Question
Assignment 5 - Text Processing PYTHON 3 Make sure you have read and understood both m odules A and B this week, and module 2R
Assignment 5 - Text Processing PYTHON 3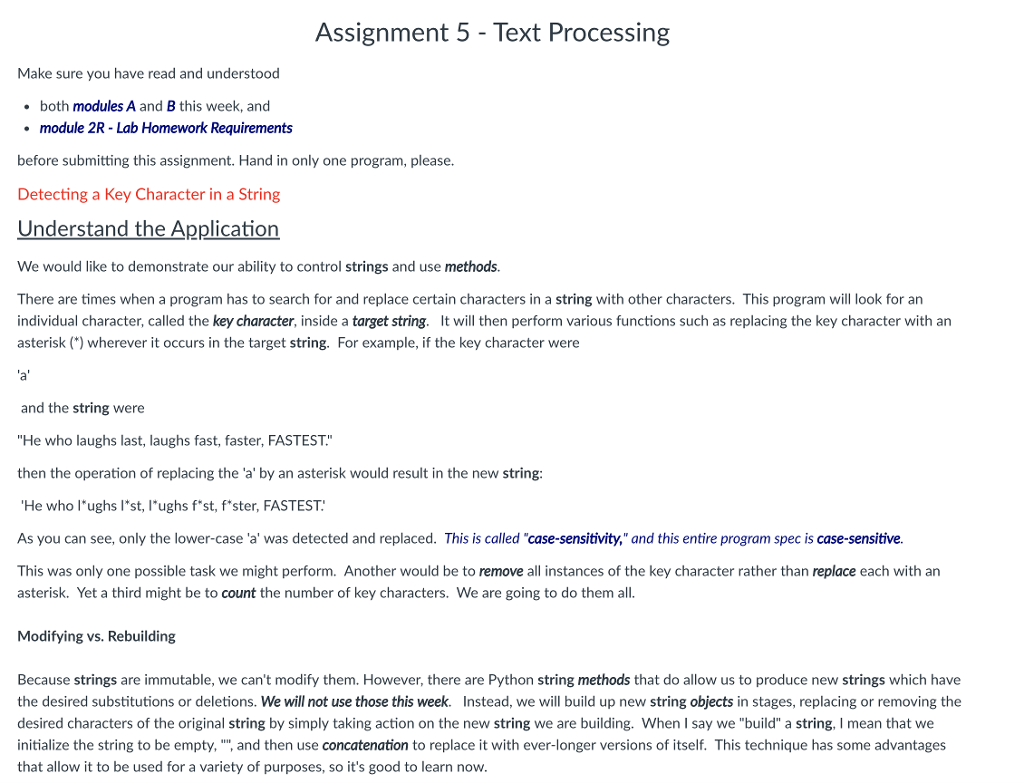
Make sure you have read and understood
both modules A and B this week, and
module 2R - Lab Homework Requirements
before submitting this assignment. Hand in only one program, please.
Detecting a Key Character in a String
Understand the Application
We would like to demonstrate our ability to control strings and use methods.
There are times when a program has to search for and replace certain characters in a string with other characters. This program will look for an individual character, called the key character, inside a target string. It will then perform various functions such as replacing the key character with an asterisk (*) wherever it occurs in the target string. For example, if the key character were
'a'
and the string were
"He who laughs last, laughs fast, faster, FASTEST."
then the operation of replacing the 'a' by an asterisk would result in the new string:
'He who l*ughs l*st, l*ughs f*st, f*ster, FASTEST.'
As you can see, only the lower-case 'a' was detected and replaced. This is called "case-sensitivity," and this entire program spec is case-sensitive.
This was only one possible task we might perform. Another would be to remove all instances of the key character rather than replace each with an asterisk. Yet a third might be to count the number of key characters. We are going to do them all. Modifying vs. Rebuilding Because strings are immutable, we can't modify them. However, there are Python string methods that do allow us to produce new strings which have the desired substitutions or deletions. We will not use those this week. Instead, we will build up new string objects in stages, replacing or removing the desired characters of the original string by simply taking action on the new string we are building. When I say we "build" a string, I mean that we initialize the string to be empty, "", and then use concatenation to replace it with ever-longer versions of itself. This technique has some advantages that allow it to be used for a variety of purposes, so it's good to learn now.
