DR] R[SA] (0 || IM) 1000010 R[DR] 1000101 R[DR] 0001100 0001101 0001110 0001110 0010000 0100000 R[SA] R[SA] + R[SB] R[SA] + R[SB] + 1 R[SA] V R[SB] R[SB] 1100101 1100000 1001000 If R[SA] 1101000 PC- 0110000 PC R[SA] + (0 || IM) R[SA] + (0|IM) + 1 R[DR] R[SB] R[DR] - Isr R[SA] by SH R[DR] -Isl R[SA] by SH R[DR] Isl R[SA] by SH R[DR] M[R[SA]] M[R[SA]] R[SB] se IM (se IM) + 1 1110000 PC - R[SA] If R[SA] < R[SB] then R[DR] = 1 If R[SA] = 0, then PC PC + 1+ se IM 0, then PC - PC + 1+ se IM PC + 1+ se IM PC + 1 + se IM, R[DR] PC + 1
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 66% (3 reviews)
Register Indirect Register Imme...View the full answer

Answered By

Rashul Chutani
I have been associated with the area of Computer Science for long. At my university, I have taught students various Computer Science Courses like Data Structures, Algorithms, Theory of Computation, Digital Logic, System Design, and Machine Learning. I also write answers to questions posted by students in the area of and around Computer Science.
I am highly fortunate to receive great feedback on my teaching skills that keeps me motivated. Once a student sent me an email stating that I had explained to him a concept better than his professor did.
I believe in the fact that "Teaching is the best way to learn". I am highly fascinated by the way technology nowadays is solving real-world problems and try to contribute my bit to the same.
Besides tutoring, I am a researcher at the Indian Institute of Technology. My present works are in the area of Text Summarization and Signal and Systems.
Some of my achievements include clearing JEE Advanced with an All India Rank of 306 out of 1.5 million contesting candidates and being the Department Ranker 1 at my University in the Department of Computer Science and Engineering.
I look forward to providing the best Tutoring Experience I can, to the student I teach.
5.00+
1+ Reviews
10+ Question Solved
Related Book For 

Logic And Computer Design Fundamentals
ISBN: 9780133760637
5th Edition
Authors: M. Morris Mano, Charles Kime, Tom Martin
Question Posted:
Students also viewed these Computer science questions
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
THE SHOPPES AT RIVERSIDE Fonda L. Carter, Columbus State University Kirk Heriot, Columbus State University CASE DESCRIPTION This case asks the students to recommend a decision to a group of...
-
The Urban Real Estate Agency is undergoing expansion. The real estate boom has led to a sharp increase in real estate transactions. The agency has more than tripled its volume of transactions and, as...
-
What is the difference between a market system and a market? How Can you have a market without a market system? Why or why not? How about the other way around? Can you have a market system without a...
-
There are five resonance structures of Phenanthrene, one of which is shown. Draw the otherfour. Phenanthrene
-
Panda Manufacturing (PM) is a division of Worldwide Communications, Inc. PM produces pagers and other personal communication devices. These devices are sold to other Worldwide divisions, as well as...
-
What is credit risk? What is market risk?
-
Danna Martin, president of Mays Electronics, was concerned about the end-of-the year marketing report that she had just received. According to Larry Savage, marketing manager, a price decrease for...
-
Blossom, Inc, reports the following operating results for August: Sales $488,000 (units 6,100 ); variable costs $292,800; and fixed costs $109.800. Management is considering the following independent...
-
A program consisting of a sequence of ten instructions without branch or jump instructions is to be executed in an 8-stage pipelined RISC computer with a clock period of 0.5 ns. Determine (a) The...
-
Assume that a computer has eight general purpose registers R0R7, a stack pointer register SP, and program counter PC. If the calling convention for this computer is that registers R0 and R1 are used...
-
Which of the following statements is false or true? A. In the DFS graph, the traversing technique queue data structure is used. B. In expression evaluation, the stack data structure is used. A....
-
The residents of the town of Stewart are well-known coffee drinkers. Dunkin Donuts and Starbucks stores supply the residents with over 100,000 cups of hot coffee per week. Recently, coffee drinkers...
-
Read through the following case study and analyse it by addressing the question that follows. Case study: Adriana Adriana runs a very busy multi-sports coaching company that provides after-school...
-
Assuming that you were invited to one of your best friends' wedding. Therefore, you decided to purchase a special product or service as a gift for this important event. Based on this scenario, you...
-
The Department of Commerce, through the Economic Development Administration (EDA), is seeking information to inform the planning and design of the Regional Technology and Innovation Hub (Tech Hubs)...
-
In frontline management, it is essential to manage time effectively. In the table below, list 3 time-management principles that are relevant to a frontline manager's own work and provide 3 examples...
-
The following diagrams represent mixtures of NO(g) and O2(g). These two substances react as follows: 2 NO(g) + O2(g) -- 2 NO2(g) It has been determined experimentally that the rate is second order in...
-
Discuss the information available from the following techniques in the analysis of inorganic pigments used in antique oil paintings: (i) Powder X-ray diffraction, (ii) Infrared and Raman...
-
Suppose Alice has picked three distinct integers and placed them into a stack S in random order. Write a short, straightline piece of pseudocode (with no loops or recursion) that uses only one...
-
Augment the ArrayQueue implementation with a new rotate( ) method having semantics identical to the combination, enqueue(dequeue( )). But, your implementation should be more efficient than making two...
-
Repeat the previous problem using the deque D and an initially empty stack S. Previous problem Suppose you have a deque D containing the numbers (1,2,3,4,5,6,7,8), in this order. Suppose further that...
-
What is the present value of $500 invested each year for 10 years at a rate of 5%?
-
GL1203 - Based on Problem 12-6A Golden Company LO P2, P3 Golden Corp.'s current year income statement, comparative balance sheets, and additional information follow. For the year, (1) all sales are...
-
A project with an initial cost of $27,950 is expected to generate cash flows of $6,800, $8,900, $9,200, $8,100, and $7,600 over each of the next five years, respectively. What is the project's...

Study smarter with the SolutionInn App


