Imagine that you are a newly hired network consultant for SNHUEnergy Inc., a quickly growing oil and gas company that has decided to expand its
Imagine that you are a newly hired network consultant for SNHUEnergy Inc., a quickly growing oil and gas company that has decided to expand its operation and begin developing a more efficient approach to its use of the currently available technology. As a consultant for the company, you will evaluate the current network architecture, determine any key changes that should occur, and recommend a high-level design for future growth. The leadership team within the company has made a major commitment to the board of directors that they will begin an initiative to create a communication architecture that will allow the company to grow for the next ten years. You have been assigned the task of addressing the overall framework for the architecture and evaluating the basic structure of the network, its communication paths, and the type of traffic utilized. You will also begin to develop a basic security plan in an effort to mitigate any risk the company currently has to internal and external factors.
SNHUEnergy Inc. is a medium-sized oil and gas company that is focused on the discovery and drilling of oil-based products. It wants to grow from company solely focused on exploration into a company that also provides the transportation and refinement of its discoveries. This is a big step for the company, and it wants to make sure the communication infrastructure is ready to deliver in the next 12 to 18 months. The company is currently headquartered in Dallas, Texas, and operates small facilities in the central United States. The total employee count is 120 across the organization, but this will grow by 50% each year for the next two years. Initially, you will evaluate the current logical and physical design of the network to determine the network connectivity, the traffic patterns of the organization, and what would need to occur to enable the business to grow.
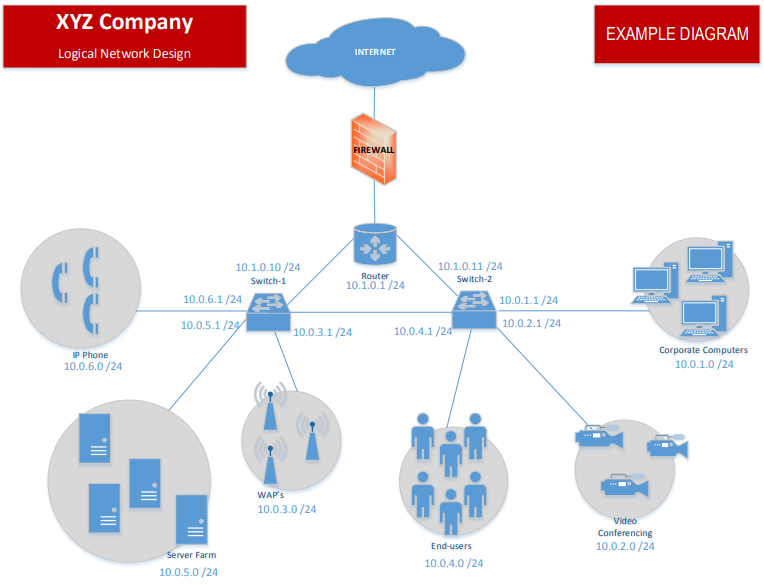
The network infrastructure consists of a single building with multiple floors and different divisions (human resources, IT, accounting, and operations and payroll). The company will develop a plan to expand to three additional regional offices in Kansas City and Houston. You will be asked to take the initial design and determine what traffic will need to communicate at each office and which security parameters will need to exist as the company grows. This work will consist of understanding the connectivity and traffic traversing internally and externally and developing a plan to enable end-users to access the correct communication to the key critical applications (i.e., human resources, email, and Voice over Internet Protocol [VoIP]) across the company.
The infrastructure consists of network routers, switches, and firewall equipment that currently connect all the users to the internet internally and externally. All the connectivity between the users is Transmission Control Protocol/Internet Protocol (TCP/IP) traffic, which is utilized by data, voice, and video applications across the organization.
In the future, the company will extend these services across the wide area network (WAN) by using TCP/IP communication processes.
Required:
Provide a high-level overview of the SNHUEnergy Inc. network architecture. Evaluate traffic patterns to determine critical aspects of your business and provide basic insight into what should be done to the network from a capability aspect as well as a security viewpoint.
Write a paper in which you need to address the following:
Based on what you know from the scenario, explain the types of physical network devices used in connecting all devices across the organization.
