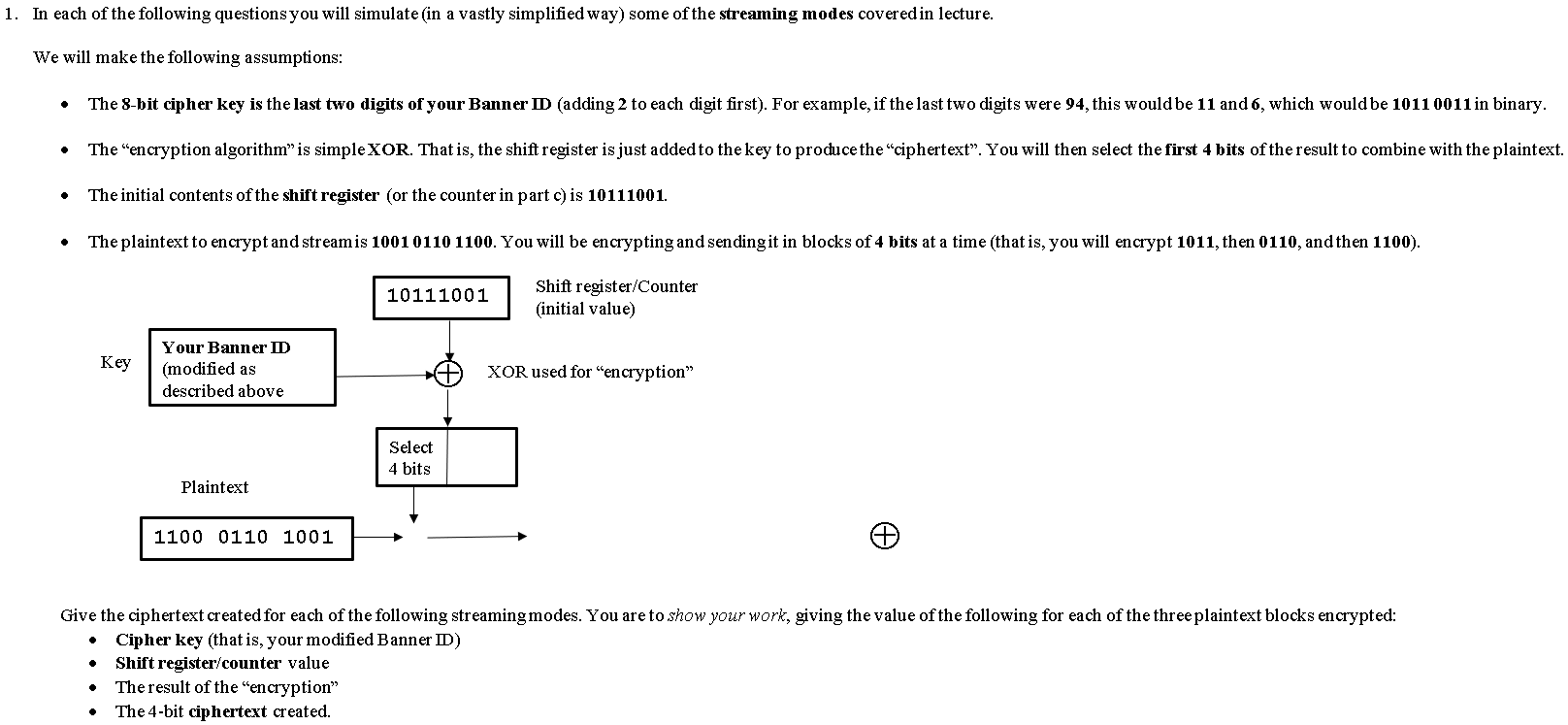

1. In each of the following questions you will simulate (in a vastly simplified way) some of the streaming modes covered in lecture. We will make the following assumptions: The 8-bit cipher key is the last two digits of your Banner ID (adding 2 to each digit first). For example, if the last two digits were 94, this would be 11 and 6, which would be 1011 0011 in binary. The "encryption algorithm" is simple XOR. That is, the shift register is just added to the key to produce the "ciphertext". You will then select the first 4 bits of the result to combine with the plaintext. . The initial contents of the shift register or the counter in part c) is 10111001. . The plaintext to encrypt and streamis 1001 0110 1100. You will be encrypting and sendingit in blocks of 4 bits at a time that is, you will encrypt 1011, then 0110, and then 1100). 10111001 Shift register/Counter (initial value) Key Your Banner D (modified as described above XOR used for "encryption" Select 4 bits Plaintext 1100 0110 1001 Give the ciphertext created for each of the following streaming modes. You are to show your work, giving the value of the following for each of the three plaintext blocks encrypted: Cipher key (that is, your modified Banner ID) Shift register/counter value The result of the "encryption" The 4-bit ciphertext created. a) Cipher Feedback Mode b) Output Feedback Mode 2. You are working for a company that provides security recommendations for a number of IT firms, each with different requirements and goals. For each of the following scenarios, give the transmission mode you would recommend or sending information, and why you would do so. a) Company A sends messages in blocks (that is, no streaming). These messages are very large, containing many repeated blocks. Speed of encryption/decryption is not a concern. They are willing to generate and send a new key for each message if necessary. b) Company G streams messages over a network. They are willing to generate and exchange a new key each time. To save time during encryption, they would like to have the ability to generate the entire key stream in advance (that is, before the actual message to be encrypted is known). c) Company Csends message in blocks (that is, no streaming). These messages are very short, consisting of few blocks, and are not sent very often. They also have parallel hardware that they would like to take advantage of in order to speed up the encryption/decryption process. They would like to avoid having to generate and exchange new keys for each message. d) Company D streams messages over a network. These messages are generally long and sent very often. They will not generate new keys for each message. They also have parallel hardware they would like to take advantage of, but are willing to sacrifice that speed for better security. Additional problem for Graduate Students: 3. Suppose that you are using CBC mode to send a message that consists of n blocks. Furthermore, suppose that thereis a transmission error in sending ciphertext block i to the recipient. Specifically, a single bit is changed due to noise (for example, a 1 in the ciphertext sent is changed to a 0 in the ciphertext received). Clearly, this will lead to an error in the plaintext block i that therecipient creates during decryption. How many other blocks will also be affected? 