Question
Compiler Construction (a) Give two legitimizations for why a compiler is routinely isolated into passes (or stages) and show a normal game plan of passes
Compiler Construction
(a) Give two legitimizations for why a compiler is routinely isolated into passes (or
stages) and show a normal game plan of passes and the data structures passed
between them. [4 marks]
(b) nd run inside various projects, could differentiate from that of
gathering an application and running it on different events on a single machine.
[2 marks]
(c) Explain the difference between a scholarly party code and a
aining a thing module. Exhibit the basic plan object
report, for example ELF, highlighting the inspiration driving each portion. Give assemblylevel or C-level code that produces sections in eachse regions. [7 marks]
(d) Explain the exercises of a linker, the occupation of libraries and what makes certain
object records directly executable. [4 marks]
(e) Explain the differentiation among static and dynamic associating giving one advantage
of each. Which is for the most part reasonable for an applet set aside on a site to be
stacked into a program? [3 marks]
3.2. 05pts. Exit with return code 2 right away in the event that how much debates passed is zero.
3.3. 05pts. Make an unfilled record samplefile on the off chance that it doesn't exist in current working vault.
3.4. 05pts. Store the endlessly out way to deal with samplefile in a variable _SFILE utilizing $1 and the filename.
3.5. 05pts. Use limit expansion to dispense with the filename samplefile from _SFILE . Hint :
Forgo all characters as longest matching model from the beginning of the all around way.
3.6. 05pts. Use limit extension to segregate how information in _SFILE by clearing out the filename
from the end.
3.7. 05pts. Print 3.5 and 3.6 in a solitary resounding announcement and exit with 0.
3.8. 05pts. Print the things in your substance with line numbers.
Standard itemsets found through Apriori have different applications in information mining tries. Assignments, for example, seeing enchanting models concerning the information base, figuring out game-plan and Mining of collusion rules is the most gigantic of them.
Affiliation rules apply to grocery store exchange information, or on the other hand if nothing else, to separate the client direct concerning the bought things. Partnership rules portray how intermittently the things are bought
(a) Name three kinds of programming weakness; give an illustration of each and a brief
depiction of how each could be taken advantage of.
(b) Alice needs to go after Bob's PC by means of the Internet, by sending IP bundles
to it, straightforwardly from her own PC. She doesn't maintain that Bob should find out the
IP address of her PC.
(I) Is this more straightforward to accomplish for Alice with TCP-or UDP-based application
conventions? Make sense of why. [3 marks]
(ii) For the more troublesome convention, make sense of one strategy that Alice could
attempt to defeat this hindrance and one countermeasure that Bob would be able
execute in his PC. [3 marks]
(iii) Name three capacities that Alice's Internet specialist co-op could
execute to make it more hard for Alice to accomplish her objective?
[3 marks]
(c) In what way are TCP/UDP port numbers under 1024 extraordinary?
(a) Distributed capacity approaches can be isolated into network joined capacity
(NAS) and capacity region organizations (SANs). Make sense of with the guide of a chart
the fundamental distinctions between the two methodologies. [4 marks]
(b) The organization document framework (NFS) is much of the time utilized in neighborhood.
(I) Why is NFS not ordinarily viewed as appropriate for wide region organizations
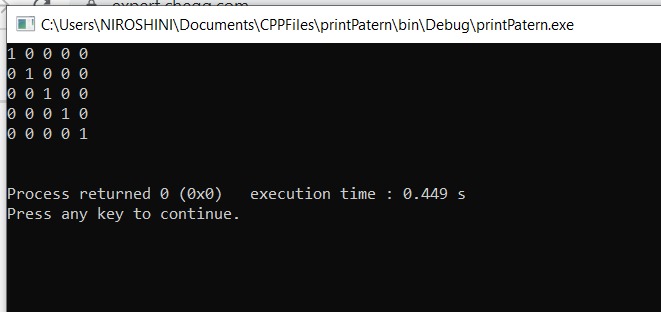
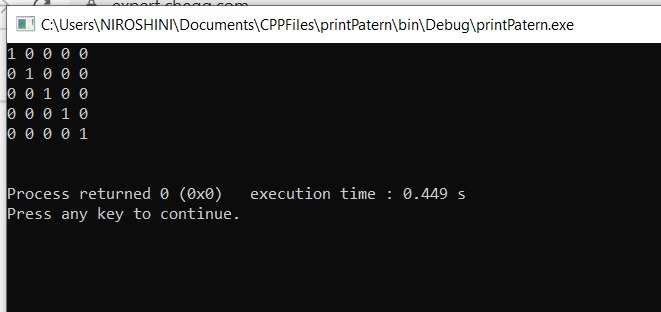
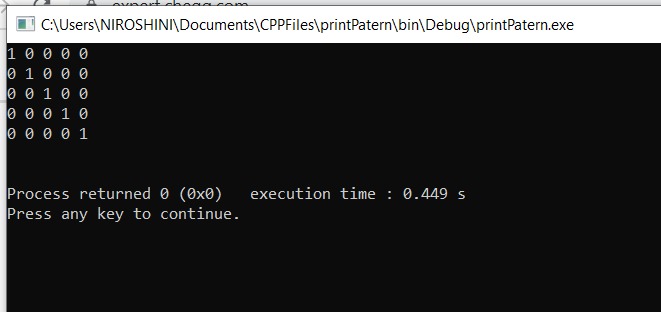
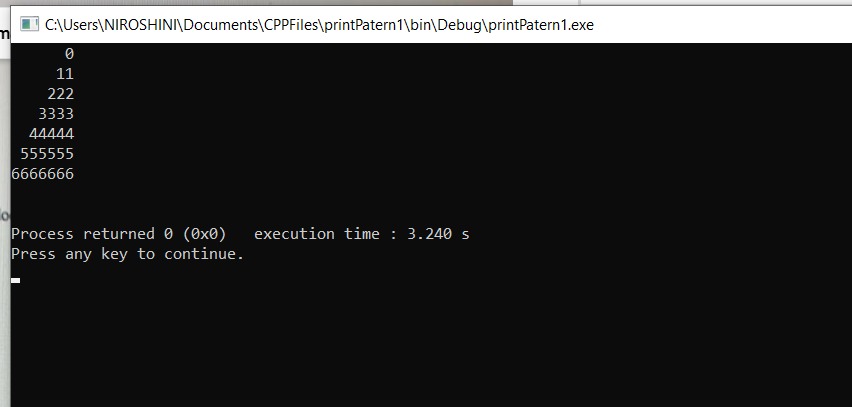
C:\Users\NIROSHINI\Documents\CPPFiles\print Patern\bin\Debug\printPatern.exe 1 0 0 0 0 0 1 0 0 0 0 0 1 0 0 0 0 0 1 0 0 0 0 0 1 Process returned 0 (0x0) execution time: 0.449 s Press any key to continue.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


