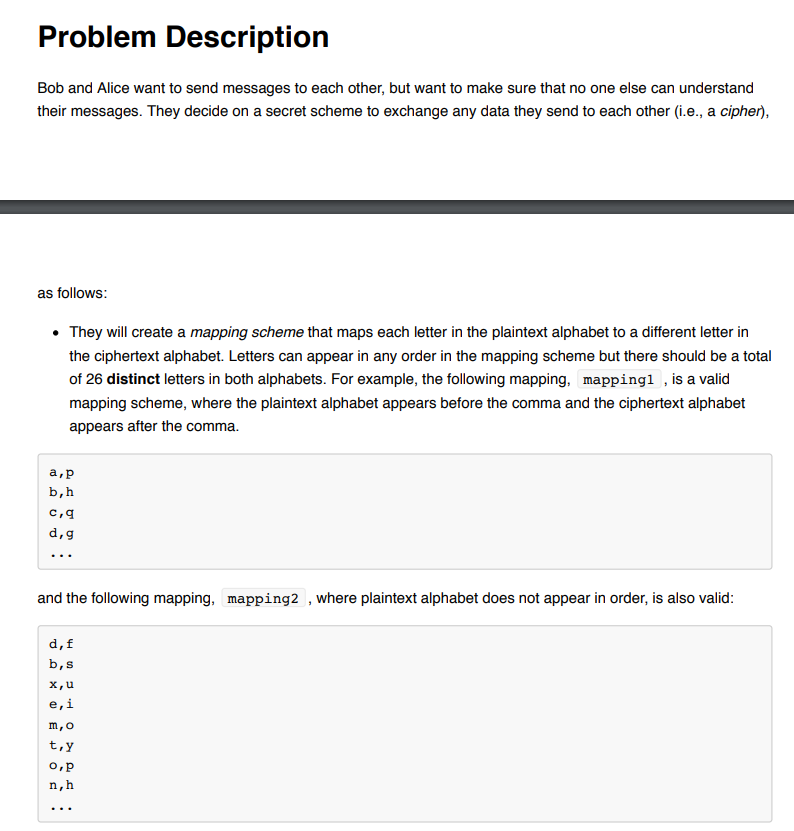
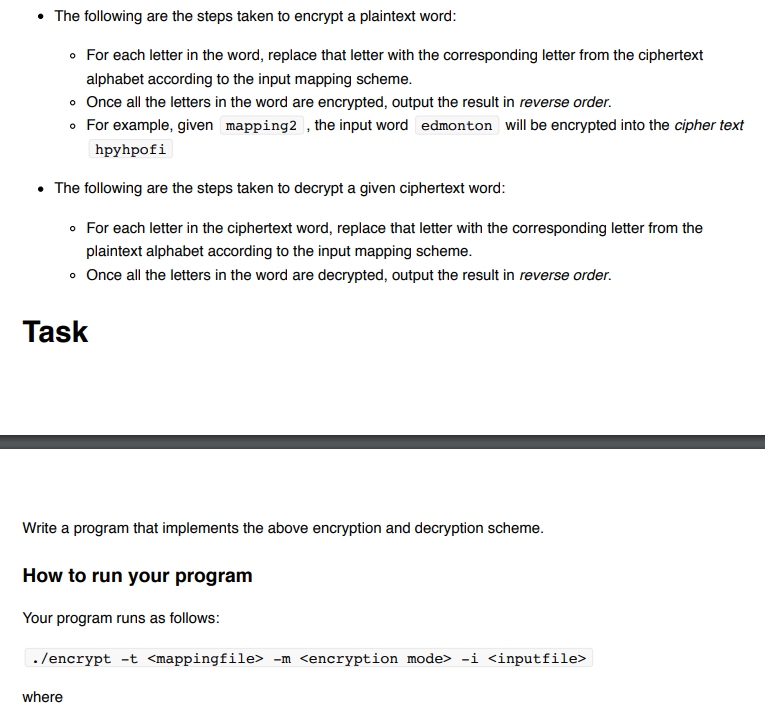



Bob and Alice want to send messages to each other, but want to make sure that no one else can understand their messages. They decide on a secret scheme to exchange any data they send to each other (i.e., a cipher. as follows: They will create a mapping scheme that maps each letter in the plaintext alphabet to a different letter in the ciphertext alphabet. Letters can appear in any order in the mapping scheme but there should be a total of 26 distinct letters in both alphabets. For example, the following mapping, mappingl , is a valid mapping scheme, where the plaintext alphabet appears before the comma and the ciphertext alphabet appears after the comma. b,h C,q d,g and the following mapping, mapping2 , where plaintext alphabet does not appear in order, is also valid: d,f b,s x, u e,i 3 t,y o,p n,h where mappingfile is a comma separated file (csv) as shown above and is preceded by the flag-t encryption mode determines if the program should encrypt or decrypt the input provided by the user. The mode is 1 for encryption and2 for decryption. The mode is preceded by the flag -m inputfile is a text input file that contains the list of words that are going to be encrypted or decrypted. Each word appears on a separate line. The file is preceded by the flag -i All the above arguments are required for the program to run and must be preceded by their respective flags. Note that the order of the program arguments should not matter. For example, the following are all equivalent ways to run the program and will yield the same behavior: ./encrypt -t mappingfile.csv -m 1 -i words.txt ./encrypt -m 2 -i words.txt-t mappingfile.csv /encrypt -m 1 -i words_to_encrypt.txt -t mappingfile.csv Error Checking Your program must report and print an error to stderr and quit in the following cases. Note the return code that needs to be returned in each case. The return code is the integer that your program returns upon exit (e.g return 0 in main or exit(2) anywhere in the program). The error message must be the exact error message provided (the quotations just show you the boundary of the message and the angle brackets just indicate placeholders and must be replaced by the exact argument. Both the quotations and the angle brackets should not be included in the message): If the input file mappingfile is not found o Error Message: "Error: Mapping file
does not exist" o Return code: 3 If the format of the input file mappingfile is incorrect. You need to check that (1) the mapping file has exactly 26 lines, (2) each line has the format , (characters other than lower case letters should not be accepted), (3) there are no repeated letters in Please do not include any extra messages or debugging information. Any extra output will make your output different from the expected output, and will cause you to fail the test cases. Program Format . Your program consists of a single C file called encrypt.c . Your program must contain at least the main function and two functions encrypt and decrypt with the following declarations: void encrypt (char plainTextl, int inputLength); void decrypt (char cipherText[], int inputLength); where encrypt takes the character array that stores the input plaintext provided by the user in encryption mode (e.g., edmonton) and the length of this plainText array. It then prints the encryption result to the screen. o and decrypt takes the character array that stores the cipher text provided by the user in and the length of this cipherText array. It then prints the decryption mode (e.g., ifohyph decryption results to the screen. o You need to correctly declare functions encrypt and decrypt at the top of your file. You