

1st excel file
2nd excl file
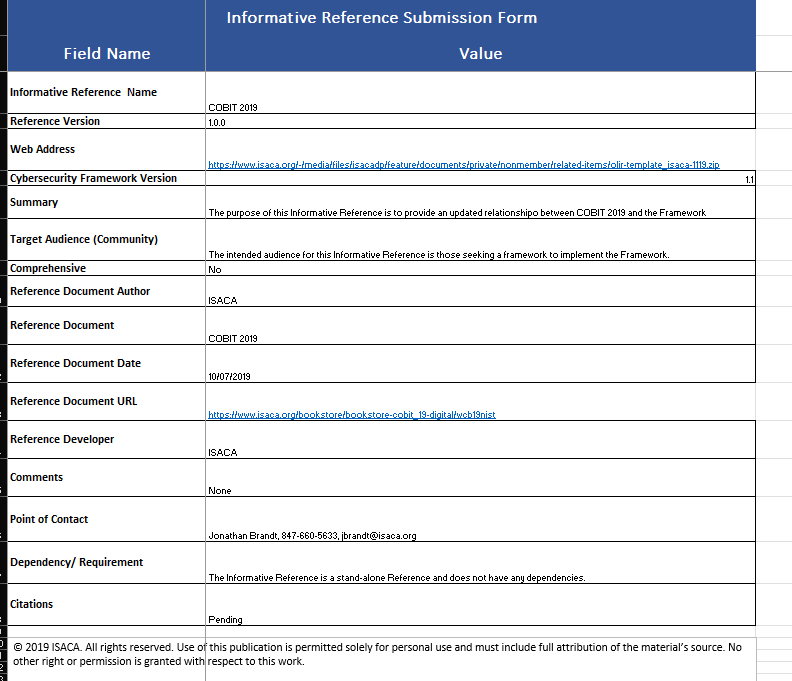
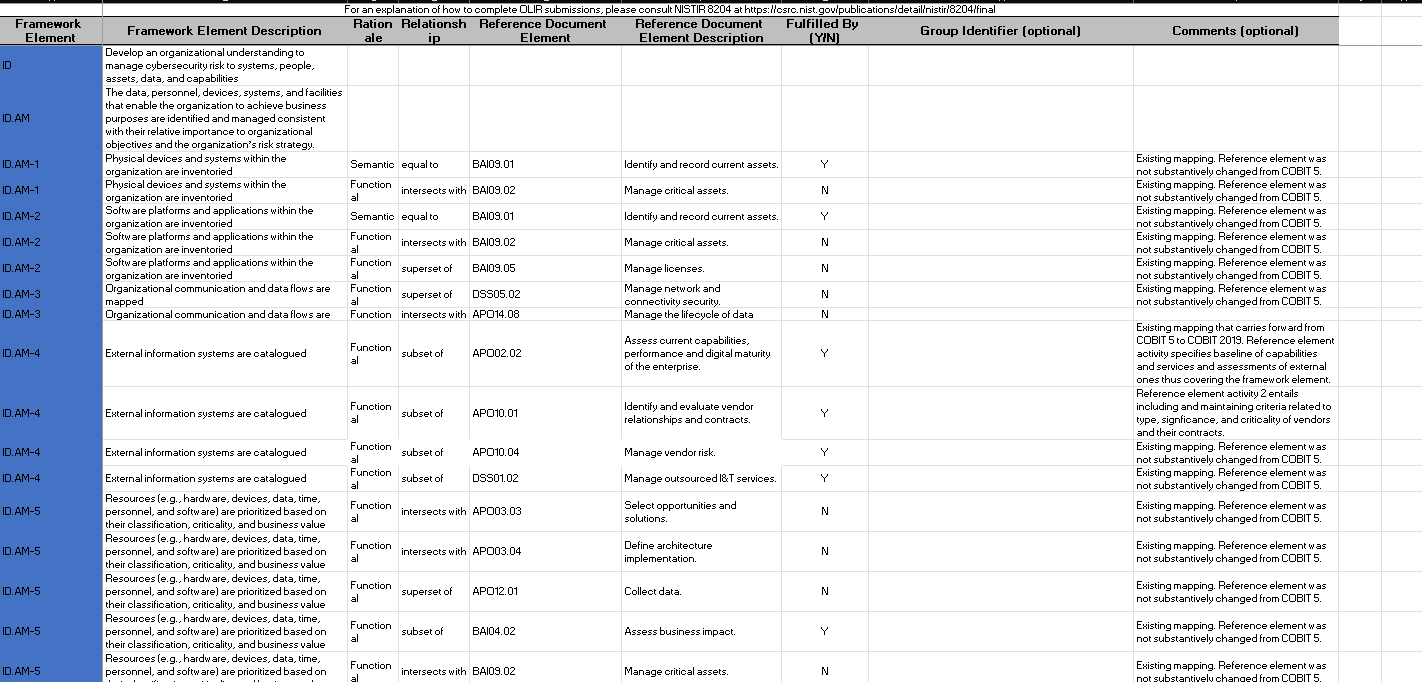
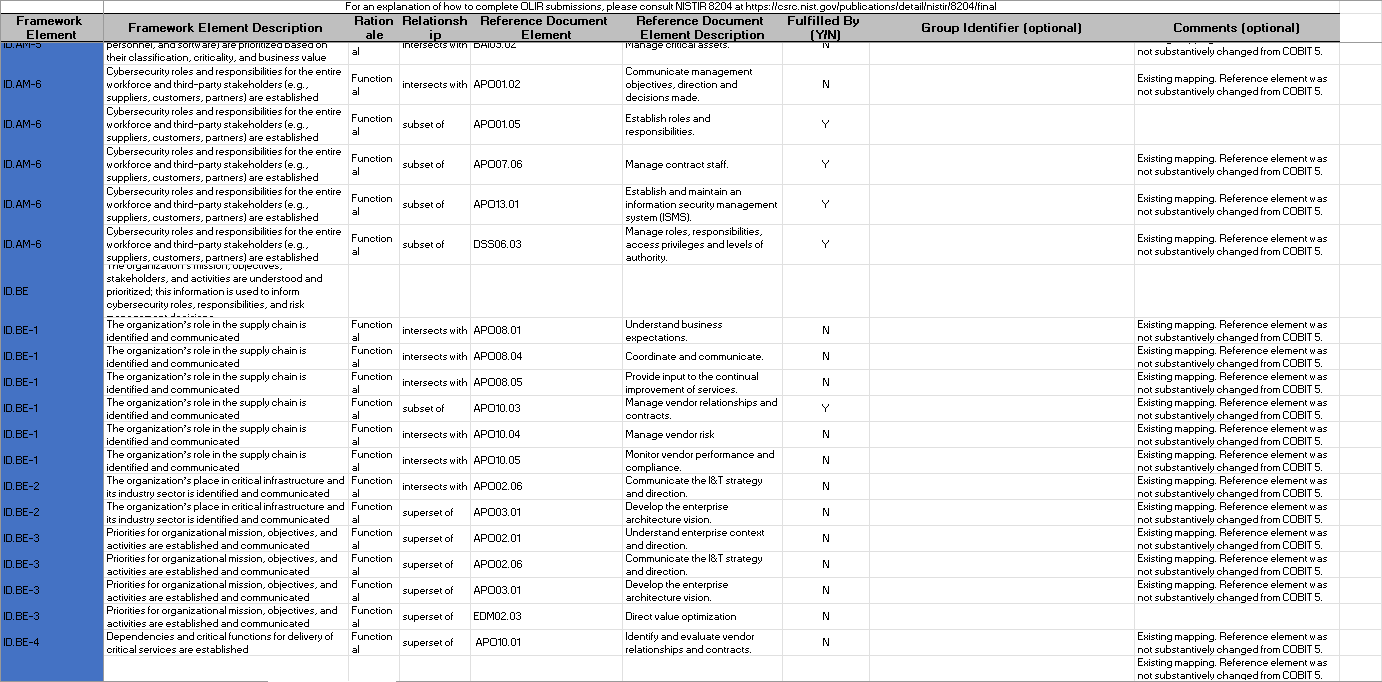
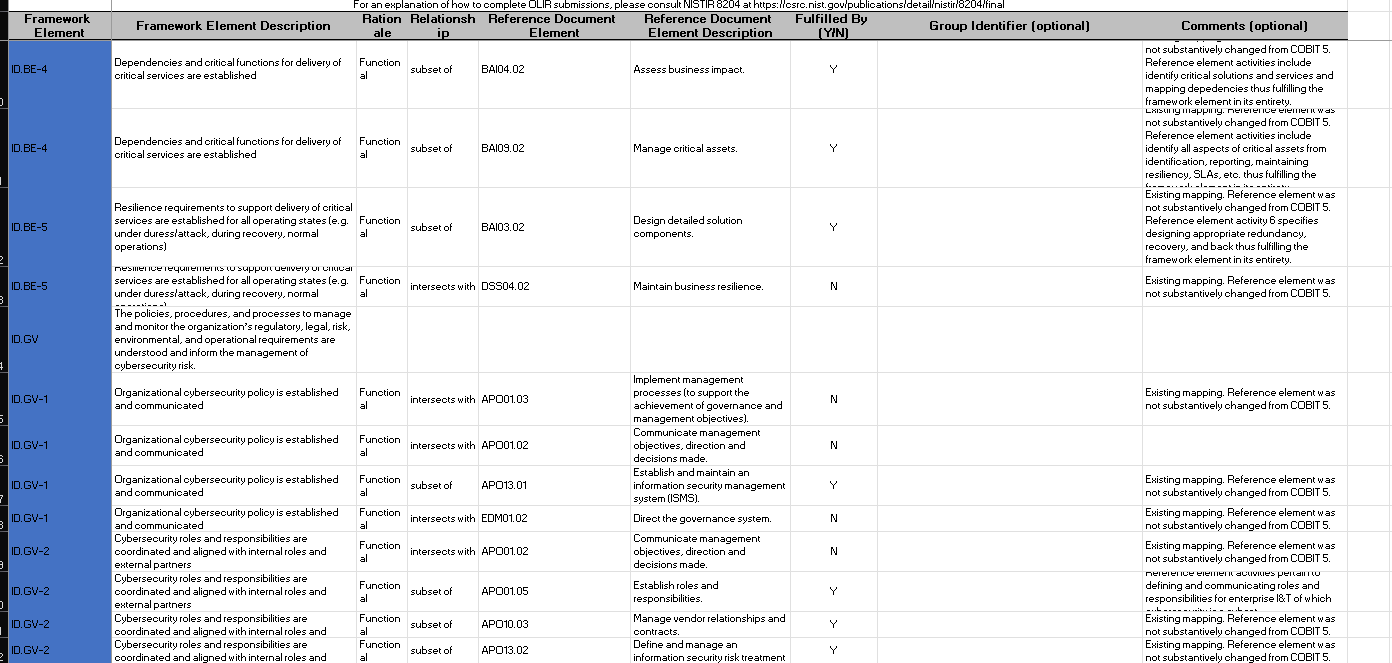
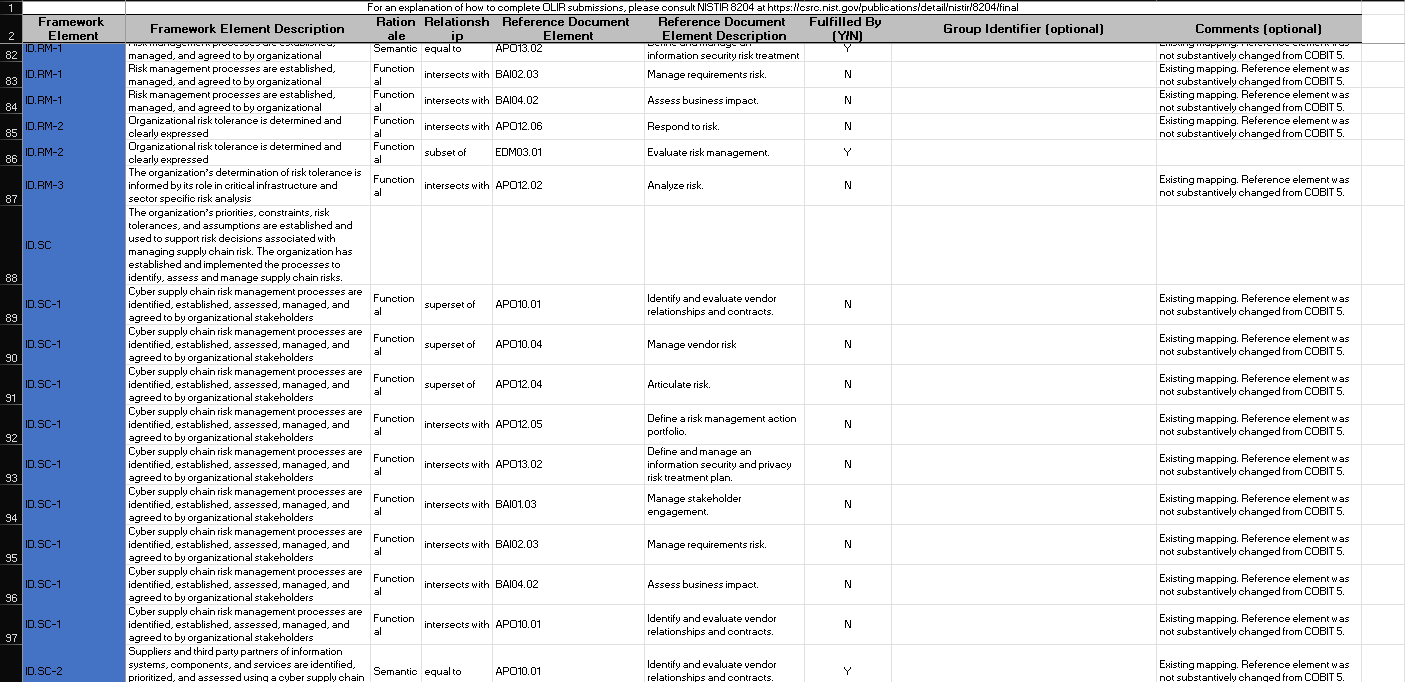
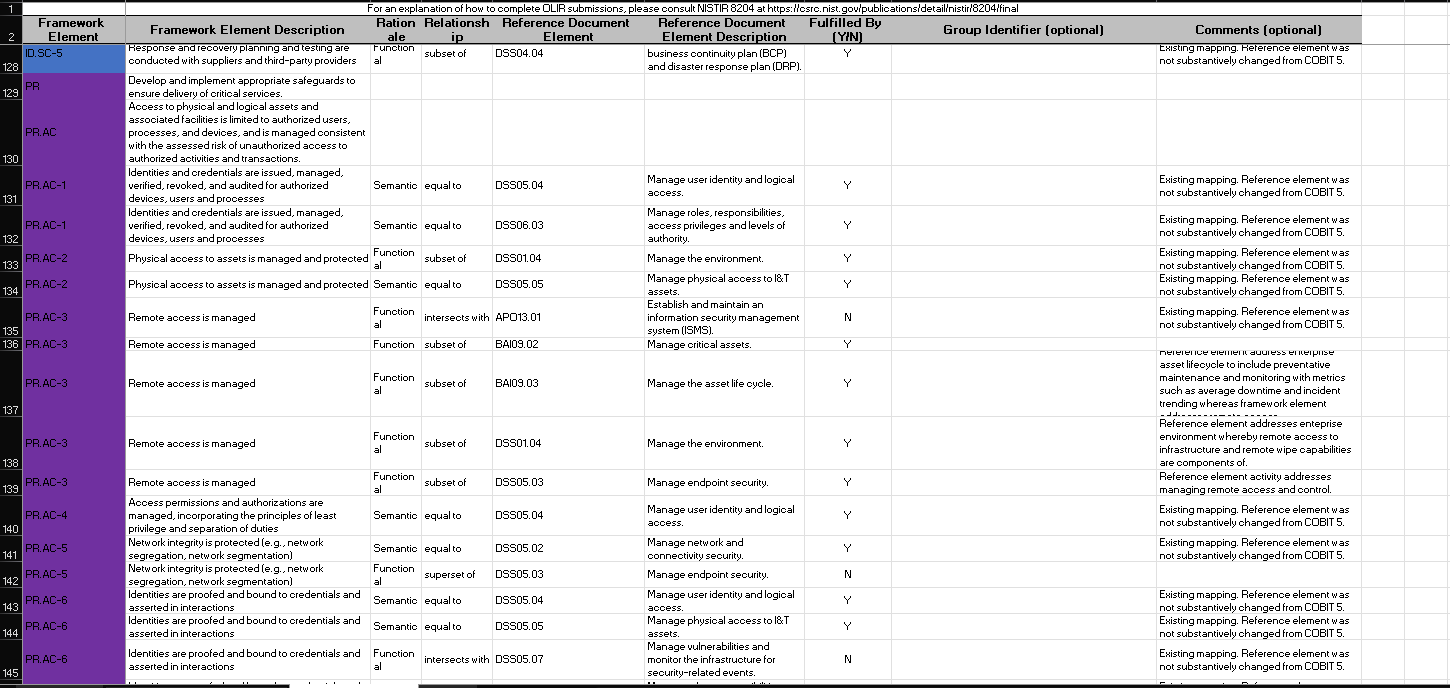
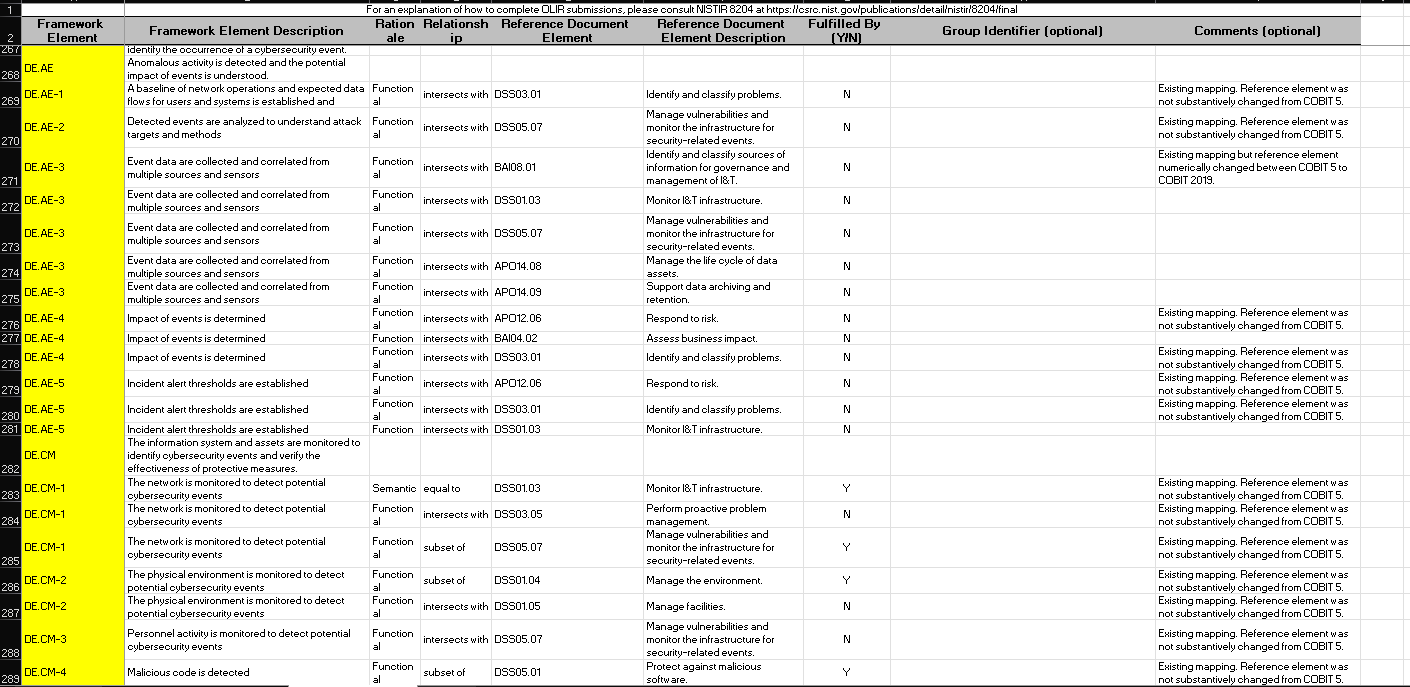
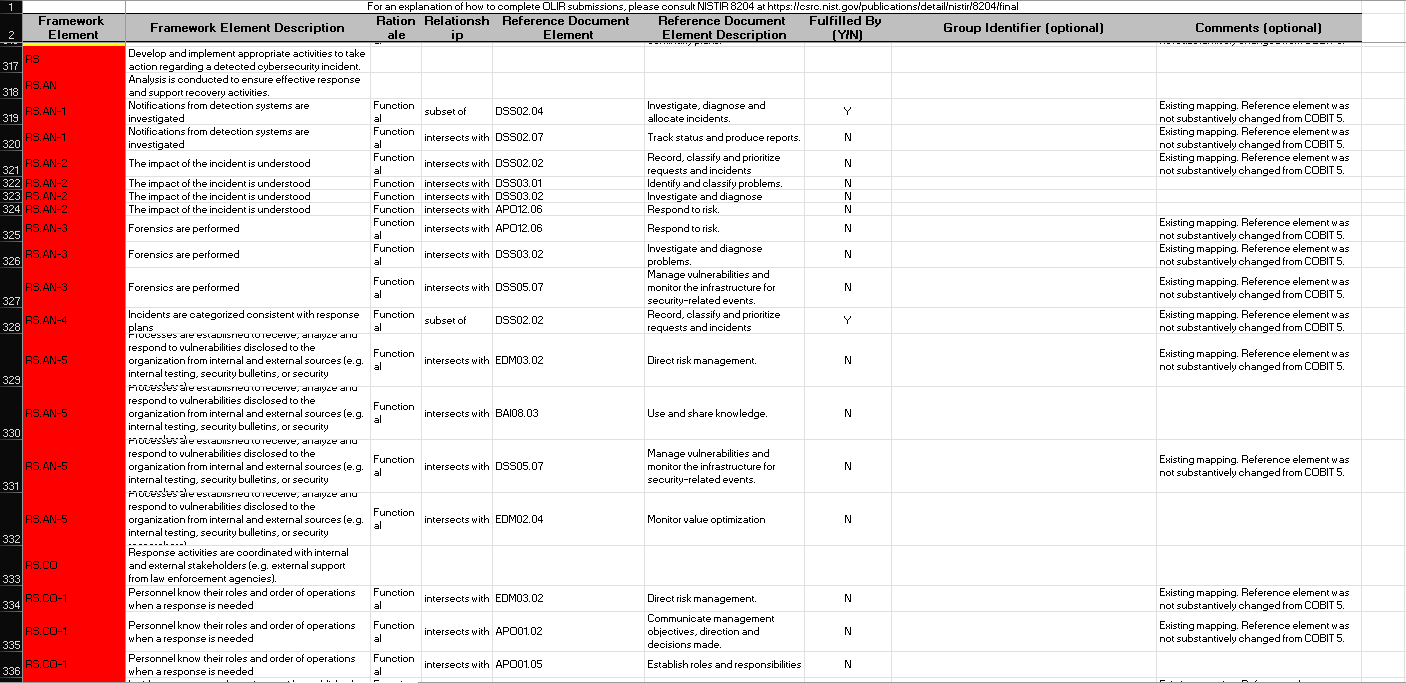
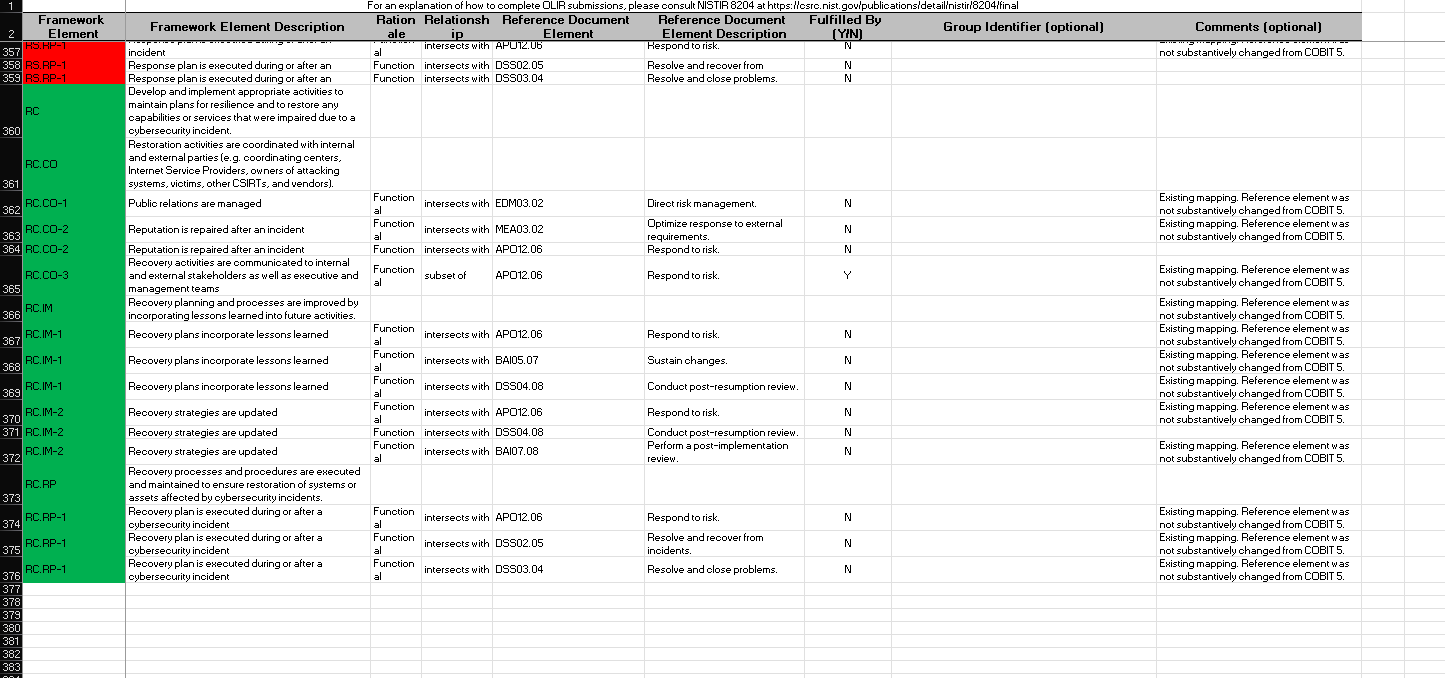
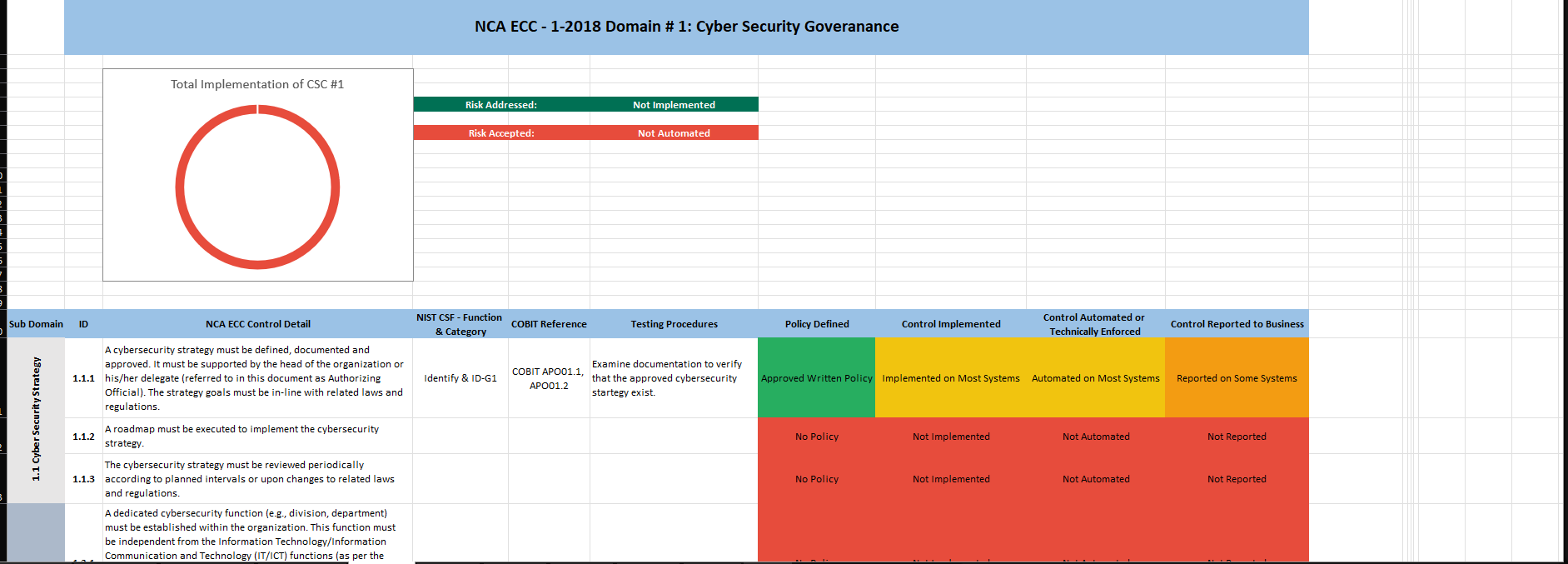
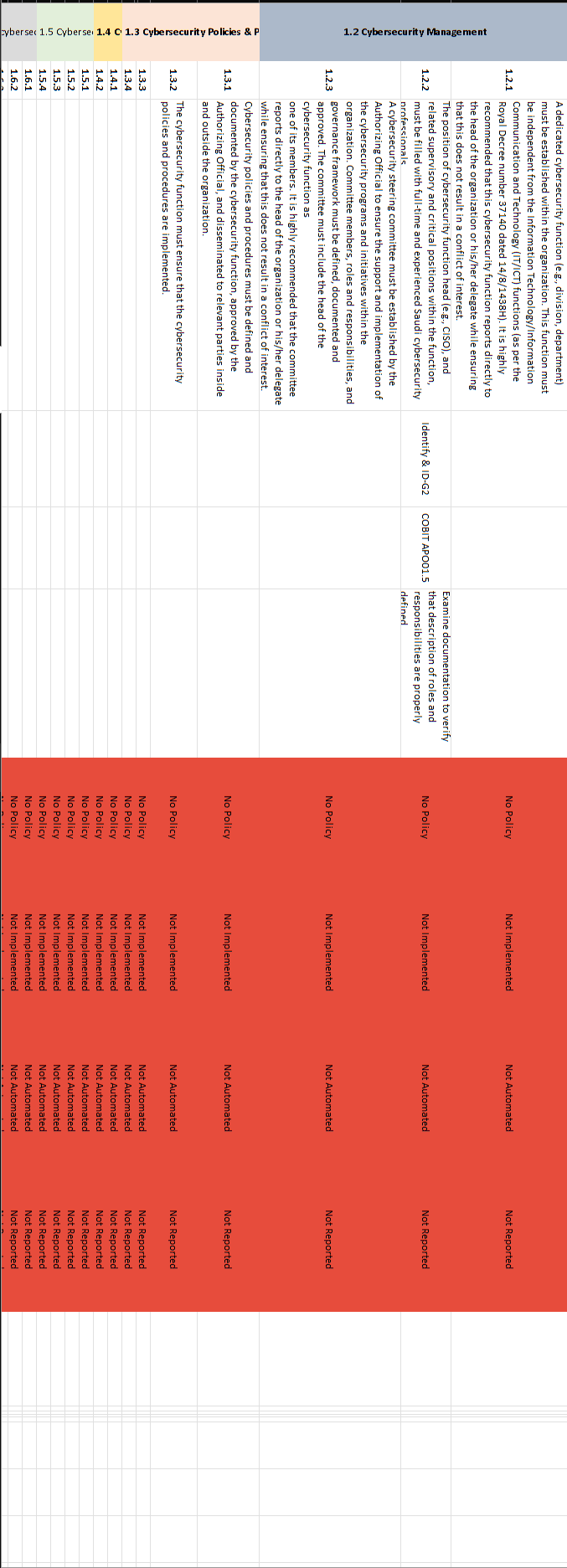
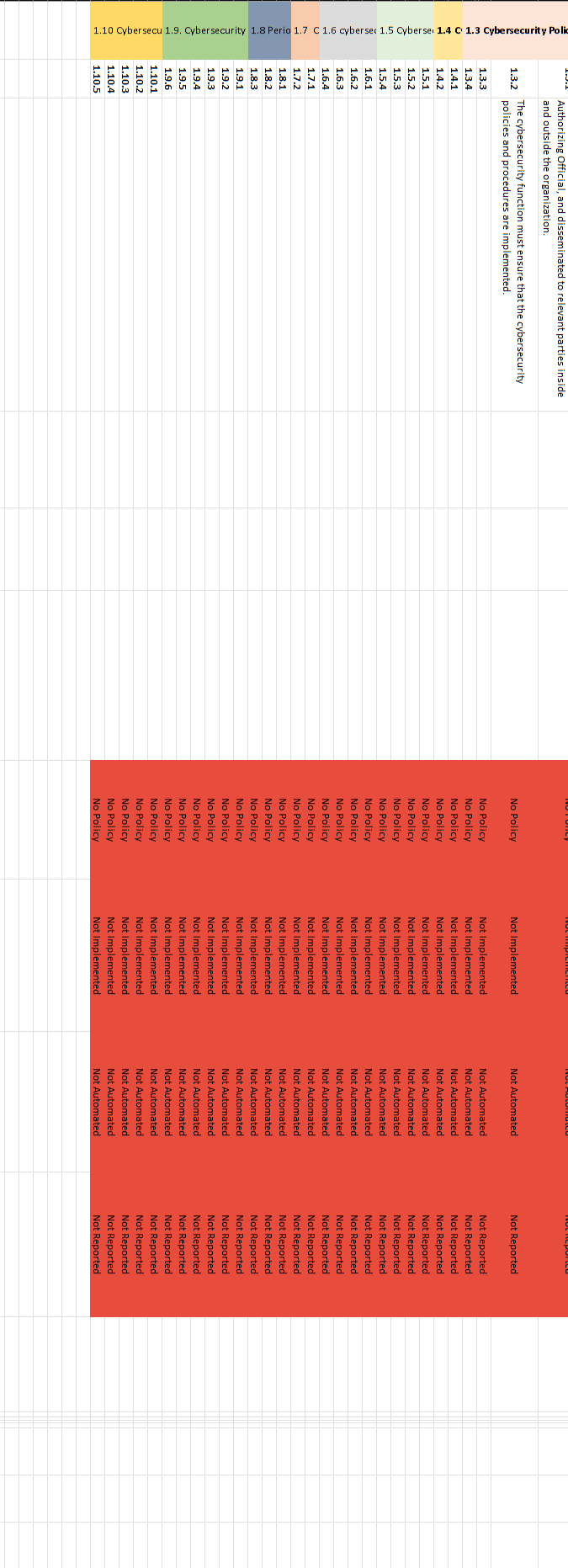
