Question
capstone Project 7-1: secure switch Ports in Packet tracer: 1. Add a new PC to your network, as shown in Figure 7-46. Create the needed
capstone Project 7-1: secure switch Ports in Packet tracer:
1. Add a new PC to your network, as shown in Figure 7-46. Create the needed connection with a Copper Straight-Through cable, connecting PC2 to Switch1s FastEthernet0/20 interface. The link between the switch and the PC should come up automatically.
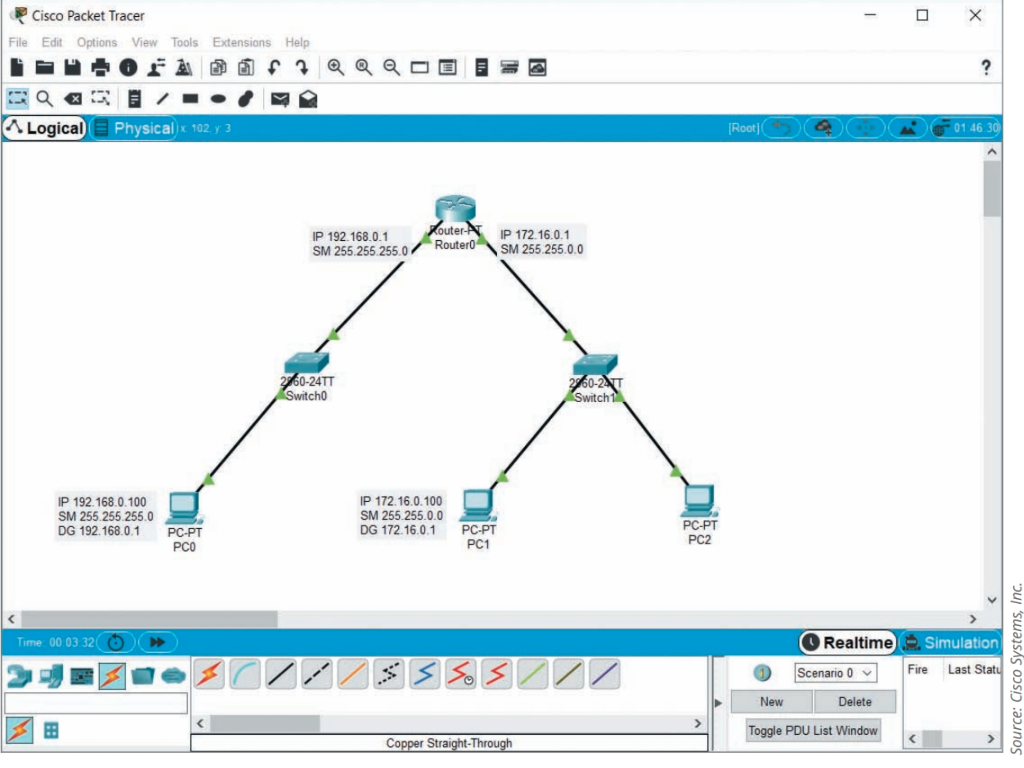
2. Configure the PC with the following static IP addresses:
a. IPv4 address: 172.16.0.110
b. Subnet mask: 255.255.0.0
c. Default gateway: 172.16.0.1
3. You can use the switch port command to explore the options available for port security on the switchs port that faces PC2. On the switchs CLI tab, click in the IOS Command Line Interface box, press enter and then enter the commands from Table 7-2. In Step 4, there are questions for you to answer as you work through the commands in Table 7-2, so be sure to look ahead at those questions as you work through the commands in the table.
