Answered step by step
Verified Expert Solution
Question
1 Approved Answer
5- (4 points) Give specific examples (search the web) one for MIM and one for replay attacks and point out the specifics that make them
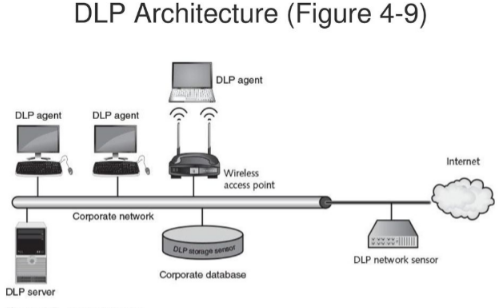
5- (4 points) Give specific examples (search the web) one for MIM and one for replay attacks and point out the specifics that make them MIM or replay. 6- (4 points) Examine and describe the concept of DLP and how it works, in your own words. Review the image of DLP architecture below and clearly identify (in the architecture) the vulnerabilities and how they can be exploited. DLP Architecture (Figure 4-9) 43 7- (8 points) You have learned that cryptography provides five (5) basic protections for information Pick fous protections and find an algorithm (under Cryptographic algorithms section) for each Describe briefly how the algorithm provides the desired protection. For example, if you want to provide Integrity, which cryptographic algorithm would you use? Why? 8- (6 points) Asymmetric cryptographic algorithms can be used to provide confidentiality and authenticity, as shown in the book (check the figures and explanations) Describe these two different uses of Asymmetric algorithms, specifically as it relates to the use of public and private keys, i.e. how are the two keys used (for each algorithm) to provide confidentiality or authenticity? 9- (4 points) What are the vulnerabilities of key storage? Be sure to explain the vulnerability for both software and hardware types. DLP Architecture (Figure 4-9) DLP agent DLP agent DLP agent Internet Wireless access point Corporate network DLP uongo warto Corporate database DLP network sensor DLP server
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