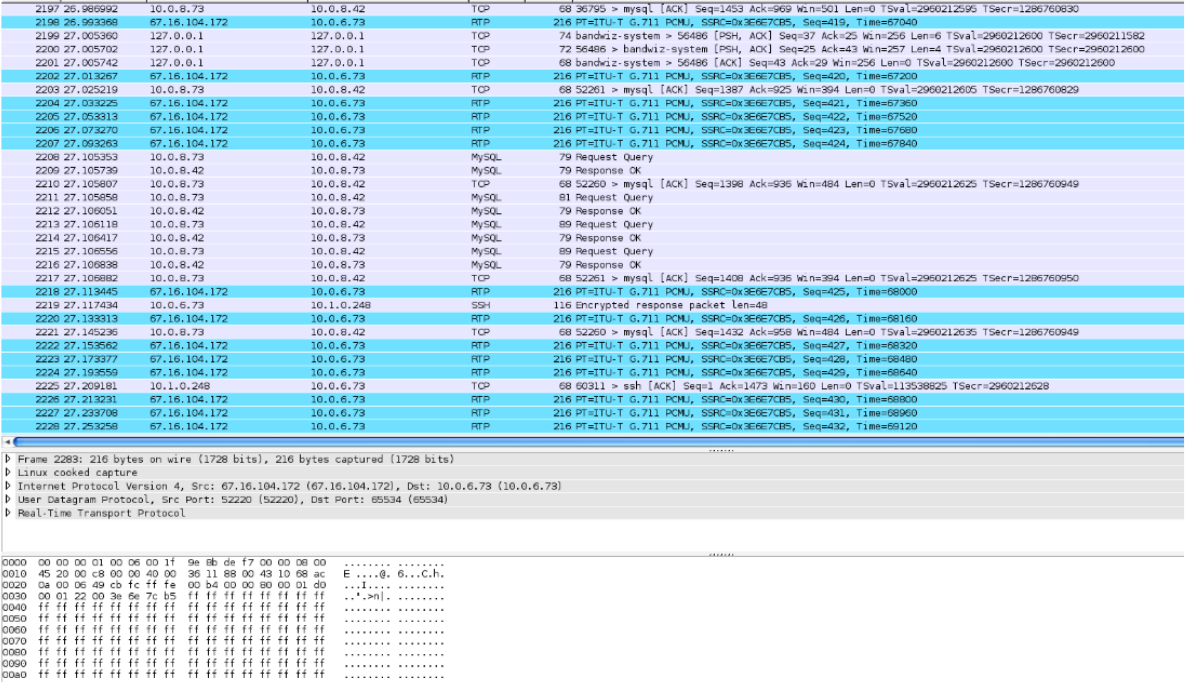
Identify the critical traffic patterns currently used by the organization, supported by examples. Use the Traffic Flow Wire-shark Capture document to guide your response.
Service (Voice over Internet Protocol [VoIP])
Application (Structured Query Language [SQL])
Network management
Describe the traffic patterns that the organization?s critical applications take across the infrastructure from office to office. Remember, the organization?s critical applications were specified in the scenario.
Describe the potential performance issues that may occur within the current network if no changes are made to support the organization?s expansion.
Describe the potential security issues that may occur within the current network if no changes are made to support the organization?s expansion.
2197 26.986992 2198 26.993368 2199 27.005360 2200 27.005702 2201 27.005742 2202 27.013267 2203 27.025219 2204 27.033225 2205 27.053313 2206 27.073270 2207 27.093263 2208 27.105353 2209 27.105739 2210 27.105807 2211 27.105858 2212 27.106051 2213 27.106118 2214 27.106417 2215 27.106556 2216 27.106838 2217 27.106882 2218 27.113445 2219 27.117434 2220 27.133313 2221 27.145236 2222 27.153562 2223 27.173377 2224 27.193559 2225 27.209181 2226 27.213231 2227 27.233708 2228 27.253258 10.0.8.73 67.16.104.172 127.0.0.1 127.0.0.1 127.0.0.1 67.16.104.172 10.0.8.73 67.16.104.172 67.16.104.172 67.16.104.172 67.16.104.172 10.0.8.73 10.0.8.42 10.0.8.73 10.0.8.73 10.0.8.42 10.0.8.73 10.0.8.42 10.0.8.73 10.0.8.42 10.0.8.73 67.16.104.172 10.0.6.73 67.16.104.172 10.0.8.73 67.16.104.172 67.16.104.172 67.16.104.172 10.1.0.248 67.16.104.172 67.16.104.172 67.16.104.172 10.0.8.42 10.0.6.73 127.0.0.1 127.0.0.1 127.0.0.1 10.0.6.73 10.0.8.42 10.0.6.73 10.0.6.73 10.0.6.73 10.0.6.73 10.0.8.42 10.0.8.73 10.0.8.42 10.0.8.42 10.0.8.73 10.0.8.42 10.0.8.73 10.0.8.42 10.0.8.73 10.0.8.42 10.0.6.73 10.1.0.248 10.0.6.73 10.0.8.42 10.0.6.73 10.0.6.73 10.0.6.73 10.0.6.73 10.0.6.73 10.0.6.73 10.0.6.73 Frame 2283: 216 bytes on wire (1728 bits), 216 bytes captured (1728 bits) Linux cooked capture 0000 00 00 00 01 00 06 00 1f 06 00 11 0010 45 20 00 45 20 00 c8 00 00 40 00 00 00 40 00 0020 Da 00 06 49 cb fc ff fe 0030 00 01 22 00 3e 6e 7c b5 0040 ff ff ff ff ff ff ff ff 0050 ff ff ff ff ff ff ff ff 0060 ff ff ff ff ff ff ff ff 0070 ff ff ff ff ff ff ff ff 0080 ff ff ff f f 0090 ff ff ff ff ff ff ff ff 0080 ff ff ff ff ff ff ff ff 9e Bb de f7 00 00 08 00 36 11 88 00 43 10 68 ac 00 b4 00 00 80 00 01 do ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff f f f f ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff TCP RTP TOP E..... 6...c.h. ....... ...n. TOP TOP RTP TOP RTP RTP RTP RTP MySQL MySQL TCP MySQL MySQL Internet Protocol Version 4, Src: 67.16.104.172 (67.16.104.172), Dst: 10.0.6.73 (10.0.6.73) User Datagram Protocol, Src Port: 