Computer security
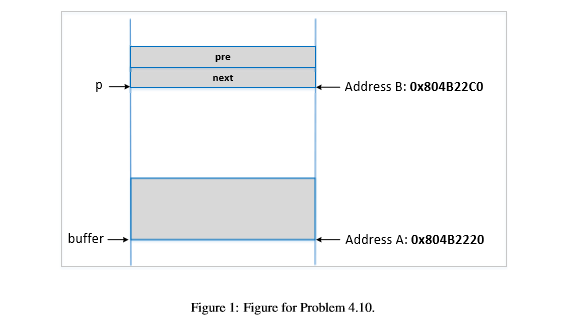
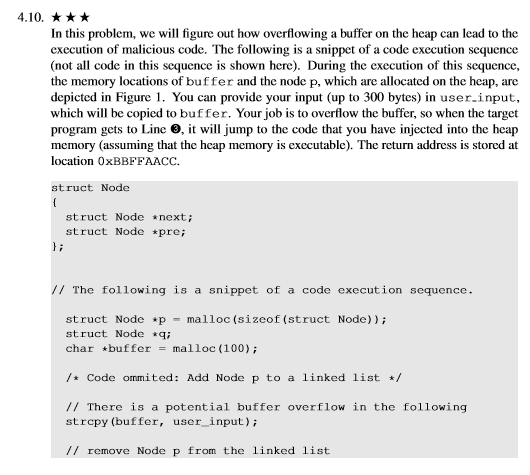

pre next Address B: 0x804B22C0 buffer Address A: 0x804B2220 Figure 1: Figure for Problem 4.10 4.10. In this problem, we will figure out how overflowing a buffer on the heap can lead to the execution of malicious code. The following is a snippet of a code execution sequence (not all code in this sequence is shown here. During the execution of this sequence, the memory locations of buffer and the node p, which are allocated on the heap, are depicted in Figure 1. You can provide your input (up to 300 bytes) in user.input, which will be copied to buffer. Your job is to overflow the buffer, so when the target program gets to Line 9, it will jump to the code that you have injected into the heap memory (assuming that the heap memory is executable). The return address is stored at location 0xBBFFAACC struct Node struct Node next; struct Node *pre; /1 The following is a snippet of a code execution sequence. struct Node p -malloc(sizeof (struct Node)) struct Node qi char .buffer malloc (100) / Code ommited: Add Node p to a linked list / // There is a potential buffer overflow in the following strepy (buffer, user_input) // remove Node p from the linked list ppre; q->nextp-nexti return; Hint: You still want to place the starting address of your malicious code into the return address field located at 0xBBFFAACC. Unlike stack-back buffer overflows, where you can naturally reach the return address field via overflowing, now the buffer is on the heap but the return address is on the stack; you cannot reach the stack by overflowing something on the heap. You should take advantage of the operations on the linked list (Lines and ) to modify the return address field. This is a simplified version of how a buffer overflow on the heap can be exploited. The linked list is not part of the vulnerable program; it is actually part of the operating system which uses it to manage the memory on the heap for the current process. Unfortunately, the linked list is also stored on the heap, so by overflowing an application's buffer, attackers can change the valucs on this linked list. When the OS operates on the corrupted linked list, it may change the return address of function, and trigger the execution of the injected 4.11. This problem is built on top of Problem 4.10 Assume that the structure for Node becomes the following (a new integer field is addeded to the beginning Please redo Problem 4.10.. It should be noted that in Figure 1, the variable p will now point to the area 4 bytes below the next field. struct Node int value; struct Node next; struct Node pre; pre next Address B: 0x804B22C0 buffer Address A: 0x804B2220 Figure 1: Figure for Problem 4.10 4.10. In this problem, we will figure out how overflowing a buffer on the heap can lead to the execution of malicious code. The following is a snippet of a code execution sequence (not all code in this sequence is shown here. During the execution of this sequence, the memory locations of buffer and the node p, which are allocated on the heap, are depicted in Figure 1. You can provide your input (up to 300 bytes) in user.input, which will be copied to buffer. Your job is to overflow the buffer, so when the target program gets to Line 9, it will jump to the code that you have injected into the heap memory (assuming that the heap memory is executable). The return address is stored at location 0xBBFFAACC struct Node struct Node next; struct Node *pre; /1 The following is a snippet of a code execution sequence. struct Node p -malloc(sizeof (struct Node)) struct Node qi char .buffer malloc (100) / Code ommited: Add Node p to a linked list / // There is a potential buffer overflow in the following strepy (buffer, user_input) // remove Node p from the linked list ppre; q->nextp-nexti return; Hint: You still want to place the starting address of your malicious code into the return address field located at 0xBBFFAACC. Unlike stack-back buffer overflows, where you can naturally reach the return address field via overflowing, now the buffer is on the heap but the return address is on the stack; you cannot reach the stack by overflowing something on the heap. You should take advantage of the operations on the linked list (Lines and ) to modify the return address field. This is a simplified version of how a buffer overflow on the heap can be exploited. The linked list is not part of the vulnerable program; it is actually part of the operating system which uses it to manage the memory on the heap for the current process. Unfortunately, the linked list is also stored on the heap, so by overflowing an application's buffer, attackers can change the valucs on this linked list. When the OS operates on the corrupted linked list, it may change the return address of function, and trigger the execution of the injected 4.11. This problem is built on top of Problem 4.10 Assume that the structure for Node becomes the following (a new integer field is addeded to the beginning Please redo Problem 4.10.. It should be noted that in Figure 1, the variable p will now point to the area 4 bytes below the next field. struct Node int value; struct Node next; struct Node pre









