Question
Consider the following mutual authentication and key establishment protocol, which uses a timestamp T and public key cryptography. For each of the following cases, explain
Consider the following mutual authentication and key establishment protocol, which uses a timestamp T and public key cryptography.
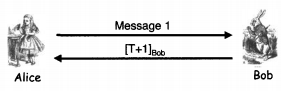
For each of the following cases, explain whether or not the resulting protocol provides an effective means for secure mutual authentication and a secure session key K. Ignore replay attacks based solely on the clock skew.
A.) Message 1: {[T,K]Alice}Bob
B.) Message 1: {"Alice", [T,K]Alice}Bob
C.) Message 1: "Alice", {[T,K]Alice}Bob
D.) Message 1: T, "Alice", {[K]Alice}Bob
E.) Message 1: "Alice", {[T]Alice}Bob and let K = h(T)
Message1 Bob AliceStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


