Question
Application #2 A Caesar cipher is a simple approach to encoding messages by shifting each letter in a message along the alphabet by a constant
Application #2
A Caesar cipher is a simple approach to encoding messages by shifting each letter in a message along the alphabet by a constant amount of k. For example, if k equals 3, then in an encoded message, each letter is shifted three characters forward: a is replaced with d, b with e, c with f and so on. The end of the alphabet wraps back around to the beginning. To decode the message each letter is shifted the same number of characters backwards. Julius Caesar actually used this type of cipher in some of his secret government correspondence. Unfortunately, the Caesar cipher is fairly easy to break. There are only 26 possibilities for shifting the characters, and the code can be broken by trying various key values until it works.
An improvement can be made to this encoding technique if we use a so called repeating key. Instead of shifting each character by a constant amount, we can shift each character by a different amount using a list of key values. If the message is longer that the list of key values, we just start using the key over again from the beginning. For example, if the key values are
3 1 7 4 2 5
then the first character is shifted by three, the second character by one, the third character by seven, etc. After shifting the sixth character by five, we start using the key over again. The seventh character is shifted by three, the eighth by one, etc. The following table shows the message knowledge is power encoded using this repeating key:
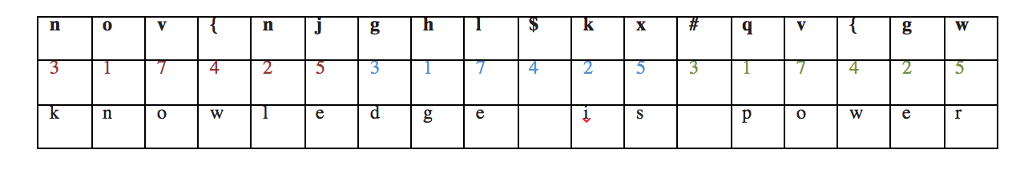
Notice that this encryption approach encodes the same letter into different characters, depending on where it occurs in the message and thus which key value is used to encode it.
Implement CircularArrayQueue class that uses a circular array with one unused location.
Next utilize this class to write a program(Cipher.java) that uses a repeating key to encode and decode a message. The keys of integer values are stored in a queue. After a key value is used, it is put back to the end of the queue so that the key continually repeats as needed for long messages. The key can use both positive and negative values. The idea is that the person encoding the message has one copy of the key, and the person decoding the message has another. Using a queue to store the repeating key makes it easy to repeat the key and the nature of the queue keeps the key values in the proper order.
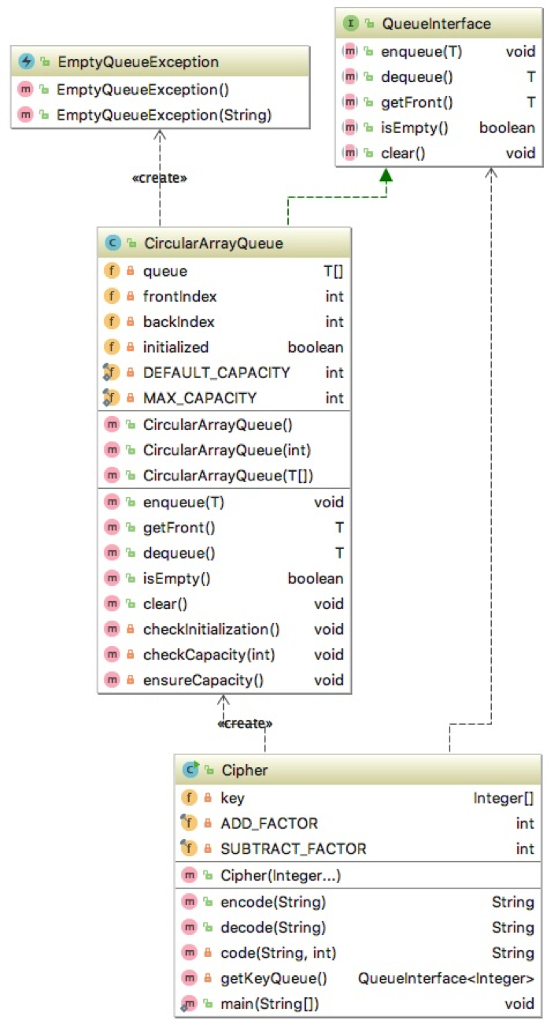
public class Cipher { private Integer[] key; private final int ADD_FACTOR = 1; private final int SUBTRACT_FACTOR = -1; public Cipher(Integer... key) { // TODO Project 2B } public String encode(String message) { // TODO Project 2B //calls code method with ADD_FACTOR return "???"; } public String decode(String encoded) { // TODO Project 2B //calls code method with SUBTRACT_FACTOR return "???"; } private String code(String message, int addOrSubtractFactor) { StringBuilder encoded = new StringBuilder(); // TODO Project 2B // calls getKeyQueue to get the queue for encoding and decoding return encoded.toString(); } private QueueInterface getKeyQueue() { // TODO Project 2B return null; // THIS IS A STUB } public static void main(String args[]) { System.out.println("************** TESTING THE CIPHER ************** "); Cipher cipher = new Cipher(5, 12, -3, 8, -9, 4, 10, 2, 3, 5, 1); String encoded = cipher.encode("All programmers are playwrights and all computers are lousy actors."); System.out.println("--->The original message encoded is:"); System.out.println(encoded); String decoded = cipher.decode(encoded); System.out.println("--->The original message decoded is:"); System.out.println(decoded); encoded = cipher.encode("There is no elevator to success, You have to take the stairs..."); System.out.println(" --->The original message encoded is:"); System.out.println(encoded); decoded = cipher.decode(encoded); System.out.println("--->The original message decoded is:"); System.out.println(decoded); cipher = new Cipher(3, 1, 7, 4, 2, 5); encoded = cipher.encode("Trust but Verify"); System.out.println(" --->The original message encoded is:"); System.out.println(encoded); decoded = cipher.decode(encoded); System.out.println("--->The original message decoded is:"); System.out.println(decoded); encoded = cipher.encode("race car"); System.out.println(" --->The original message encoded is:"); System.out.println(encoded); decoded = cipher.decode(encoded); System.out.println("--->The original message decoded is:"); System.out.println(decoded); } } public class CircularArrayQueueimplements QueueInterface { private T[] queue; // Circular array of queue entries and one unused location private int frontIndex; // Index of front entry private int backIndex; // Index of back entry private boolean initialized = false; private static final int DEFAULT_CAPACITY = 3; private static final int MAX_CAPACITY = 10000; public CircularArrayQueue() { this(DEFAULT_CAPACITY); } // end default constructor public CircularArrayQueue(int initialCapacity) { checkCapacity(initialCapacity); // The cast is safe because the new array contains null entries @SuppressWarnings("unchecked") T[] tempQueue = (T[]) new Object[initialCapacity + 1]; this.queue = tempQueue; this.frontIndex = 0; this.backIndex = initialCapacity; this.initialized = true; } // end constructor public CircularArrayQueue(T[] initialContent) { // TODO Project 2A } // end constructor public void enqueue(T newEntry) { //System.out.println("enqueue(" + newEntry + ")"); // ***TESTING // TODO Project 2A //System.out.println("queue[" + backIndex + "] = " + newEntry); // ***TESTING } // end enqueue public T getFront() throws EmptyQueueException { // TODO Project 2A return null; } // end getFront public T dequeue() throws EmptyQueueException { // TODO Project 2A return null; } // end dequeue public boolean isEmpty() { // TODO Project 2A return true; // THIS IS A STUB } // end isEmpty public void clear() { // null out only the used slots // TODO Project 2A } // end clear // Throws an exception if this object is not initialized. private void checkInitialization() { if (!this.initialized) throw new SecurityException("CircularArrayQueue object is not initialized properly."); } // end checkInitialization // Throws an exception if the client requests a capacity that is too large. private void checkCapacity(int capacity) { if (capacity > MAX_CAPACITY) throw new IllegalStateException("Attempt to create a queue " + "whose capacity exceeds " + "allowed maximum."); } // end checkCapacity // Doubles the size of the array queue if it is full. // Precondition: checkInitialization has been called. private void ensureCapacity() { // TODO Project 2A } // end ensureCapacity }
SAMPLE RUN:
************** TESTING THE CIPHER **************
--->The original message encoded is:
Fxi(gvyiufnrqo{e|g#umftz`krvv%bspicp*errqzbzj$kth%mtpemvrwt3
--->The original message decoded is:
All programmers are playwrights and all computers are lousy actors.
--->The original message encoded is:
Ytbz\$su#sp%qimme~qu%ut,p}Zgouv1!^{r(_eg#yp%^s\$~jh%tymfzj280
--->The original message decoded is:
There is no elevator to success, You have to take the stairs...
--->The original message encoded is:
Ws|wv%ev{$Xjujm}
--->The original message decoded is:
Trust but Verify
--->The original message encoded is:
ubji"hds
--->The original message decoded is:
race car
Process finished with exit code 0
10 3 17425 3 17 4 2 53 7 4 25Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