CPIS 606 - IT AUDIT Project Objectives: - Develop an IT Audit / Assessment tool based on NCA ECC -1-2018 - Mapping NCA ECC -1-2018 with NIST 800-53 and COBIT 2019 - Auditing NCA ECC -1-2018 controls Part 1: Develop an Audit/ Assessment Tool based on NCA ECC-1-2018 The purpose of this project is to provide organizations with a simple tool performing an Internal IT audit / assessment of their information assurance maturity level based on the controls defined by the NCA ECC -1-2018. The Essential Cybersecurity Controls consist of the following: - 5 Cybersecurity Main Domains. - 29 Cybersecurity Subdomains. - 114 Cybersecurity Controls. These cybersecurity controls are linked to related national and international law and regulatory requirements. The IT auditor should complete the answer to the drop-down menu questions lists on the Excel pages labeled ECC#1ECC \# 5. By choosing a drop-down choice for each critical control, the assessment tool will automatically generate scores and maturity level based on the answers to each question. Based on the answers to each question, the dashboard worksheet will automatically populate with the overall maturity level scores for the organization as a whole. These scores can therefore be used to measure the organization's progress and what percentage of the NCA ECC Controls they are currently following. Part 2: Conducting Audit/ Assessment In the second part of the project, you have to select any sub domain of NCA ECC -1-2018 and prepare an IT audit plan. Use the Internet to select an organization that appeals to you. The audit plan should include the following sections: - Introduction - Understanding the Business (Organization) - Defining