are welcome (and encouraged) to have more functions to have a cleaner and more modular program, but the above two functions will count towards your grade. To get started early, you can just create the main function that contains all your code. When we cover functions, you can then create the two above functions, and take out the necessary parts of the code you wrote to put into these functions. Do not wait till we cover functions to start this assignment. It is unlikely that you will finish it on time While we will not grade you for header files for this assignment, you are welcome (and encouraged) to create a header file for your program. Please check the general assignment information on eClass for code style, comments, etc. Assumptions The following are assumptions you can safely make. You cannot assume anything that is not explicitly stated here. When in doubt, ask on the forum. The input files we will use to test your program will follow the correct format indicated above Our test input files will have words that contain only lower-case English letters. Each word will be on a separate line in the input file, and the maximum length of any word is 20 letters. We will only test with input that can be encrypted/decrypted using the input mapping file. . You cannot make any assumptions about the input mapping file. You must ensure that it is in the correct format described above . You cannot make any assumptions about the program arguments. You must ensure you handle all cases described in the "How to run your program" section above. When testing your program arguments, we will make sure the expected output of the test case is not ambiguous and corresponds to one output code Submission . You must create a Makefile to compile your program. Your Makefile must also contain the clean target. Your program must compile into an executable called encrypt without any warnings or errors. If your TA cannot run ./encrypt after running make, you will get a 0 for the assignment. . You will create 1 encryption and 1 decryption test case as follows. o The encryption test case will have the following files 1. mapping_encryption.csv test case which is the mapping file that will be used for your encryption 2. input_encryption.txt which contains a single line with the input word to encrypt 3. output_encryption.txt of the input word which contains a single line with the expected encryption output 4. test_encryption.sh (with the correct program arguments) to run your program with the above mapping and input files. Running/test_encryption.sh must produce the expected output, which is the same as that provided in the output_encryption.txt file. which is an executable bash script that contains the right command o The decryption test case will have the following files 1. mapping_decryption.csv test case which is the mapping file that will be used for your decryption 2. input_decryption.txt which contains a single line with the ciphertext that need to be decrypted output_decryption.txt which contains a single line with the expected decryption output of the input ciphertext 3. 4. test_decryption.sh which is an executable bash script that contains the right command (with the correct program arguments) to run your program with the above mapping and input files. Running/test_decryption.sh must produce the expected output, which is the same as that provided in the outut_decryption.txt file o Sample test files have been provided in your GitHub repo. *Note that you must adhere these exact file names as your TA will use automated scripts to mark your test case. Note that you cannot submit the provided samples for your test cases. We will use the diff command to ensure that your provided files are different











