Answered step by step
Verified Expert Solution
Question
1 Approved Answer
2. Score 9.9 Attack Vendor > Network. Attack vendor is Network because this Is a DNS traffic that can be intercepted many Hops away.
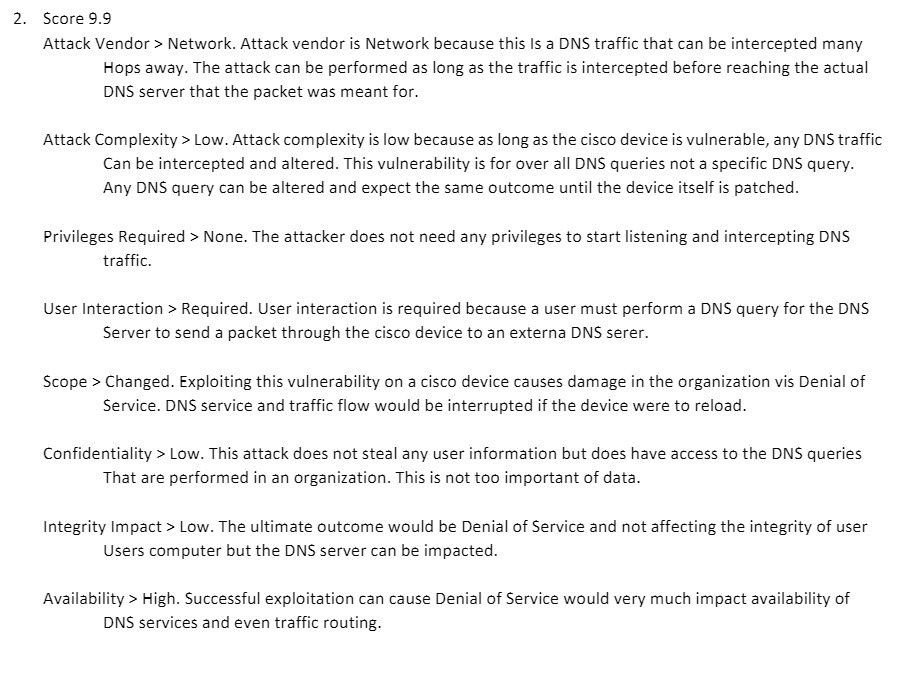
2. Score 9.9 Attack Vendor > Network. Attack vendor is Network because this Is a DNS traffic that can be intercepted many Hops away. The attack can be performed as long as the traffic is intercepted before reaching the actual DNS server that the packet was meant for. Attack Complexity > Low. Attack complexity is low because as long as the cisco device is vulnerable, any DNS traffic Can be intercepted and altered. This vulnerability is for over all DNS queries not a specific DNS query. Any DNS query can be altered and expect the same outcome until the device itself is patched. Privileges Required > None. The attacker does not need any privileges to start listening and intercepting DNS traffic. User Interaction > Required. User interaction is required because a user must perform a DNS query for the DNS Server to send a packet through the cisco device to an externa DNS serer. Scope > Changed. Exploiting this vulnerability on a cisco device causes damage in the organization vis Denial of Service. DNS service and traffic flow would be interrupted if the device were to reload. Confidentiality > Low. This attack does not steal any user information but does have access to the DNS queries That are performed in an organization. This is not too important of data. Integrity Impact > Low. The ultimate outcome would be Denial of Service and not affecting the integrity of user Users computer but the DNS server can be impacted. Availability > High. Successful exploitation can cause Denial of Service would very much impact availability of DNS services and even traffic routing.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


