Question
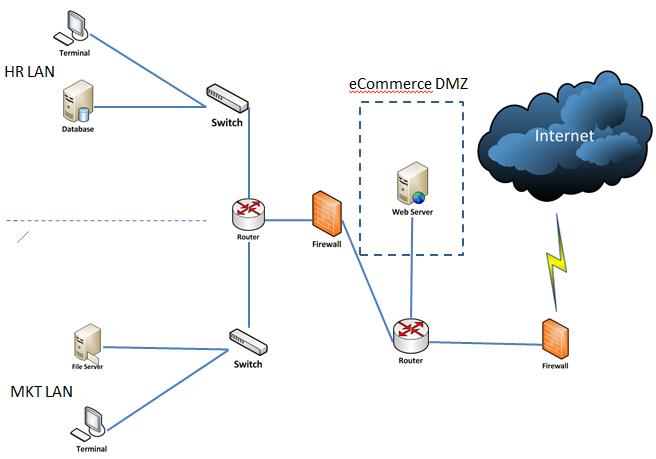
A small company is using the topology shown below to secure its intranet while providing a less-secured environment to its eCommerce DMZ server. The company
A small company is using the topology shown below to secure its intranet while providing a less-secured environment to its eCommerce DMZ server. The company is concerned that firewalls are not enough to detect and prevent network attacks. Hence, deployment of sensors to intrusion detection systems (IDS) and/or intrusion prevention systems (IPS) are needed in the network.
Company’s Requirements
Detect any malicious traffic entering the e-commerce server without performance penalty to traffic getting in the server from revenue-generating customers.
Stop any malicious traffic entering the human resources LAN (HR LAN).
Detect any malicious traffic entering the computer terminal in the marketing LAN (MKT LAN).
Stop any traffic entering the File Server in MKT LAN.
Deploy a centralized database and analysis console in the intranet to managing and monitoring both IDS and IPS sensors.
HR LAN Terminal Database File Server MKT LAN Terminal www. Switch Router Switch Firewall eCommerce DMZ H-N Web Server Router Internet Firewall
Step by Step Solution
There are 3 Steps involved in it
Step: 1
To meet the companys requirements the following network design with IDSIPS sensors is recommended Network Design Intranet The intranet consists of the HR LAN MKT LAN and File Server eCommerce DMZ The ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