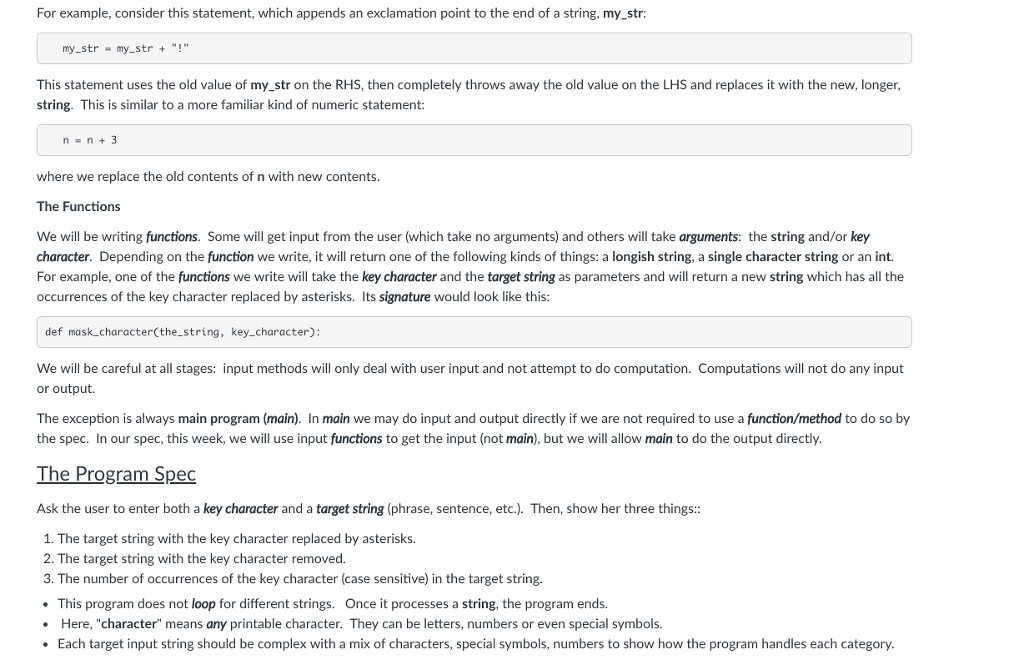
For example, consider this statement, which appends an exclamation point to the end of a string, my_str:
my_str = my_str + "!"
This statement uses the old value of my_str on the RHS, then completely throws away the old value on the LHS and replaces it with the new, longer, string. This is similar to a more familiar kind of numeric statement:
n = n + 3
where we replace the old contents of n with new contents.
The Functions
We will be writing functions. Some will get input from the user (which take no arguments) and others will take arguments: the string and/or key character. Depending on the function we write, it will return one of the following kinds of things: a longish string, a single character string or an int. For example, one of the functions we write will take the key character and the target string as parameters and will return a new string which has all the occurrences of the key character replaced by asterisks. Its signature would look like this:
def mask_character(the_string, key_character):
We will be careful at all stages: input methods will only deal with user input and not attempt to do computation. Computations will not do any input or output.
The exception is always main program (main). In main we may do input and output directly if we are not required to use a function/method to do so by the spec. In our spec, this week, we will use input functions to get the input (not main), but we will allow main to do the output directly.
The Program Spec
Ask the user to enter both a key character and a target string (phrase, sentence, etc.). Then, show her three things::
The target string with the key character replaced by asterisks.
The target string with the key character removed.
The number of occurrences of the key character (case sensitive) in the target string.
This program does not loop for different strings. Once it processes a string, the program ends.
Here, "character" means any printable character. They can be letters, numbers or even special symbols.
Each target input string should be complex with a mix of characters, special symbols, numbers to show how the program handles each category.
