Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1 A company recently noted some brute force attempts to gain access to information on its website. The company mplements a new policy stating The
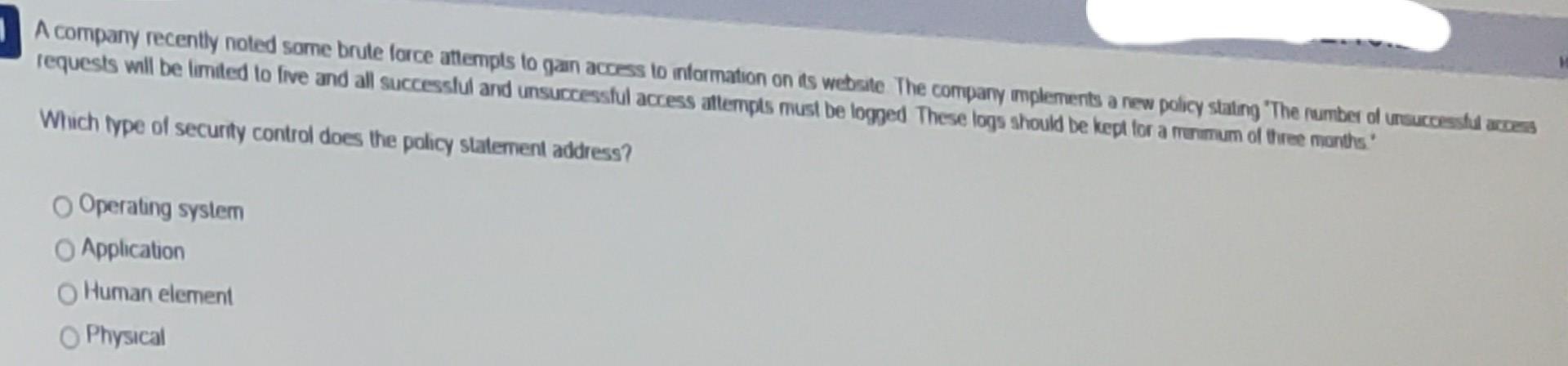


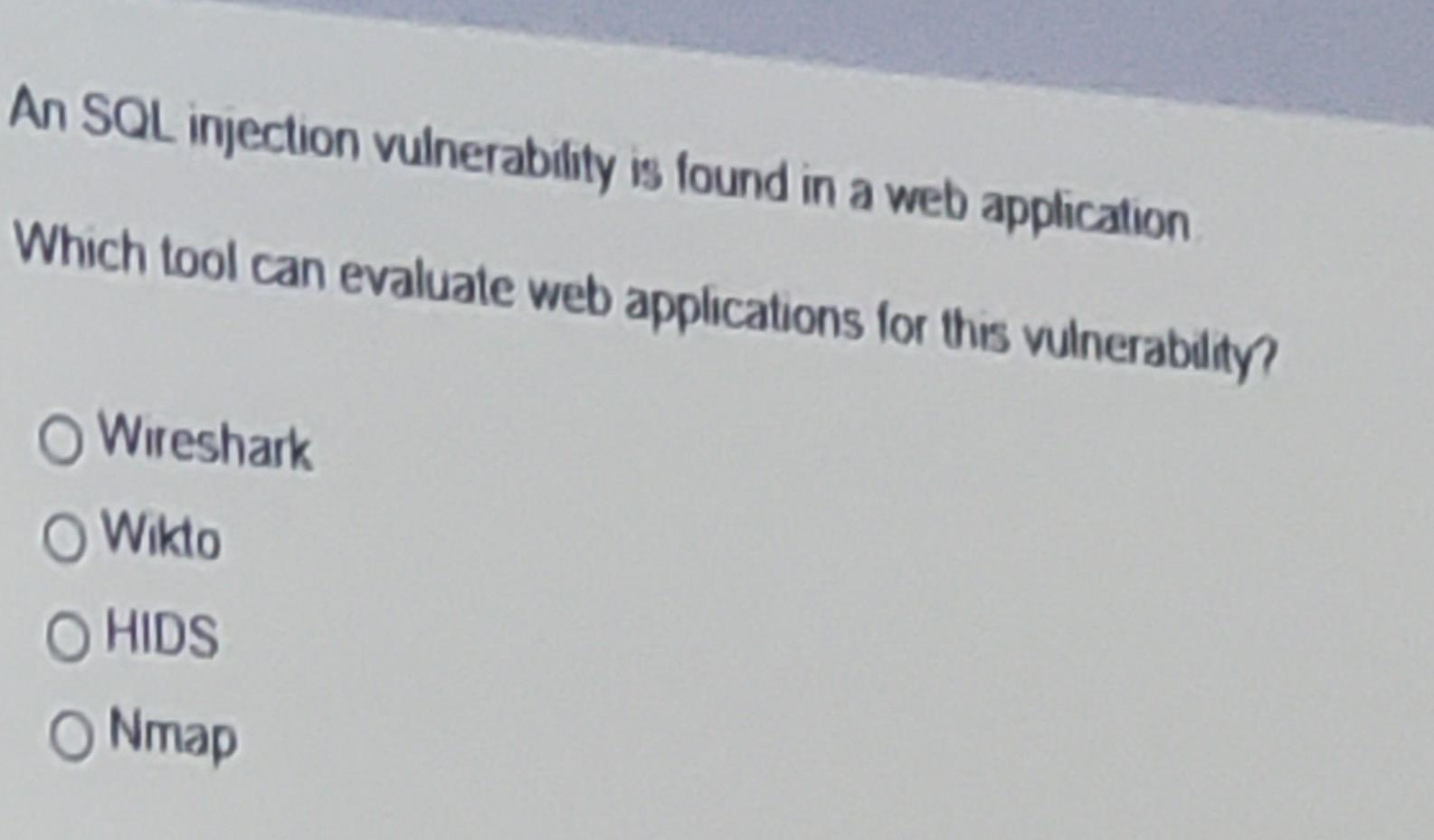
1 A company recently noted some brute force attempts to gain access to information on its website. The company mplements a new policy stating "The number of unsuccessful aces requests will be limited to live and all successiul and unsuccessful access attempts must be logged These logs should be kept for a frumum of three months. Which type of security control does the policy statement address? Operating system Application Human element Physical An organation sees annoase in recent uperating system vulnerabilities to address these nderebilities the organization modifies espectang persondataluny patches within 10 days of release Which deense in depth layer does the new policy address? Network Data Application Host Auser runs an applicabon that has been infected with malware. This malware then performs a brute force altack on the buill in administrator account on Windows systems The malware successfully cracks the password, and is used to compromise other systems in the environment Which safeguard should be implemented to prevent this type of attack? Disable remote desktop access Modify the delault user accounts Uninstall unnecessary software Turn on logging and auditing An SQL injection vulnerability is found in a web application Which tool can evaluate web applications for this vulnerability o Wireshark O Wikto O HIDS Nmap
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


