Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Closed Hash Table Assume that in the input file a3.txt, there are no more than 50 state names. Each entry is less than or equal
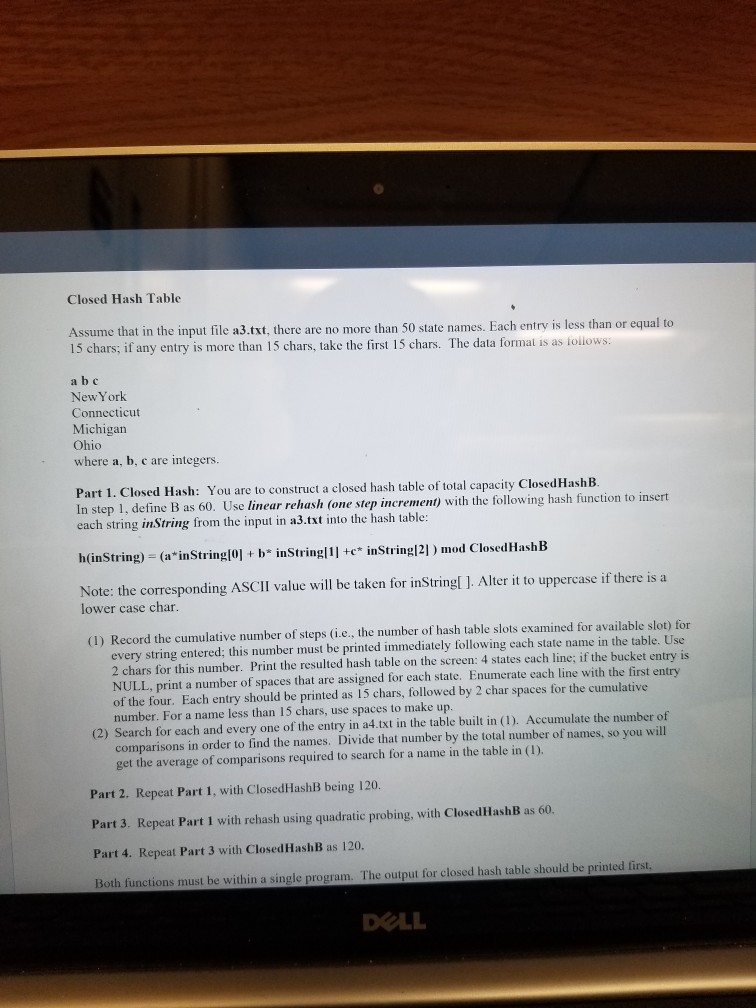
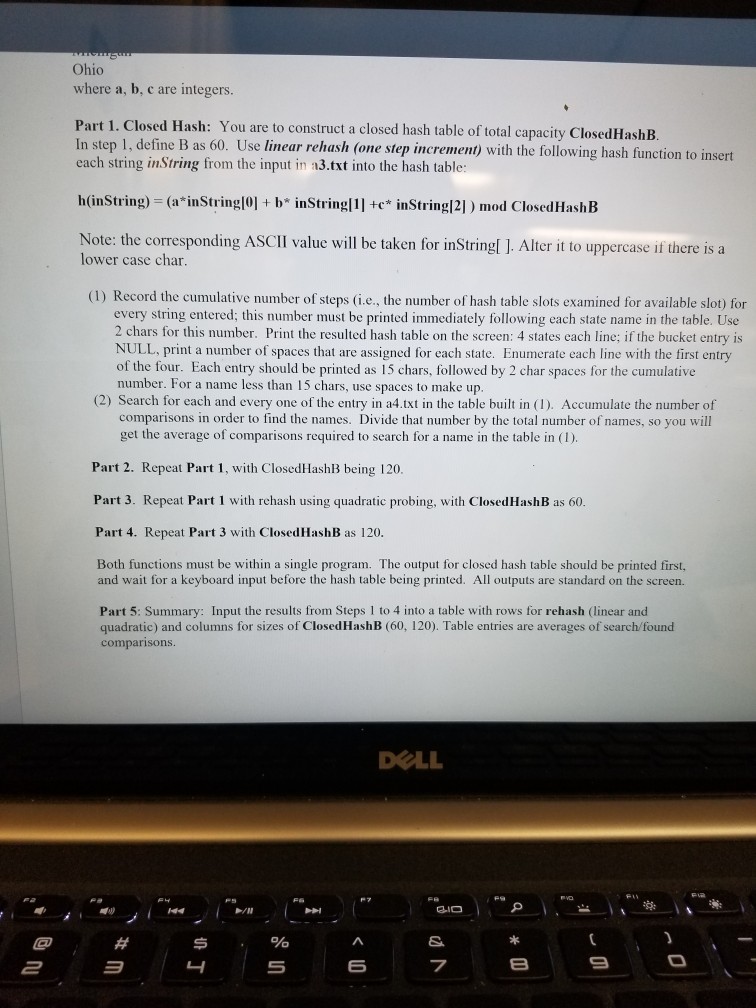
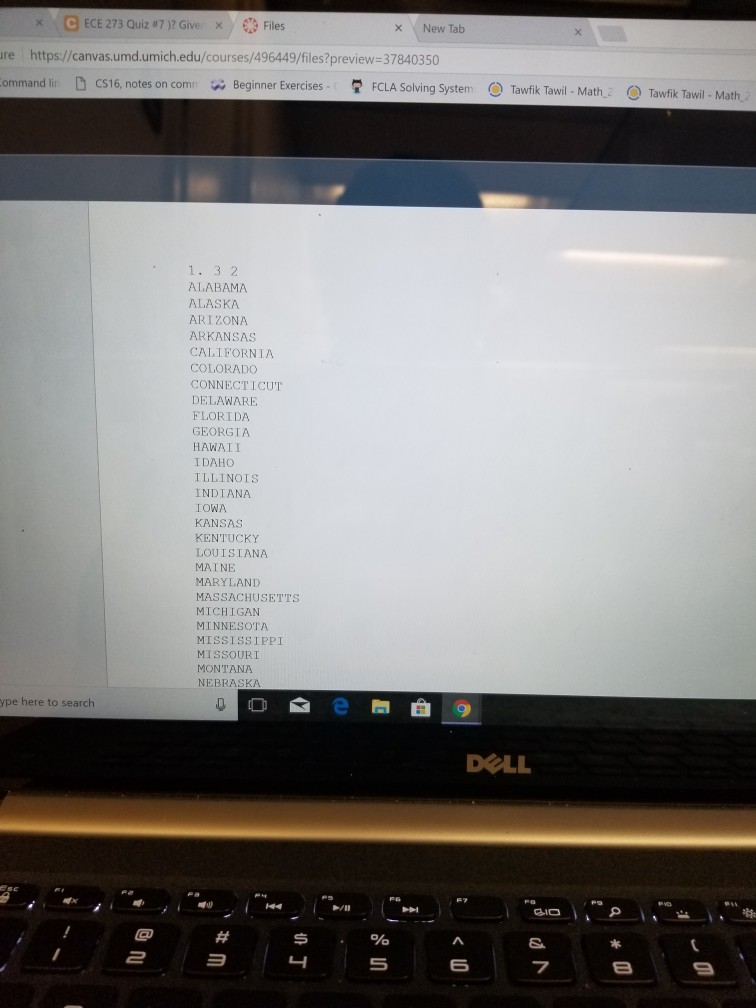
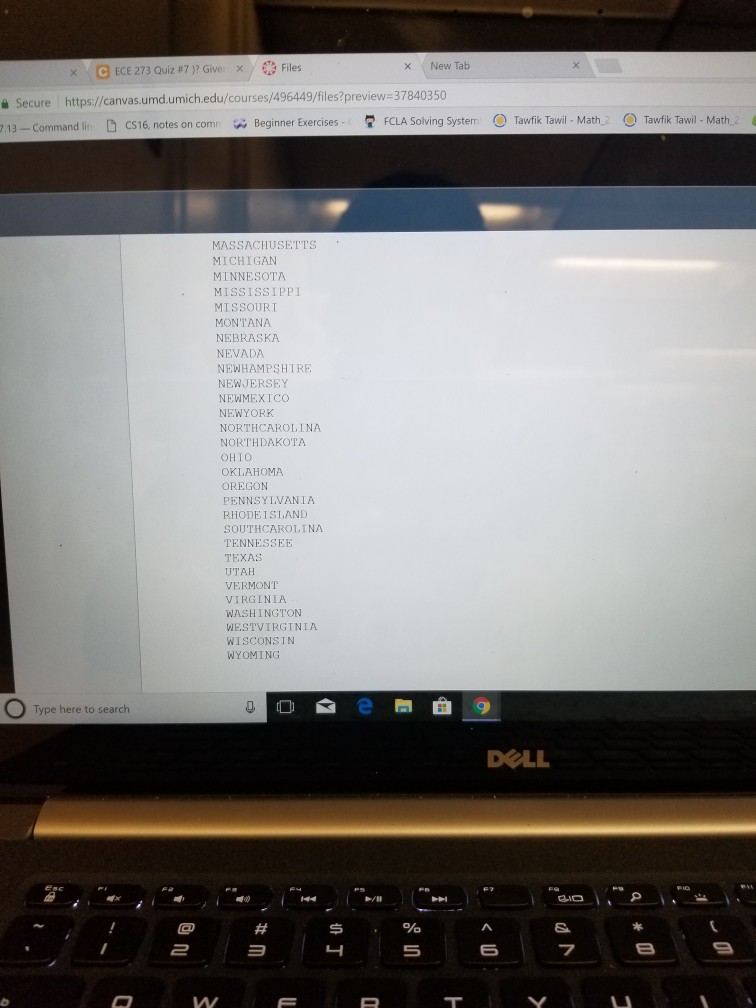
Closed Hash Table Assume that in the input file a3.txt, there are no more than 50 state names. Each entry is less than or equal to 15 chars; if any entry is more than 15 chars, take the first 15 chars. The data formal is as ioiiows a b c NewYork Connecticut Michigan Ohio where a, b, c are integers. Part 1. Closed In step 1, def each string inString from the input in a3.txt into the hash table: Hash: You are to construct a closed hash table of total capacity Closed HashB fine B as 60. Use linear rehash (one step increment) with the following hash function to insert h(inString) - (a"inStringlo]+ b inStringlle inStringl21) mod ClosedHashB Note: the corresponding ASCII value will be taken for inString[ ]. Alter it to uppercase if there is a lower case char. (1) Record the cumulative number of steps (i.e., the number of hash table slots examined for available slot) for every string entered; this number must be printed immediately following each state name in the table. Use 2 chars for this number. Print the resulted hash table on the screen: 4 states each line; if the bucket