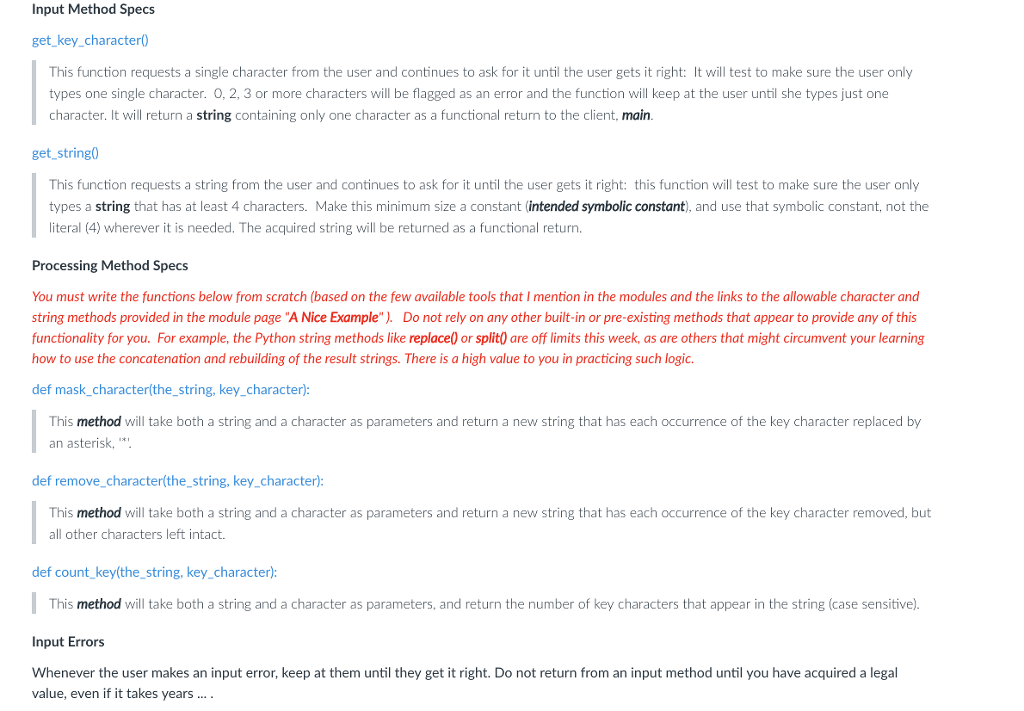
Input Method Specs
get_key_character()
This function requests a single character from the user and continues to ask for it until the user gets it right: It will test to make sure the user only types one single character. 0, 2, 3 or more characters will be flagged as an error and the function will keep at the user until she types just one character. It will return a string containing only one character as a functional return to the client, main.
get_string()
This function requests a string from the user and continues to ask for it until the user gets it right: this function will test to make sure the user only types a string that has at least 4 characters. Make this minimum size a constant (intended symbolic constant), and use that symbolic constant, not the literal (4) wherever it is needed. The acquired string will be returned as a functional return.
Processing Method Specs
You must write the functions below from scratch (based on the few available tools that I mention in the modules and the links to the allowable character and string methods provided in the module page "A Nice Example" ). Do not rely on any other built-in or pre-existing methods that appear to provide any of this functionality for you. For example, the Python string methods like replace() or split() are off limits this week, as are others that might circumvent your learning how to use the concatenation and rebuilding of the result strings. There is a high value to you in practicing such logic.
def mask_character(the_string, key_character):
This method will take both a string and a character as parameters and return a new string that has each occurrence of the key character replaced by an asterisk, '*'.
def remove_character(the_string, key_character):
This method will take both a string and a character as parameters and return a new string that has each occurrence of the key character removed, but all other characters left intact.
def count_key(the_string, key_character):
This method will take both a string and a character as parameters, and return the number of key characters that appear in the string (case sensitive).
Input Errors
Whenever the user makes an input error, keep at them until they get it right. Do not return from an input method until you have acquired a legal value, even if it takes years ... .
