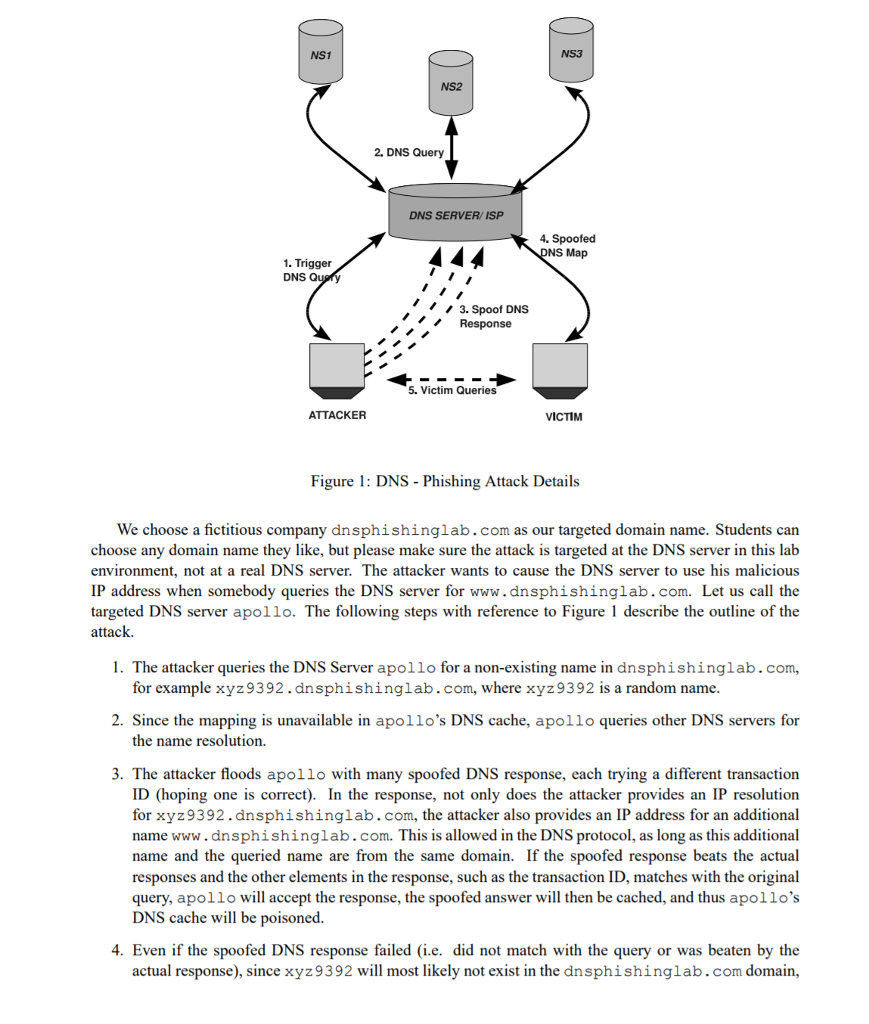


3 Lab Tasks: Pharming Attacks The main objective of Pharming attacks on a user is to redirect the user to another machine B when the user tries to get to machine A using As host name. For example, when the user tries to access the online banking, such as www.chase.com, if the adversaries can redirect the user to a malicious web site that looks very much like the main web site of www. chase.com, the user might be fooled and give away password of his/her online banking account. When a user types in www.chase.com in his browsers, the user's machine will issue a DNS query to find out the IP address of this web site. Attackers goal is to fool the user's machine with a faked DNS reply, which resolves www.chase.com to a malicious IP address. There are several ways to achieve such an attack. In the rest of the lab description, we will use www.example.com as the web site that the user wants to access, instead of using the real web site name www.chase.com; the example.com domain name is reserved for use in documentation, and is not owned by anybody. 3.1 Attackers have already compromised the victim's machine Modifying HOSTS file. The host name and IP address pairs in the HOSTS file (/etc/hosts) are used for local lookup; they take the preference over remote DNS lookups. For example, if there is a following entry in the HOSTS file in the user's computer, the www.example.com will be resolved as 1.2.3.4 in user's computer without asking any DNS server: 1.2.3.4 www.example.com Attacks. If attackers have compromised a user's machine, they can modify the HOSTS file to redirect the user to a malicious site whenever the user tries to access www.example.com. Assume that you have already compromised a machine, please try this technique to redirect www.example.com to any IP address that you choose. Note: /etc/hosts is ignored by the nslookup command, but will take effect on ping command and web browser etc. 3 Lab Tasks: Pharming Attacks The main objective of Pharming attacks on a user is to redirect the user to another machine B when the user tries to get to machine A using As host name. For example, when the user tries to access the online banking, such as www.chase.com, if the adversaries can redirect the user to a malicious web site that looks very much like the main web site of www. chase.com, the user might be fooled and give away password of his/her online banking account. When a user types in www.chase.com in his browsers, the user's machine will issue a DNS query to find out the IP address of this web site. Attackers goal is to fool the user's machine with a faked DNS reply, which resolves www.chase.com to a malicious IP address. There are several ways to achieve such an attack. In the rest of the lab description, we will use www.example.com as the web site that the user wants to access, instead of using the real web site name www.chase.com; the example.com domain name is reserved for use in documentation, and is not owned by anybody. 3.1 Attackers have already compromised the victim's machine Modifying HOSTS file. The host name and IP address pairs in the HOSTS file (/etc/hosts) are used for local lookup; they take the preference over remote DNS lookups. For example, if there is a following entry in the HOSTS file in the user's computer, the www.example.com will be resolved as 1.2.3.4 in user's computer without asking any DNS server: 1.2.3.4 www.example.com Attacks. If attackers have compromised a user's machine, they can modify the HOSTS file to redirect the user to a malicious site whenever the user tries to access www.example.com. Assume that you have already compromised a machine, please try this technique to redirect www.example.com to any IP address that you choose. Note: /etc/hosts is ignored by the nslookup command, but will take effect on ping command and web browser etc