entry is NULL, print a number of spaces that are assigned for each state. Enumerate each line with the first e of the four. Each entry should be printed as 15 chars, followed by 2 char spaces for the cumulative number. For a name less than 15 chars, use spaces to make up. ntry (2) Search for each and every one of the entry in a4.txt in the table built in (1). Accumulate the number of comparisons in order to find the names. Divide that number by the total number of names, so you will get the average of comparisons required to search for a name in the table in (1). Part 2. Repeat Part 1, with ClosedHashB being 120 Part 3. Repeat Part 1 with rehash using quadratic probing, with ClosedHashB as 60. Part 4. Repeat Part 3 with ClosedHashB as 120. Both functions must be within a single program. The output for closed hash table should be printed first, DOLL Closed Hash Table Assume that in the input file a3.txt, there are no more than 50 state names. Each entry is less than or equal to 15 chars; if any entry is more than 15 chars, take the first 15 chars. The data formal is as ioiiows a b c NewYork Connecticut Michigan Ohio where a, b, c are integers. Part 1. Closed In step 1, def each string inString from the input in a3.txt into the hash table: Hash: You are to construct a closed hash table of total capacity Closed HashB fine B as 60. Use linear rehash (one step increment) with the following hash function to insert h(inString) - (a"inStringlo]+ b inStringlle inStringl21) mod ClosedHashB Note: the corresponding ASCII value will be taken for inString[ ]. Alter it to uppercase if there is a lower case char. (1) Record the cumulative number of steps (i.e., the number of hash table slots examined for available slot) for every string entered; this number must be printed immediately following each state name in the table. Use 2 chars for this number. Print the resulted hash table on the screen: 4 states each line; if the bucket entry is NULL, print a number of spaces that are assigned for each state. Enumerate each line with the first e of the four. Each entry should be printed as 15 chars, followed by 2 char spaces for the cumulative number. For a name less than 15 chars, use spaces to make up. ntry (2) Search for each and every one of the entry in a4.txt in the table built in (1). Accumulate the number of comparisons in order to find the names. Divide that number by the total number of names, so you will get the average of comparisons required to search for a name in the table in (1). Part 2. Repeat Part 1, with ClosedHashB being 120 Part 3. Repeat Part 1 with rehash using quadratic probing, with ClosedHashB as 60. Part 4. Repeat Part 3 with ClosedHashB as 120. Both functions must be within a single program. The output for closed hash table should be printed first, DOLL
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


