Question
Assignment: Question 1: For the Linux command useradd, you used aflag -m. What does the -m flag do? Question 2: Which Windows passwords were cracked
 Assignment:
Assignment:
Question 1: For the Linux command useradd, you used aflag -m. What does the -m flag do?
Question 2: Which Windows passwords were cracked using hashcatand how long did it take?
Question 3: Which Linux passwords were cracked using John theRipper and how long did it take?
Question 4: Which Windows passwords were cracked using John theRipper and how long did it take?
Question 5: Which Windows passwords were cracked using theonline Rainbow Tables?
Question 6: Can crackstation crack the Kali Linux passwords? Whyor why not? (This requires some research and explanation!).
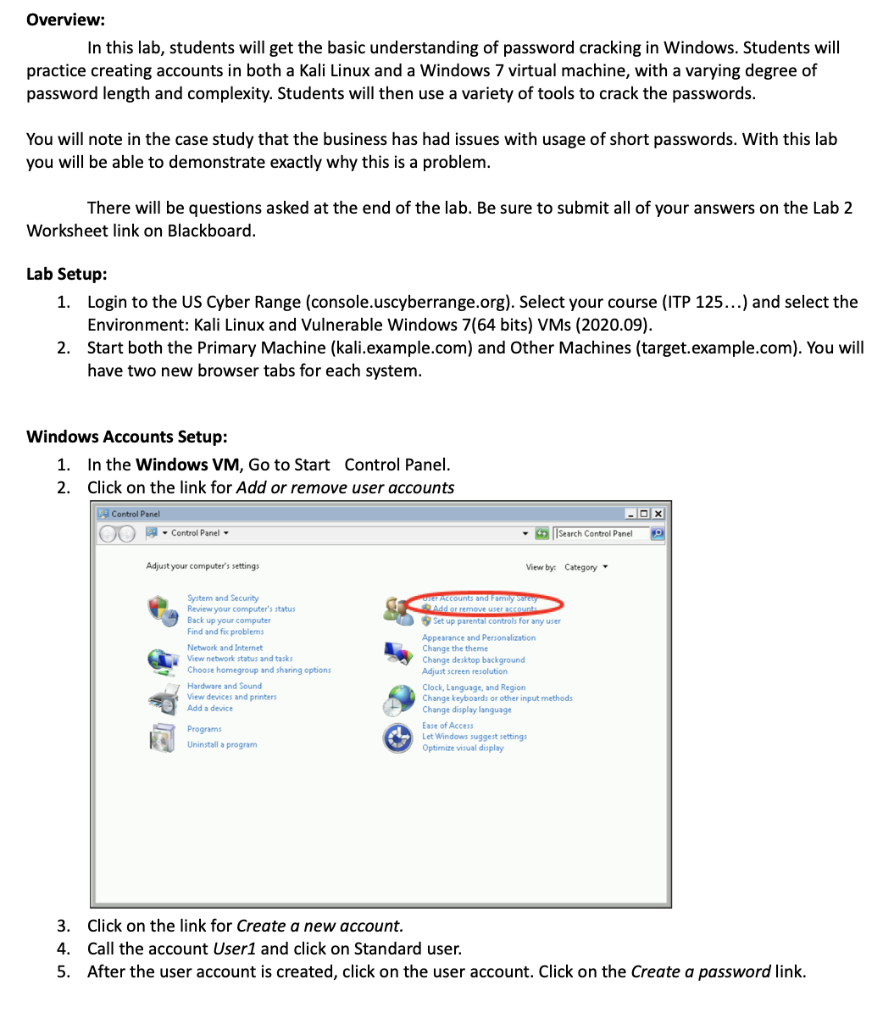
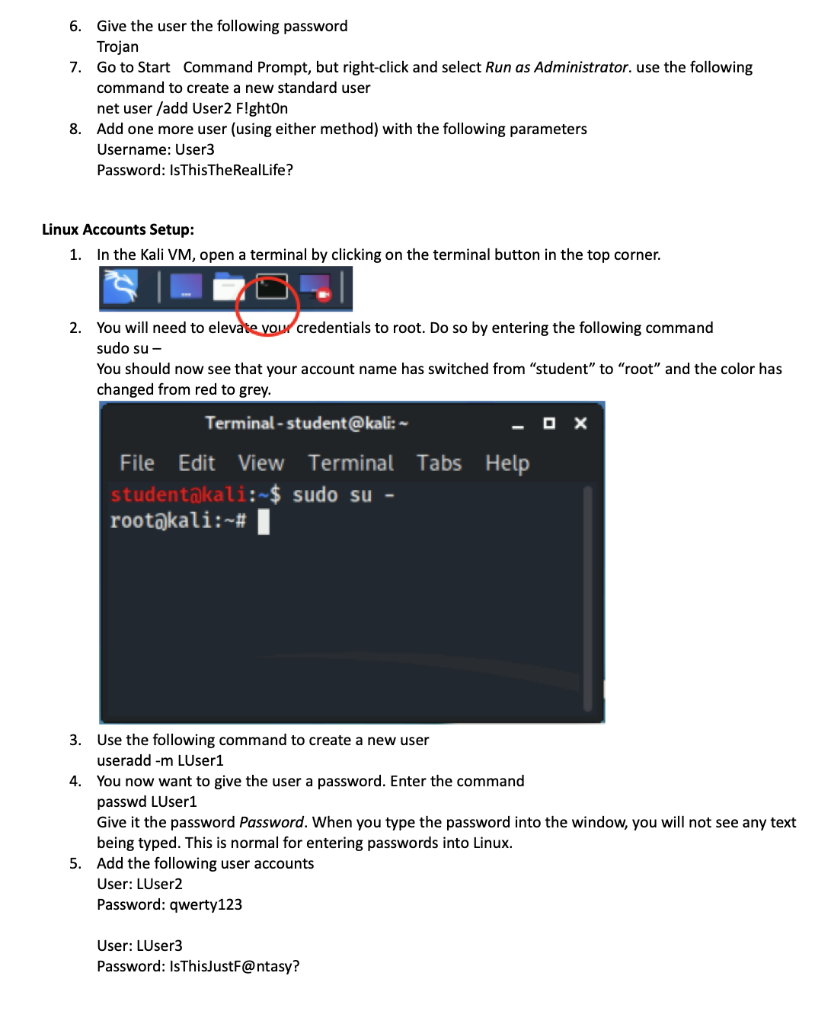
Overview: In this lab, students will get the basic understanding of password cracking in Windows. Students will practice creating accounts in both a Kali Linux and a Windows 7 virtual machine, with a varying degree of password length and complexity. Students will then use a variety of tools to crack the passwords. You will note in the case study that the business has had issues with usage of short passwords. With this lab you will be able to demonstrate exactly why this is a problem. There will be questions asked at the end of the lab. Be sure to submit all of your answers on the Lab 2 Worksheet link on Blackboard. Lab Setup: 1. Login to the US Cyber Range (console.uscyberrange.org). Select your course (ITP 125...) and select the Environment: Kali Linux and Vulnerable Windows 7(64 bits) VMs (2020.09). 2. Start both the Primary Machine (kali.example.com) and Other Machines (target.example.com). You will have two new browser tabs for each system. Windows Accounts Setup: 1. In the Windows VM, Go to Start Control Panel. Click on the link for Add or remove user accounts 2. Control Panel Control Panel Adjust your computer s settings System and Security Review your computer s status Back up your computer Find and fix problems Network and Internet View network status and tasks Choose homegroup and sharing options Hardware and Sound View devices and printers Add a device Programs Uninstall a program View by: Category Search Control Panel Accounts and Family sarey Add or remove user accounti Set up parental controls for any user Appearance and Personalization Change the theme Change desktop background Adjust screen resolution Clock, Language, and Region Change keyboards or other input methods Change display language Ease of Access Let Windows suggest settings Optimize visual display Ox P 3. Click on the link for Create a new account. 