Answered step by step
Verified Expert Solution
Question
1 Approved Answer
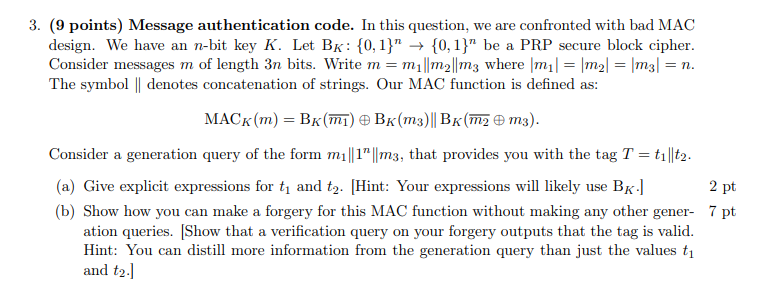
( 9 points ) Message authentication code. In this question, we are confronted with bad MAC design. We have an n - bit key K
points Message authentication code. In this question, we are confronted with bad MAC
design. We have an bit key Let : be a PRP secure block cipher.
Consider messages of length bits. Write where
The symbol denotes concatenation of strings. Our MAC function is defined as:
Consider a generation query of the form that provides you with the tag
a Give explicit expressions for and Hint: Your expressions will likely use
b Show how you can make a forgery for this MAC function without making any other gener
ation queries. Show that a verification query on your forgery outputs that the tag is valid.
Hint: You can distill more information from the generation query than just the values
and
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


