Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1. [3 marks] Suppose you are responsible for the IT infrastructure of an organization, which has about 20 desktop computers. You are advised that
![1. [3 marks] Suppose you are responsible for the IT infrastructure of an organization, which has about 20](https://dsd5zvtm8ll6.cloudfront.net/questions/2023/10/6540c21ae7395_1698742805758.jpg)
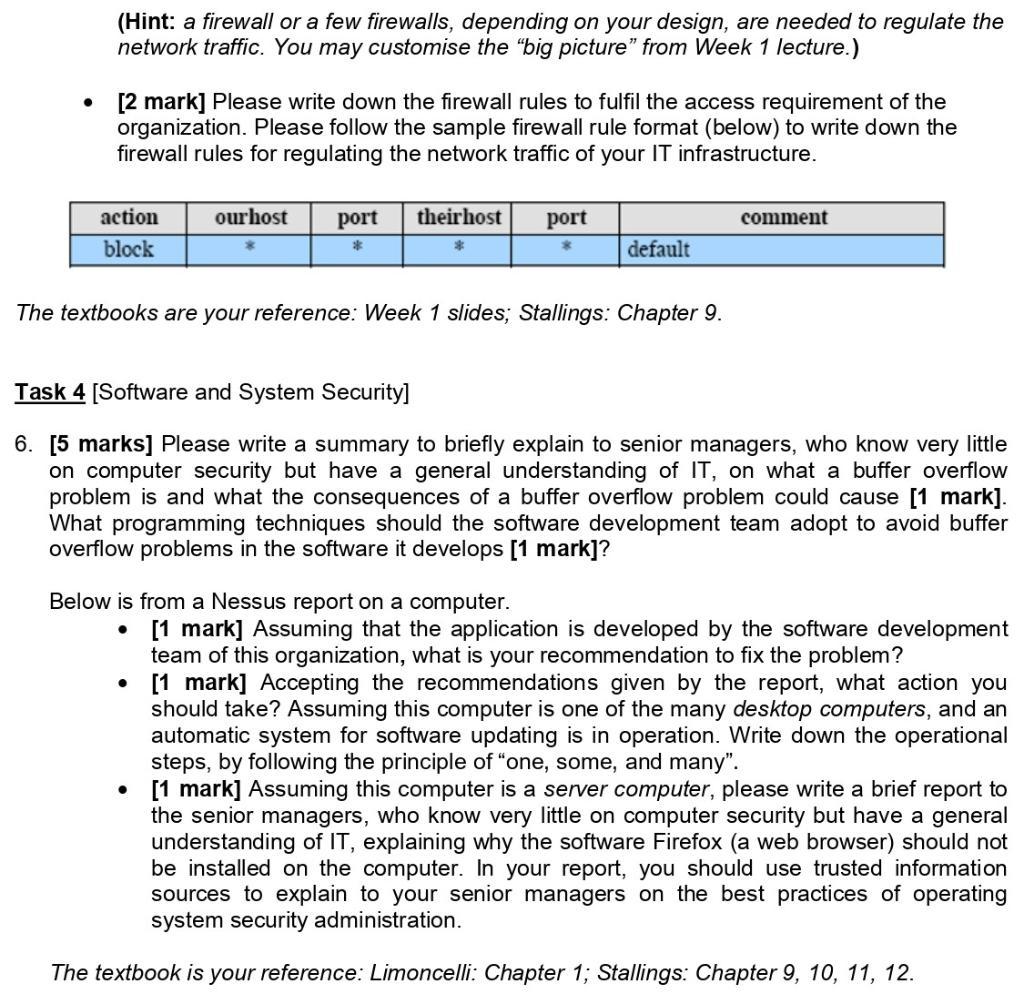
1. [3 marks] Suppose you are responsible for the IT infrastructure of an organization, which has about 20 desktop computers. You are advised that automation for uniformity is a good solution. What does "automation for uniformity" mean? Why is it a good solution in principle? Will you implement a fully automatic system in this case of yours? 2. [2 marks] Please summarise the technologies used in server computers to improve reliability. availability, and performance. 3. [2 mark] Please summarise the essentials of running a well organised Helpdesk operation. Task 2 [Cryptography] 4. [3 marks] Suppose that you are responsible for the IT department of a university with students around the world. It is infeasible to meet each student in person. The IT department is responsible for all secure communication with the students. Assume that there is a trusted certificate authority which can securely issue certificates to all involved parties. Please explain: Why the trusted certificate authority is essential to establish a secure communication? What role does it play in the secure communication between the IT department and the students? From time to time, your department, on behalf of the University, makes public announcements. The announcements are of public nature and can be shared and transmitted by any interested parties, say, prospective students. How would you guarantee the authenticity of your announcements? It is not a solution to publish the announcement on a website for students to compare and decide if the received copies are the same as the web copies. Task 3 [DoS and Firewall] 5. [5 marks] An organization has two server computers and several desktop computers, a few printers (IP address: p1.p2.p3.p4) and routers (IP address: r1.r2.r3.r4). All of them are connected via an internal network, and the network is connected to the Internet via the border router of the organization. From the outside of the organization, on the Internet, only these two server computers are visible. One of them is the email server (IP address: e1.e2.e3.e4), and the other one is the web server (IP address: w1.w2.w3.w4). In other words, only these two server computers accept requesting incoming network traffic. All desktop computers (IP address: d1.d2.d3.d4) are allowed to access the Internet, without any restriction. Therefore, they accept responding incoming network traffic, but cannot accept any requesting incoming network traffic. . [3 marks] Please design the network and draw the network diagram. You have the freedom to assume the internal network structure. In the diagram, in addition to the two servers, you should also include a few desktop computers and a printer. Please explain the rationale on why you put a computer or a printer in its designated location, one example for each location. A subnet (or a segment) is regarded as the same location. (Hint: a firewall or a few firewalls, depending on your design, are needed to regulate the network traffic. You may customise the "big picture" from Week 1 lecture.) [2 mark] Please write down the firewall rules to fulfil the access requirement of the organization. Please follow the sample firewall rule format (below) to write down the firewall rules for regulating the network traffic of your IT infrastructure. action block ourhost port * theirhost port * The textbooks are your reference: Week 1 slides; Stallings: Chapter 9. Below is from a Nessus report on a computer. * default Task 4 [Software and System Security] 6. [5 marks] Please write a summary to briefly explain to senior managers, who know very little on computer security but have a general understanding of IT, on what a buffer overflow problem is and what the consequences of a buffer overflow problem could cause [1 mark]. What programming techniques should the software development team adopt to avoid buffer overflow problems in the software it develops [1 mark]? comment [1 mark] Assuming that the application is developed by the software development team of this organization, what is your recommendation to fix the problem? [1 mark] Accepting the recommendations given by the report, what action you should take? Assuming this computer is one of the many desktop computers, and an automatic system for software updating is in operation. Write down the operational steps, by following the principle of "one, some, and many". [1 mark] Assuming this computer is a server computer, please write a brief report to the senior managers, who know very little on computer security but have a general understanding of IT, explaining why the software Firefox (a web browser) should not be installed on the computer. In your report, you should use trusted information sources to explain to your senior managers on the best practices of operating system security administration. The textbook is your reference: Limoncelli: Chapter 1; Stallings: Chapter 9, 10, 11, 12.
Step by Step Solution
★★★★★
3.49 Rating (156 Votes )
There are 3 Steps involved in it
Step: 1
Answer to question 1 Automation for uniformity means using automation to ensure that all IT infrastructure components are configured and managed in the same way This can be achieved by using scripts c...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


