Question: 22)b, c? 21. Encrypt the message this is an exercise using one of the following ciphers. Ignore the space between words. Decrypt the message to
22)b,c?
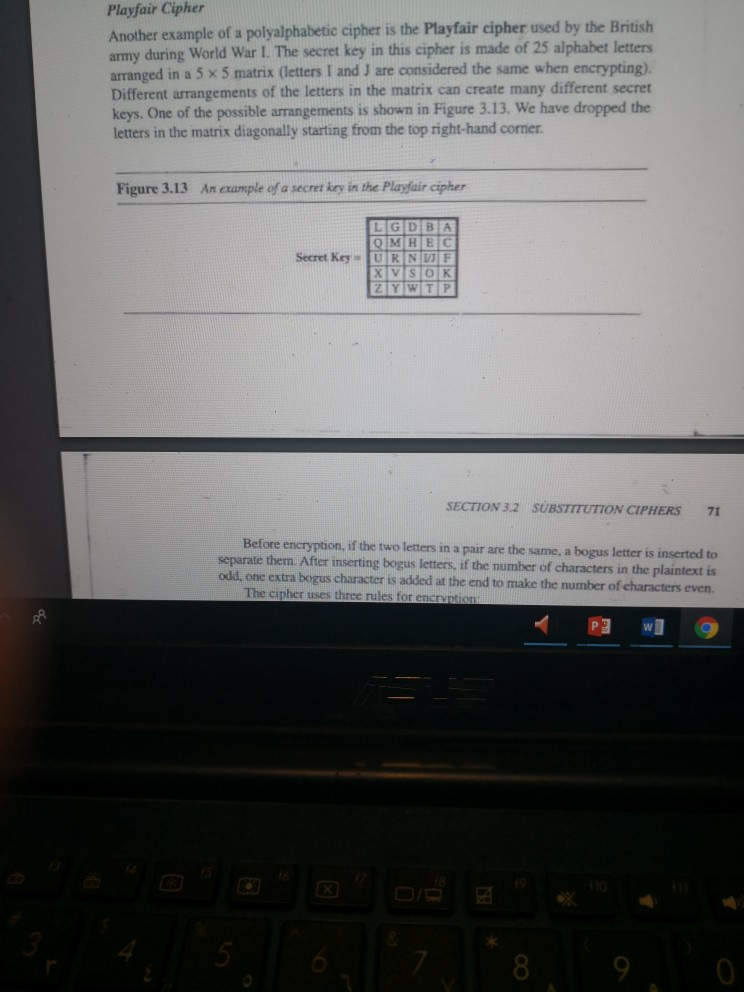
21. Encrypt the message "this is an exercise" using one of the following ciphers. Ignore the space between words. Decrypt the message to get the original plaintext. a. Additive cipher with key 20 b Multiplicative cipher with key 15 c. Affine cipher with key (15, 20) 22. Encrypt the message "the house is being sold tonight" using one of the following ciphers. Ignore the spac between words. Decrypt the message to get the plaintext: a. Vigenere cipher with key: "dollars" b. Autokey cipher with key -7 c. Playfair cipher with the key created in the text (see Figure 3.13) 23. Use the Vigenere cipher with keyword "HEATH" to encipher the message "Life is full of surprises" 24. Use the Playfair cipher to encipher the message "The key is hidden under pad". The secret key can be mde by filling the first and part of the second row with the word "GUIDANCE" and filling the rest of the matrix with the rest of the 25. Use a Hill cipher to encipher the message "We live in an insecure world". Use the following key K03 02 05 26. John is reading a mystery book involving cryplography. In one part of the book, and two paragraphis later the author tells the the author gives a ciphertext "CIW" two reader that this is a shift cipher and the plaintest is yes". In the next chapter, the hero found a tablet in a cave with "XVIEWYWr engraved on it. John immediately found the actual meaning of the ciphenext. What type of attack did John launch here? What is the plaintext? 9 0 Playfair Cipher Another example of a polyalphabetic cipher is the Playfair cipher used by the British army during World War I. The secret key in this cipher is made of 25 alphabet letters arranged in a 5 x 5 matrix (letters I and J are considered the same when encrypting). Different arrangements of the letters in the matrix can create many different secret letters in the matrix diagonally starting from the top right-hand corner Figure 3.13 An example of a secret key in the Playfair cipher LGDBA Secret Key SECTION 3.2 SUBSTITUTION CIPHERS 7 Before encryption, if the two letters in a pair are the same, a bogus letter is inserted to separate them. After inserting bogus letters, if the number of characters in the plaintext is odd, one extra bogus character is added at the end to make the number of characters even. The cipher uses three rules for encrvption
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


