Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1) Given the risks assessment results listed in the table in Section 5. Construct a risk register, adding the risk response column and populate with
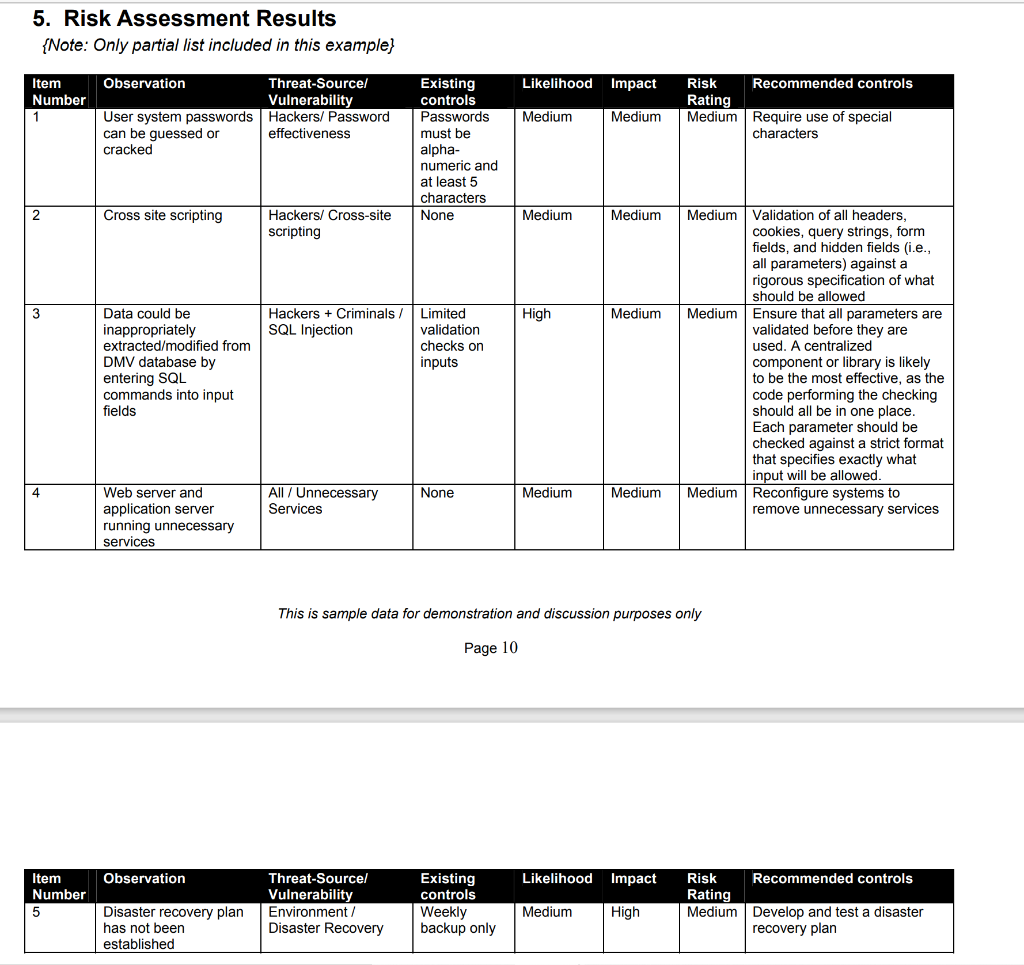
1) Given the risks assessment results listed in the table in Section 5. Construct a risk register, adding the risk response column and populate with what you think is an appropriate risk response action (e.g. accept, mitigate, etc.)
you just have to add one more column i.e. "RISK RESPONSE" . in that column we have to write about its mitigation
5. Risk Assessment Results {Note: Only partial list included in this example} Likelihood Impact Item Number 1 Observation Threat-Source Vulnerability User system passwords Hackers/ Password can be guessed or effectiveness cracked Risk Recommended controls Rating Medium Require use of special characters Medium Medium Existing controls Passwords must be alpha- numeric and at least 5 characters None 2 Cross site scripting Medium Medium Hackers/ Cross-site scripting 3 Hackers + Criminals SQL Injection High Medium Data could be inappropriately extracted/modified from DMV database by entering SQL commands into input fields Limited validation checks on inputs Medium Validation of all headers, cookies, query strings, form fields, and hidden fields (i.e., all parameters) against a rigorous specification of what should be allowed Medium Ensure that all parameters are validated before they are used. A centralized component or library is likely to be the most effective, as the code performing the checking che ch in one place. Each parameter should be checked against a strict format that specifies exactly what input will be allowed. Medium Reconfigure systems to remove unnecessary services should all be in me 4 All / Unnecessary Services None Medium Medium Web server and application server running unnecessary services This is sample data for demonstration and discussion purposes only Page 10 Observation Likelihood Impact Item Number 5 Threat-Sourcel Vulnerability Environment / Disaster Recovery Existing controls Weekly backup only Disaster recovery plan has not been established Medium High Risk Recommended controls Rating Medium Develop and test a disaster recovery plan 5. Risk Assessment Results {Note: Only partial list included in this example} Likelihood Impact Item Number 1 Observation Threat-Source Vulnerability User system passwords Hackers/ Password can be guessed or effectiveness cracked Risk Recommended controls Rating Medium Require use of special characters Medium Medium Existing controls Passwords must be alpha- numeric and at least 5 characters None 2 Cross site scripting Medium Medium Hackers/ Cross-site scripting 3 Hackers + Criminals SQL Injection High Medium Data could be inappropriately extracted/modified from DMV database by entering SQL commands into input fields Limited validation checks on inputs Medium Validation of all headers, cookies, query strings, form fields, and hidden fields (i.e., all parameters) against a rigorous specification of what should be allowed Medium Ensure that all parameters are validated before they are used. A centralized component or library is likely to be the most effective, as the code performing the checking che ch in one place. Each parameter should be checked against a strict format that specifies exactly what input will be allowed. Medium Reconfigure systems to remove unnecessary services should all be in me 4 All / Unnecessary Services None Medium Medium Web server and application server running unnecessary services This is sample data for demonstration and discussion purposes only Page 10 Observation Likelihood Impact Item Number 5 Threat-Sourcel Vulnerability Environment / Disaster Recovery Existing controls Weekly backup only Disaster recovery plan has not been established Medium High Risk Recommended controls Rating Medium Develop and test a disaster recovery planStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


