Answered step by step
Verified Expert Solution
Question
1 Approved Answer
answer all parts of assignment, Do NOT plagarise cache before cache after dont worry about it, was due 20 minutes ago Part 1. Exploring ARP
answer all parts of assignment, Do NOT plagarise 

cache before
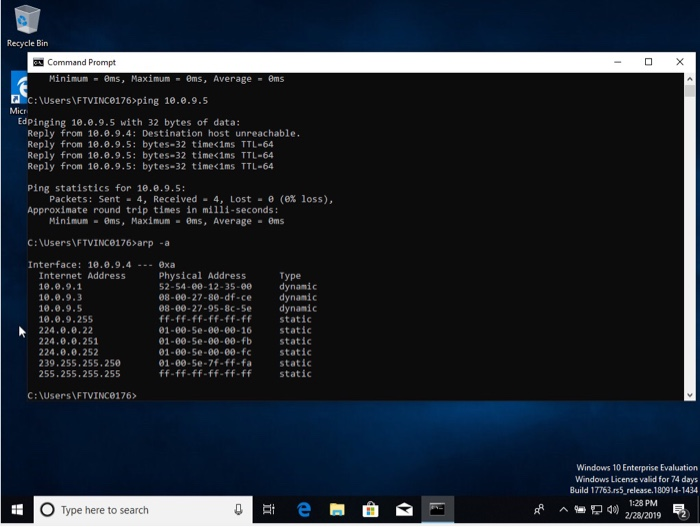
cache after
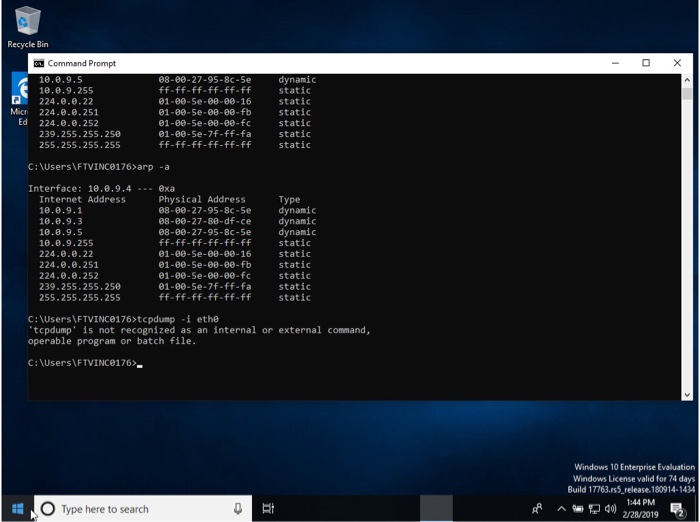
dont worry about it, was due 20 minutes ago
Part 1. Exploring ARP Spoofing Answer questions 1 and 2 based on Activity-4-ARP Spoofing. 1. [40 points] Explain what you noticed about difference between contents of victim's ARP cache in Step4 (before launching ARP spoofing) and Step 6 (after launching ARP spoofing). Use specific examples of ARP cache entries and support your answer with at least two screenshots comparing the ARP cache before and after ARP spoofing 2. [15] What packets in your trafficFile (created in step 7) are associated with the ARP cache poisoning? (Be specific about the packets. Mention their source, destination and the message they are carrying. Part 2. Studying a Real World Malware Emotet is an advanced banking Trojan that primarily functions as a downloader of other Trojans. According to the Symantec Internet security threat report, Emotet first emerged in 2014 and, after a quiet period, reappeared to make waves in the second half of 2017. Do some online search and answer the following questions about Emotet Use references to support your answers. 3. 15 points] Explain how the malware spread itself. In particular, do you think its spreading mechanism is like a worm or a virus? Justify your answer. 4 [15 points]Explain its concealment mechanisms. 5. [15 points] How does it work with a command and control (C&C) server? Recycle Bin Command Prompt Minimum ems, Maximum ms, Average ems c:VUsers\FTVINC0176>ping 10.0.9.5 Micr Edpinging 10.0.9.S with 32 bytes of data: Reply from 1..9.4: Destination host unreachable Reply from 1..9.5: bytes-32 timearp -a Interface: 18.0.9.4xa Internet Address 10.0.9.1 10.9.9.3 18.8.9.5 10.0.9.255 224.0.0.22 224.0.0.251 224.0.0.252 239.255.255.250 255.255.255.255 Physical Address 52-54-0e-12-35- dynamic 08-00-27-80-df-ce dynamic 08-00-27-95-8c-Se dynamic Type 01-00-Se-00-00-16 01-00-5e-00-00-fb 01-00-5e-00-00-fc 01-00-5e-7f-ff-fa static static static static static static C:\Users\FTVINC 176> Windows 10 Enterprise Evaluation Windows License valid for 74 days Build 17763rs5 release.180914-1434 Type here to search Recycle Bin Command Prompt 0.0.9.5 dynamic static static static static static static 08-00-27-95-8c-Se 10.0.9.255 Q' 224.0.0.22 Micn 224.0.0.251 Ed 224.8.8.252 01-00-5e-00-00-16 91-00-Se-08-00-fb 91-00-5e-00-00-fc 01-00-Se-7f-ff-fa 239.255.255.250 255.255.255.255 C:\Users\FTVINCe176>arp -a Interface: 10.0.9.4 exa Physical Address 08-00-27-95-8c-Se dynamic 88-80-27-88-df-ce dynamic 08-80-27-95-8c-Se Internet Address 10.0.9.1 10.0.9.3 10.8.9.5 10.0.9.255 224.0.0.22 224.0.0.251 224.0.0.252 239.255.255.250 255.255.255.255 Type 01-00-Se-00-00-16 01-0e-Se-00-e0-fb 01-00-Se-00-0e-fc 01-00-5e-7f-ff-fa dynamic static static static static static static C: \Users\FTVINCe176 tcpdump -i ethe tcpdump is not recognized as an internal or external command operable program or batch file C: \Users\FTV1Ncei 70% Windows 10 Enterprise Evaluation Windows License valid for 74 days Build 17763.rs5_release.180914-1434 O Type here to search 1:44 PM 2/28/2019 Part 1. Exploring ARP Spoofing Answer questions 1 and 2 based on Activity-4-ARP Spoofing. 