Binary bomb phase_2
I can't understand how to solve this problem.
I want to know the process and the answer.
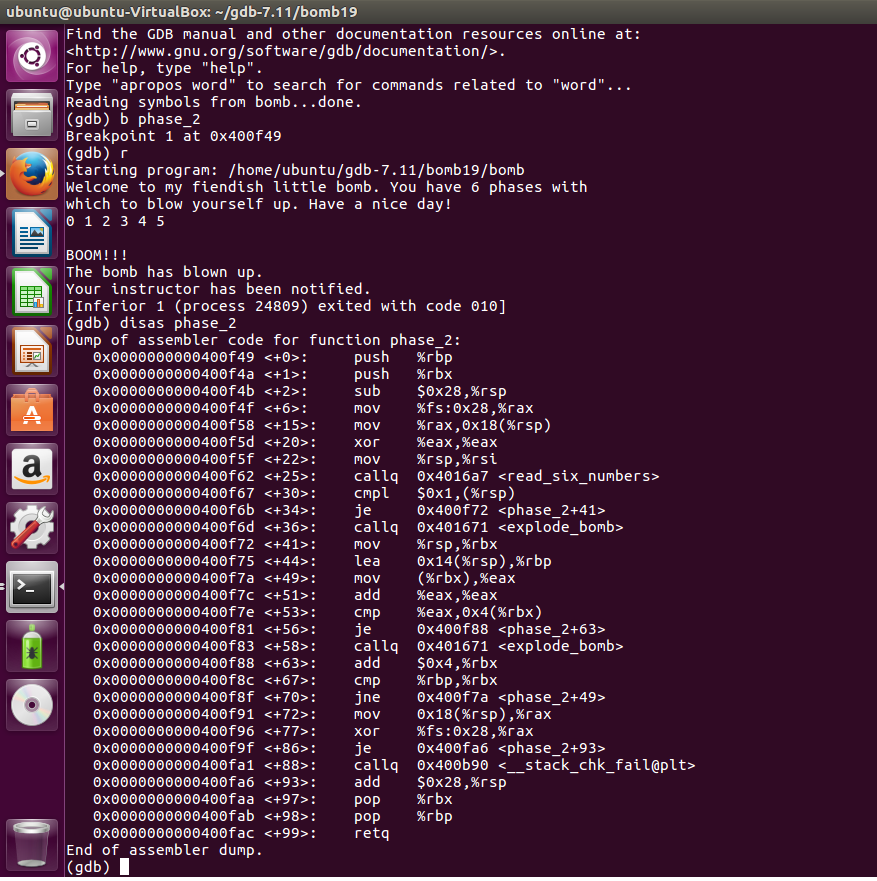
ubuntu@ubuntu-VirtualBox:~/gdb-7.11/bomb19 Find the GDB manual and other documentation resources online at:
. For help, type "help". Type "apropos word" to search for commands related to "word"... Reading symbols from bomb...done. (gdb) b phase_2 Breakpoint 1 at 0x400f49 (gdb) r Starting program: /home/ubuntu/gdb-7.11/bomb19/bonb Welcome to my fiendish little bomb. You have 6 phases with which to blow yourself up. Have a nice day! 12345 BOOM!!! The bonb has blown up. Your instructor has been notified [Inferior 1 (process 24809) exited with code 010] (gdb) disas phase_2 Dump of assembler code for function phase_2: 0x0000000000400f49 0x0000000000400f4a : 0x0000000000400f4b 6x0000000000400f4f : push push sub %rb %rbx $0x28,%rsp %fs :0x28,Krax 0x0000000000400f5d 0x0000000000400f5f : 6x0000000000400f6225: 0x000000000040of67 : cauq6x401671explode-bomb> 0x0000000000400f72 : 0x000000000040of75 : mov (%rbx),%eax 0x0000000000400f7c : 0x0000000000400f7e : cmp %eax,0x4(%rbx) 0x0000000000400f81 :je 0x0000000000400f83 : 0x0000000000400f88 : 0x0000000000400f8c : 0x0000000000400f8f: jne 6x400f7a
0x000000000040of91 : mov 0x18(%rsp),%ra>x 0x0000000000400f96 : 0x0000000000400f9f: je 6x0000000000400fa188: caug 6x400b98 stack chk fail@olt 0x0000000000400fa6 : 0x0000000000400faa : 0x0000000000400fab : %rsp,%rbx add %eax , %eax 0x400f88 callq 0x401671 add$0x4,%rbx xor %fs :0x28 , % rax add 0 0 retq 0x400fa6 $0x28,%rsp Xtbp End of assembler dump. ubuntu@ubuntu-VirtualBox:~/gdb-7.11/bomb19 Find the GDB manual and other documentation resources online at: . For help, type "help". Type "apropos word" to search for commands related to "word"... Reading symbols from bomb...done. (gdb) b phase_2 Breakpoint 1 at 0x400f49 (gdb) r Starting program: /home/ubuntu/gdb-7.11/bomb19/bonb Welcome to my fiendish little bomb. You have 6 phases with which to blow yourself up. Have a nice day! 12345 BOOM!!! The bonb has blown up. Your instructor has been notified [Inferior 1 (process 24809) exited with code 010] (gdb) disas phase_2 Dump of assembler code for function phase_2: 0x0000000000400f49 0x0000000000400f4a : 0x0000000000400f4b 6x0000000000400f4f : push push sub %rb %rbx $0x28,%rsp %fs :0x28,Krax 0x0000000000400f5d 0x0000000000400f5f : 6x0000000000400f6225: 0x000000000040of67 : cauq6x401671explode-bomb> 0x0000000000400f72 : 0x000000000040of75 : mov (%rbx),%eax 0x0000000000400f7c : 0x0000000000400f7e : cmp %eax,0x4(%rbx) 0x0000000000400f81 :je 0x0000000000400f83 : 0x0000000000400f88 : 0x0000000000400f8c : 0x0000000000400f8f: jne 6x400f7a 0x000000000040of91 : mov 0x18(%rsp),%ra>x 0x0000000000400f96 : 0x0000000000400f9f: je 6x0000000000400fa188: caug 6x400b98 stack chk fail@olt 0x0000000000400fa6 : 0x0000000000400faa : 0x0000000000400fab : %rsp,%rbx add %eax , %eax 0x400f88 callq 0x401671 add$0x4,%rbx xor %fs :0x28 , % rax add 0 0 retq 0x400fa6 $0x28,%rsp Xtbp End of assembler dump