1. In each of the following questions you will simulate (in a vastly simplified way) some of the streaming modes covered in lecture. We will make the following assumptions: The 8-bit cipher key is the last two digits of your Banner ID (adding 2 to each digit first). For example, if the last two digits were 94, this would be 11 and 6, which would be 1011 0011 in binary. The "encryption algorithm" is simple XOR. That is, the shift register is just added to the key to produce the "ciphertext". You will then select the first 4 bits of the result to combine with the plaintext. . The initial contents of the shift register or the counter in part c) is 10111001. . The plaintext to encrypt and streamis 1001 0110 1100. You will be encrypting and sendingit in blocks of 4 bits at a time that is, you will encrypt 1011, then 0110, and then 1100). 10111001 Shift register/Counter (initial value) Key Your Banner D (modified as described above XOR used for "encryption" Select 4 bits Plaintext 1100 0110 1001 Give the ciphertext created for each of the following streaming modes. You are to show your work, giving the value of the following for each of the three plaintext blocks encrypted: Cipher key (that is, your modified Banner ID) Shift register/counter value The result of the "encryption" The 4-bit ciphertext created. a) Cipher Feedback Mode b) Output Feedback Mode 2. You are working for a company that provides security recommendations for a number of IT firms, each with different requirements and goals. For each of the following scenarios, give the transmission mode you would recommend or sending information, and why you would do so. a) Company A sends messages in blocks (that is, no streaming). These messages are very large, containing many repeated blocks. Speed of encryption/decryption is not a concern. They are willing to generate and send a new key for each message if necessary. b) Company G streams messages over a network. They are willing to generate and exchange a new key each time. To save time during encryption, they would like to have the ability to generate the entire key stream in advance (that is, before the actual message to be encrypted is known). c) Company Csends message in blocks (that is, no streaming). These messages are very short, consisting of few blocks, and are not sent very often. They also have parallel hardware that they would like to take advantage of in order to speed up the encryption/decryption process. They would like to avoid having to generate and exchange new keys for each message. d) Company D streams messages over a network. These messages are generally long and sent very often. They will not generate new keys for each message. They also have parallel hardware they would like to take advantage of, but are willing to sacrifice that speed for better security. Additional problem for Graduate Students: 3. Suppose that you are using CBC mode to send a message that consists of n blocks. Furthermore, suppose that thereis a transmission error in sending ciphertext block i to the recipient. Specifically, a single bit is changed due to noise (for example, a 1 in the ciphertext sent is changed to a 0 in the ciphertext received). Clearly, this will lead to an error in the plaintext block i that therecipient creates during decryption. How many other blocks will also be affected