1. [40 points] Explain what you noticed about difference between contents of victim's ARP cache in Step4 (before launching ARP spoofing) and Step 6 (after launching ARP spoofing). Use specific examples of ARP cache entries and support your answer with at least two screenshots comparing the ARP cache before and after ARP spoofing 2. [15] What packets in your trafficFile (created in step 7) are associated with the ARP cache poisoning? (Be specific about the packets. Mention their source, destination and the message they are carrying. Part 2. Studying a Real World Malware Emotet is an advanced banking Trojan that primarily functions as a downloader of other Trojans. According to the Symantec Internet security threat report, Emotet first emerged in 2014 and, after a quiet period, reappeared to make waves in the second half of 2017. Do some online search and answer the following questions about Emotet Use references to support your answers. 3. 15 points] Explain how the malware spread itself. In particular, do you think its spreading mechanism is like a worm or a virus? Justify your answer. 4 [15 points]Explain its concealment mechanisms. 5. [15 points] How does it work with a command and control (C&C) server? Recycle Bin Command Prompt Minimum ems, Maximum ms, Average ems c:VUsers\FTVINC0176>ping 10.0.9.5 Micr Edpinging 10.0.9.S with 32 bytes of data: Reply from 1..9.4: Destination host unreachable Reply from 1..9.5: bytes-32 timearp -a Interface: 18.0.9.4xa Internet Address 10.0.9.1 10.9.9.3 18.8.9.5 10.0.9.255 224.0.0.22 224.0.0.251 224.0.0.252 239.255.255.250 255.255.255.255 Physical Address 52-54-0e-12-35- dynamic 08-00-27-80-df-ce dynamic 08-00-27-95-8c-Se dynamic Type 01-00-Se-00-00-16 01-00-5e-00-00-fb 01-00-5e-00-00-fc 01-00-5e-7f-ff-fa static static static static static static C:\Users\FTVINC 176> Windows 10 Enterprise Evaluation Windows License valid for 74 days Build 17763rs5 release.180914-1434 Type here to search Recycle Bin Command Prompt 0.0.9.5 dynamic static static static static static static 08-00-27-95-8c-Se 10.0.9.255 Q' 224.0.0.22 Micn 224.0.0.251 Ed 224.8.8.252 01-00-5e-00-00-16 91-00-Se-08-00-fb 91-00-5e-00-00-fc 01-00-Se-7f-ff-fa 239.255.255.250 255.255.255.255 C:\Users\FTVINCe176>arp -a Interface: 10.0.9.4 exa Physical Address 08-00-27-95-8c-Se dynamic 88-80-27-88-df-ce dynamic 08-80-27-95-8c-Se Internet Address 10.0.9.1 10.0.9.3 10.8.9.5 10.0.9.255 224.0.0.22 224.0.0.251 224.0.0.252 239.255.255.250 255.255.255.255 Type 01-00-Se-00-00-16 01-0e-Se-00-e0-fb 01-00-Se-00-0e-fc 01-00-5e-7f-ff-fa dynamic static static static static static static C: \Users\FTVINCe176 tcpdump -i ethe tcpdump is not recognized as an internal or external command operable program or batch file C: \Users\FTV1Ncei 70% Windows 10 Enterprise Evaluation Windows License valid for 74 days Build 17763.rs5_release.180914-1434 O Type here to search 1:44 PM 2/28/2019 Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