table 7-2 Explore port security options on a switch
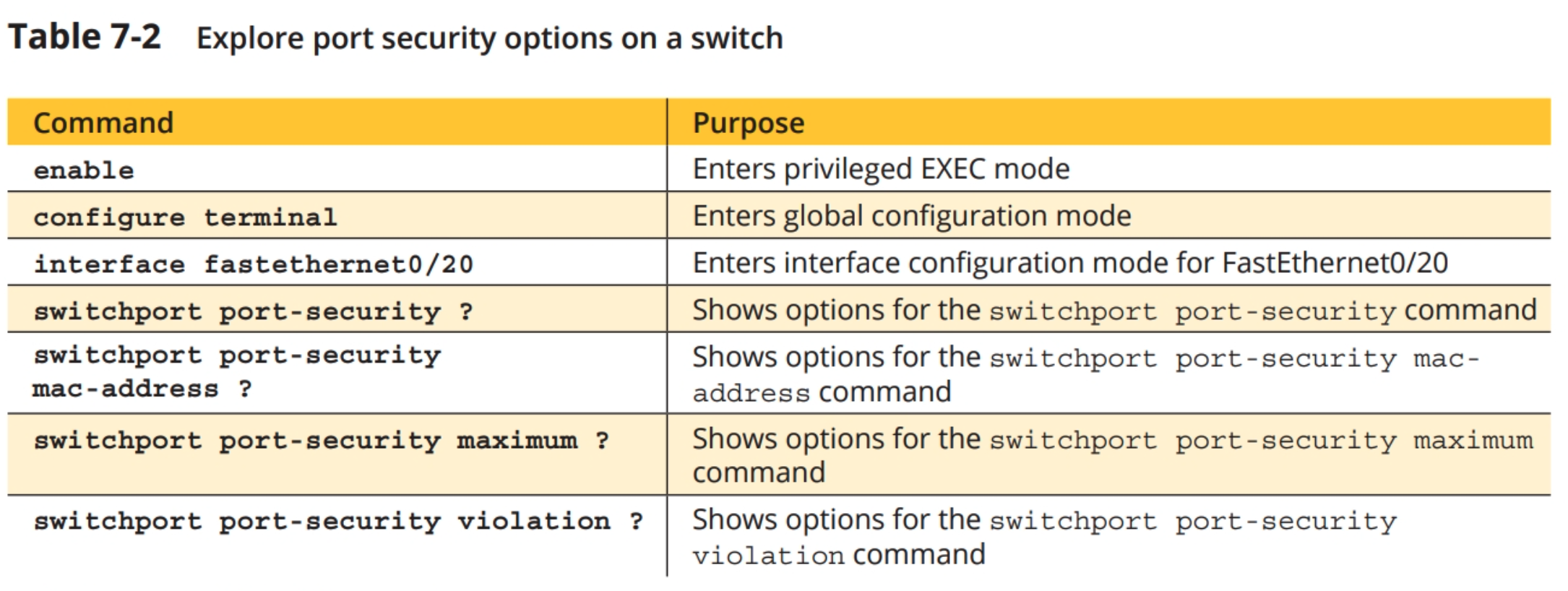
4. Answer the following questions:
a. What are the four options listed for the switchport port-security command?
b. What are the two configuration options for the switchport port-security mac-address command?
c. How many MAC addresses can be allowed using the switchport port-security maximum command?
d. What are the three configuration options for the switchport port-security violation command?
5. Now youre ready to configure port security on the switchs port that faces PC2. But first, you must configure the port for access mode. This indicates to the switch the port will be connected to an endpoint rather than to another switch. On the switchs CLI tab, enter the commands from Table 7-3.
