Question
COMPLETE THE FOLLWING PROGRAM IN C USING THE TEMPLATES BELOW: hash.h: #ifndef __HASH_H #define __HASH_H typedef struct HTNodeTag { char* key; char* value; struct HTNodeTag
COMPLETE THE FOLLWING PROGRAM IN C USING THE TEMPLATES BELOW:
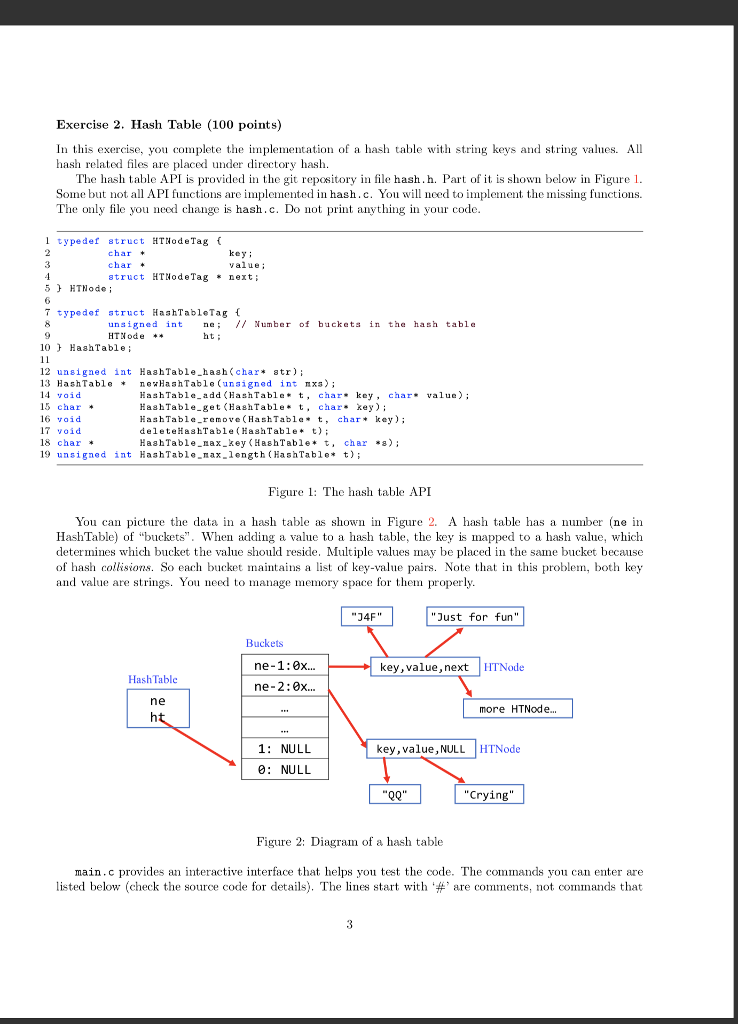


hash.h:
#ifndef __HASH_H
#define __HASH_H
typedef struct HTNodeTag {
char* key;
char* value;
struct HTNodeTag * next;
} HTNode;
typedef struct HashTableTag {
unsigned int ne;
HTNode ** ht;
} HashTable;
unsigned int HashTable_hash(char* str);
HashTable * newHashTable(unsigned int mxs);
void HashTable_add(HashTable* t, char* key, char* value);
char * HashTable_get(HashTable* t, char* key);
void HashTable_remove(HashTable* t, char* key);
void deleteHashTable(HashTable* t);
unsigned int HashTable_max_length(HashTable* t);
char * HashTable_max_key(HashTable* t, char *s);
#endif
hash.c:
#define _POSIX_C_SOURCE 200809L
#include
#include
#include
#include
#include
#include "hash.h"
#define HT_HASH_PRIME 41U
int power(int base, unsigned int exp){
int i, result = 1;
for(i =0; i result *= base; return result; } /* The function maps a string to an unsigned int */ unsigned int HashTable_hash(char* str) { if (str == NULL) return 0; } HashTable* newHashTable(unsigned int mxs) { /* Implement a constructor that builds a hashtable relying on auxiliary chaining (lists) and capable to hold up to mxs lists in its primary structure. Write a hash function that is suitable for strings. */ //TODO } * return NULL if the key is not on the list */ static HTNode* findInList(HTNode * head, char * key) { // TODO return NULL; } /* Add the pair key/value to the hash table t. * Do nothing is the key is already in the hash table. * */ void HashTable_add(HashTable* t, char* key, char* value) { if (t == NULL) return; } char* HashTable_get(HashTable* t, char* key) { /* Returns the value associated to key in t. If there is no such value (key does not appear in t) simply return NULL */ // TODO return NULL; } void HashTable_remove(HashTable* t, char* key) { /* Removes the pair identified by key from the hashtable t */ // TODO } void deleteHashTable(HashTable* t) { /* Deallocate all the memory needed for t and its auxiliary structures */ } /* Find the length of the longest list * Return 0 if the hash table is empty. * */ unsigned int HashTable_max_length(HashTable* t) { // TODO return 0; } /* If s is NULL, return a pointer to the largest key in the hash table. * * If s not NULL, return the largest of the keys that are smaller than s. * * Do not clone the key. * * Return NULL if no key is found. * * Note that an empty string is the smallest. So pass NULL to * find the max. */ char * HashTable_max_key(HashTable* t, char *s) { // TODO if (t == NULL) return NULL; return NULL; }
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