52220 (52220), Dst Port: 65534 (65534) Real-Time Transport Protocol MySQL MySQL MySQL MySQL TCP RTP SSH RTP TOP RTP RTP RTP TOP RTP RTP RTP 68 36795 > mysql [ACK] Seq=1453 Ack=969 win=501 Len=0 TSval=2960212595 TSecr=1286760830 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=419, Time=67040 74 bandwiz-system> 56486 [PSH, ACK] Seq=37 Ack=25 Win=256 Len=6 TSval-2960212600 TSecr=2960211582 72 56496 > bandwiz-system [PSH, ACK] Seq=25 Ack=43 Win=257 Len=4 TSval=2960212600 TSecr=2960212500 68 bandwiz-system> 56486 [ACK] Seq=43 Ack-29 Win=256 Len=0 TSval=2960212600 TSecr=2960212600 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=420, Time=67200 68 52261 > mysql [ACK] Seq=1387 Ack-925 Win=394 Len=0 TSval-2960212605 TSecr=1286760829 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=421, Time=67360 216 PT ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=422, Time=67520 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=423, Time=67680 216 PT ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=424, Time=67840 79 Request Query 79 Response CK 68 52260 > mysql [ACK] Seq=1398 Ack=936 Win=484 Len=0 TSval=2960212625 TSecr=1286760949 81 Request Query 79 Response CK 89 Request Query 79 Response CK 89 Request Query 79 Response OK 68 52261 > mysql [ACK] Seq=1408 Ack=936 Win=394 Len=0 TSval=2960212625 TSecr=1286760950 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=425, Time=68000 116 Encrypted response packet len=48 216 PT=ITU-T G.711 PCMJ, SSRC=0x3E6E7CB5, Seq=426, Time=68160 68 52260 > mysql [ACK] Seq=1432 Ack=958 Win=484 Len=0 TSval=2960212635 TSecr=1286760949 216 PT ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=427, Time=68320 216 PT ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=428, Time=68480 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CB5, Seq=429, Time=68640 68 60311 ssh [ACK] Seq=1 Ack=1473 Win=160 Len=0 TSval=113538825 TSecr=2960212628 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=430, Time=68800 216 PT ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=431, Time=68960 216 PT=ITU-T G.711 PCMU, SSRC=0x3E6E7CBS, Seq=432, Time=69120 CALEIAL XYZ Company Logical Network Design IP Phone 10.0.6.0/24 * ||| * ||| 10.0.6.1/24 10.0.5.1/24 * ||| 10.1.0.10/24 Switch-1 Server Farm 10.0.5.0/24 10.0.3.1/24 WAP's 10.0.3.0/24 INTERNET FIREWALL Router 10.1.0.1/24 10.1.0.11/24 Switch-2 10.0.4.1/24 End-users 10.0.4.0/24 10.0.1.1/24 10.0.2.1/24 EXAMPLE DIAGRAM Video Conferencing 10.0.2.0/24 PEMANNS Corporate Computers 10.0.1.0/24
Step by Step Solution
3.47 Rating (163 Votes )
There are 3 Steps involved in it
Step: 1
The key network components Most important data networks are designed to connect users and allow them access to resources such as the Internet and other computers connected to the network Networking co...
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