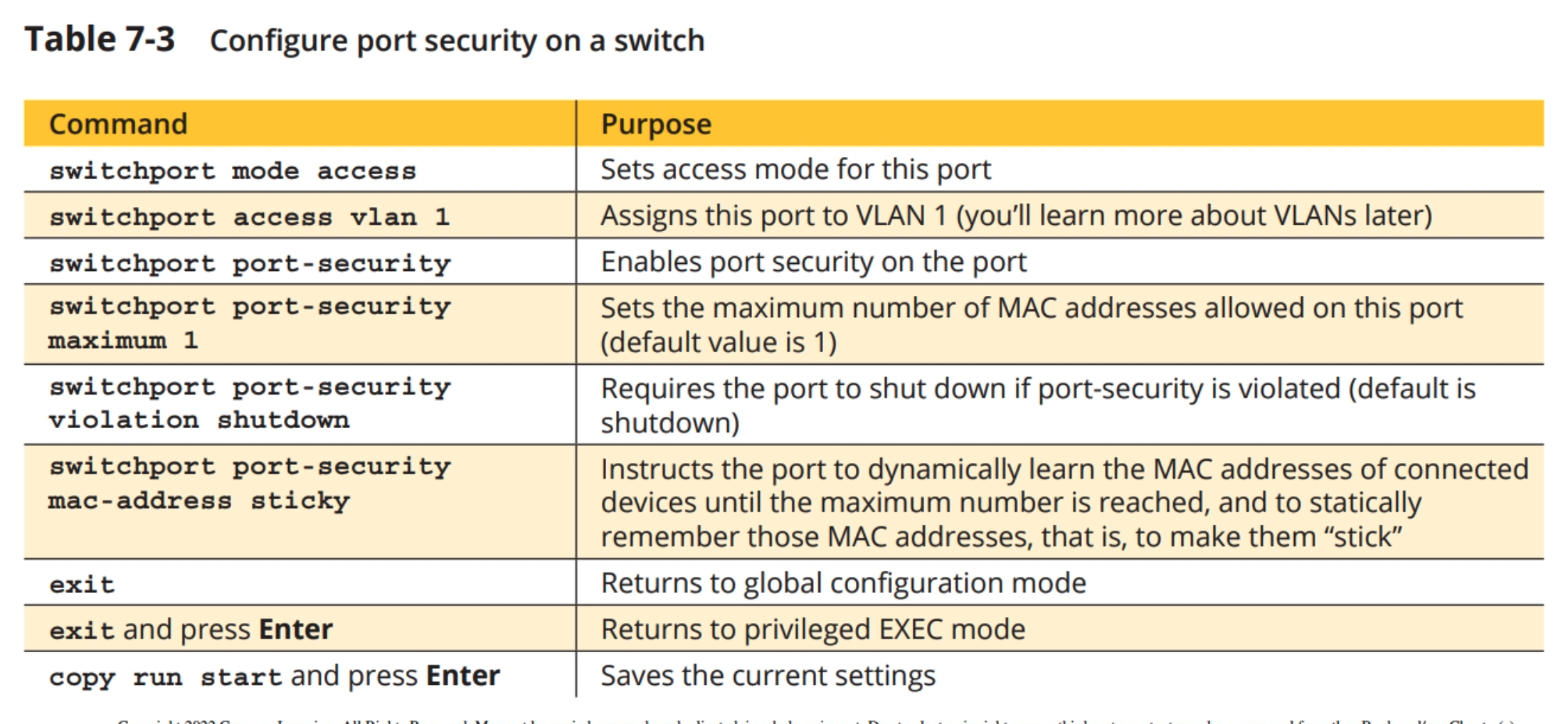
6. Now that youve secured the port and instructed the switch to automatically learn and remember the MAC address of the connected computer, youre ready to check the MAC address table. Enter the command show mac-address-table. What MAC address information is listed?
7. The switch has not yet seen any packets from PC2 to learn its MAC address. So you need to send some packets across the interface from which the switch can collect MAC address information. From PC2, ping PC1. What command did you use?
8. On Switch1, rerun the show mac-address-table command and answer the following questions:
a. Now what information is listed?
b. What is the type of each entry?
c. Why do you think this is?
Pretend a hacker gains physical access to the Ethernet cable connected to PC2. They remove the cable from PC2 and connect it to their own laptop. What will happen when they try to access the network? To find out, do the following:
a. Delete the cable connecting PC2 to the switch as follows: Click anywhere in the workspace to deselect any objects, click the delete (del) button in the Common tools bar, click the cable leading to PC2, and then press esc to exit Delete mode. What information is reported on the switchs CLI tab?
b. Add a laptop to the workspace. Set its static IP address information to the following:
IPv4 address: 172.16.0.110
Subnet mask: 255.255.0.0
Default gateway: 172.16.0.1
c. Add a Copper Straight-Through connection from the laptop to the switchs FastEthernet0/20 port. Wait for the link to come up. What information is reported on the switchs CLI tab now?