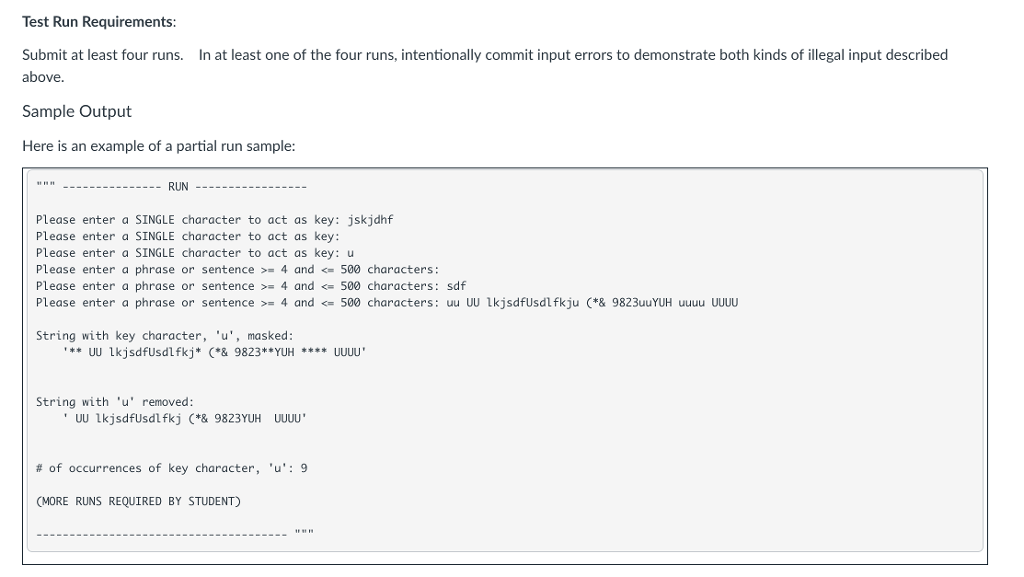
Test Run Requirements:
Submit at least four runs. In at least one of the four runs, intentionally commit input errors to demonstrate both kinds of illegal input described above.
Sample Output
Here is an example of a partial run sample:
""" --------------- RUN ----------------- Please enter a SINGLE character to act as key: jskjdhf Please enter a SINGLE character to act as key: Please enter a SINGLE character to act as key: u Please enter a phrase or sentence >= 4 and = 4 and = 4 andOnce your assignment is graded and returned, you can view the instructor solution here:
Quiz List
Your access code will be provided in your graded assignment comments. Find the assignment in the list, click "Take Survey" and you will see the solution. Even though it is called a "Quiz," it is actually just a solution; there is no need to submit anything, just open the quiz and see the solution.
Assignment 5 - Text Processing Make sure you have read and understood both modules A and B this week, and module 2R - Lab Homework Requirements before submitting this assignment. Hand in only one program, please. Detecting a Key Character in a String Understand the Application We would like to demonstrate our ability to control strings and use methods. There are times when a program has to search for and replace certain characters in a string with other characters. This program will look for an individual character, called the key character, inside a target string. It will then perform various functions such as replacing the key character with an asterisk () wherever it occurs in the target string. For example, if the key character were a' and the string were He who laughs last, laughs fast, faster, FASTEST." then the operation of replacing the 'a' by an asterisk would result in the new string He who lughs I'st, lughs f st, f*ster, FASTEST As you can see, only the lower-case 'a' was detected and replaced. This is called "case-sensitivity," and this entire program spec is case-sensitive. This was only one possible task we might perform. Another would be to remove all instances of the key character rather than replace each with an asterisk. Yet a third might be to count the number of key characters. We are going to do them all. Modifying vs. Rebuilding Because strings are immutable, we can't modify them. However, there are Python string methods that do allow us to produce new strings which have the desired substitutions or deletions. We will not use those this week. Instead, we will build up new string objects in stages, replacing or removing the desired characters of the original string by simply taking action on the new string we are building. When I say we "build" a string, I mean that we initialize the string to be empty, "", and then use concatenation to replace it with ever-longer versions of itself. This technique has some advantages that allow it to be used for a variety of purposes, so it's good to learn now
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