4. Call the account User1 and click on Standard user. 5. After the user account is created, click on the user account. Click on the Create a password link. 6. Give the user the following password Trojan 7. Go to Start Command Prompt, but right-click and select Run as Administrator. use the following command to create a new standard user net user /add User2 F!ghtOn 8. Add one more user (using either method) with the following parameters Username: User3 Password: Is This TheRealLife? Linux Accounts Setup: 1. In the Kali VM, open a terminal by clicking on the terminal button in the top corner. 2. You will need to elevate your credentials to root. Do so by entering the following command sudo su - You should now see that your account name has switched from student to root and the color has changed from red to grey. Terminal-student@kali: ~ File Edit student@kali:~$ root@kali:~# Terminal sudo su - Help 3. Use the following command to create a new user useradd -m LUser1 4. You now want to give the user a password. Enter the command passwd LUser1 User: LUser3 Password: IsThisJustF@ntasy? DX Give it the password Password. When you type the password into the window, you will not see any text being typed. This is normal for entering passwords into Linux. 5. Add the following user accounts User: LUser2 Password: qwerty123 Extracting the Windows Passwords 1. Within the Windows 7 VM, open up Chrome, and navigate to the following link: http://www.tarasco.org/security/pwdump 7/pwdump7.zip 2. The file should download, and when it is done, go to the File Explorer student Downloads. You should see the pwdump7 file. Right-click, and hit Extract All... Extract the package to the default location. 3. Copy-and-paste the extracted pwdump7 folder to the desktop. 4. Open an Administrator Command Prompt. Go to the newly created folder by typing cd C:\Users\student\Desktop\pwdump7\ 5. Execute the program by typing PwDump7.exe > winpass.txt 6. Open the newly created text file winpass.txt. Select all of the text and hit CTRL+C or Edit Copy. 7. Switch to your Kali VM. Click on the Kali Linux Dragon symbol in the top-left corner to bring up the menu. 8. Click on the Text Editor link on the right. 9. Hit CTRL+V or Edit Paste. You can see that there is a shared clipboard between each of the VMs and your own system. Save the file as winpass.txt in the student home directory. 10. You can see the Home directory from the desktop of the Kali Linux VM or by opening a terminal, which defaults to the home directory. Extracting the Linux Passwords 1. Open a new terminal window. We will be proceeding using the command-line for the entirety of this portion of the exercise. 2. Make sure you are in the home directory. You can always switch back to the home directory by typing cd~ and you can see which directory you are in by typing in pwd 3. Switch to the etc folder by typing cd \etc 4. View the contents of the password file by typing in cat passwd 5. Now view the contents of the shadow file by typing in cat shadow 6. Elevate to a root shell by typing in sudo su 7. Now navigate back to the etc folder, and see the contents of the shadow file. 8. Copy both the passwd and shadow files by using the following commands (one at a time) cp /etc/passwd /home/student/passwd cp /etc/shadow /home/student/shadow 9. Enter exit to leave the root shell and return to the student user account. Switch back to your home directory. Look at the contents of the home directory by typing in Is 10. Try to view the contents of both the passwd and the shadow file. You will still be blocked from viewing the shadow file. Type in the following command to unlock the shadow file sudo chmod 755 shadow 11. You should now be able to look at both the passwd and the shadow files 12. We need to combine the passwd and shadow files. Luckily, Kali has a built-in tool for password cracking called John the Ripper which in addition to password cracking has a tool for combining the files. While in your home directory, type the following command unshadow passwd shadow > linpass.txt 13. Look at the contents of the linpass.txt file. You should see both the user accounts, hashes and some other information from the passwd file. Cracking Passwords 1. You should be in the Kali VM for the entirety of this portion, with the extracted password hashes as winpass.txt and linpass.txt in the student home directory. 2. There is a wordlist that is included in Kali that will be useful for this exercise. Copy the wordlist to your home directory by entering the following command: cp /usr/share/wordlists/rockyou.txt.gz rockyou.txt.gz 3. Unzip the file by typing in gunzip rockyou.txt.gz 4. We will be using a tool called hashcat to try to crack the windows passwords. Type in the following command hashcat -h 5. Hashcat is a very powerful cracker that can do either dictionary or bruteforce using CPUs or GPUs. Enter the following command hashcat -m 1000 winpass.txt rockyou.txt --force Take note of the passwords cracked and the time taken 6. If you want to review the cracked passwords, they are stored in a file that can be viewed by entering the following command cat ~/.hashcat/hashcat.potfile 7. Now we ll try using John the Ripper on the linux passwords. We have already combined the passwd and shadow files. So enter the following command john --wordlist=rockyou.txt linpass.txt 8. It will take a while to finish, and you can always hit the enter key to see the status. After about 5 minutes, go ahead and hit q or CTRL+C. Take note of the passwords cracked and the time taken 9. Try using john the ripper against the windows passwords. You just have to change the password file at the end of the previous command. 10. Now we re going to use an online rainbow tables resource. Using your own computer, navigate to https://crackstation.net 11. On your Kali VM, open the winpass.txt file using the Text Editor. Copy each of the hashes from the file into the crackstation window, one hash on each separate line. 12. Do the reCAPTCHA and hit Crack Hashes Note which passwords were cracked.
Step by Step Solution
3.29 Rating (164 Votes )
There are 3 Steps involved in it
Step: 1
The skin friction coefficient Cf for a laminar boundary ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