10. The connection is successfully established, but can the hacker do anything on the network? After both ends of the new connection turn to green triangles, go to the laptops Command Prompt interface. Position the laptops configuration window off to the side of the workspace so you can see the network and enter commands at the same time. Ping PC1, watch the effect, and then answer the following questions: a. What happened when you attempted the ping? b. What information is reported on the switchs CLI tab? c. What do you think administratively down means?
11. The switch has automatically shut down the port in response to the security violation. Take a screenshot of your network showing the administratively down link; submit this visual with your answers to this projects questions.
12. Now try to reconnect the legitimate computer. Delete the laptop and its connection to the switch and add a new connection between PC2 and the switchs FastEthernet0/20 port. What happens?
13. Try to ping PC1 from PC2. What happens?
14. To reenable the connection from PC2, go to the switchs CLI tab. Position the switchs configuration window off to the side of the workspace so you can see the network and enter commands at the same time. Press enter to return to the command prompt and then enter the commands from Table 7-4. What happens to the connection?
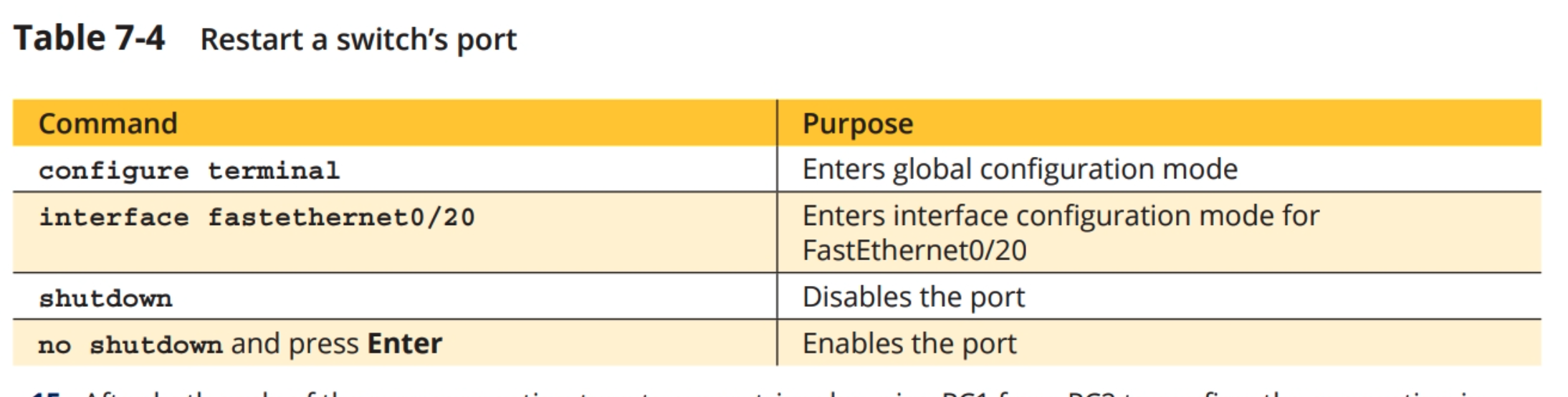
15. After both ends of the new connection turn to green triangles, ping PC1 from PC2 to confirm the connection is restored. Save your project in a safe place for future projects.
16. Make some notes on your Wikidot website about your activities in Packet Tracer for this project.
Provide screen shots for all the steps and answer questions please and thank you.
Cisco Packet Tracer Table 7-2 Explore port security options on a switch Table 7-3 Configure port security on a switch Table 7-4 Restart a switch's portStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