the Audit Universe (Audit scope, Audit objectives, Relevant IT systems) - Performing a Risk Assessment - Formalizing the IT Audit Plan Resources: The following documents will be uploaded to the project folder on the blackboard. 1. Template (Excel) for developing IT Assessment tool. 2. NCA ECC 1-2018 3. NIST 80053 4. COBIT 2019 Submission: You are required to submit two documents. 1. IT Audit/ Assessment Tool (Excel) 2. IT Audit Plan (MS Word or PDF) NCA ECC - 1-2018 Domain \# 1: Cyber Security Goveranance Total Implementation of CSC \#1 manmin | 1 1 ImUUU!| 11 1.10 Cybersecu 1.9. Cybersecurity 1.8 Perio 1.7 C 1.6 cybersec 1.5 Cyberse, 1.4 C 1.3 Cybersecurity Pol: Informative Reference Submission Form Field Name Value Informative Reference Name COEIT 2019 Reference Version 1.0.0 Web Address hittpsidwuw.isaca.orod-tmediadfilestisacadpdeatureldocumentsporivatedonmemberdelated-itemstolir-template isaca-1119.zip Cybersecurity Framework Version Summary The purpose of this informative Reference is to provide an updated relationshipo between COBIT 2019 and the Framework Target Audience (Community) The intended audience for this Informative Reference is those seeking a framework to implement the Framework. \begin{tabular}{l|l} \hline Comprehensive & No \\ \hline \end{tabular} \begin{tabular}{l|l} Reference Document Author & ISACA \end{tabular} Reference Document COEIT 2019 Reference Document Date 1010712019 Reference Document URL Reference Developer ISACA Comments None Point of Contact Jonathan Brandt, 847-660-5633, jbrandt@isaca.org Dependency/ Requirement The Informative Reference is a stand-alone Reference and does not have any dependencies. Citations Pending (c) 2019 ISACA. All rights reserved. Use of this publication is permitted solely for personal use and must include full attribution of the material's source. No other right or permission is granted with respect to this work. For an explanation of how to complete [LIR submissions, please consult |NISTIR 8204 at https: Ilosre.nist.gow'publicationsidetailinistirl8204lfinal For an explanation of how to complete OLIR submissions, please consult NISTIR 8204 at https:/losre.nist. gowlpublicationsidetailistirl8204/final




















