Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Create and compile a list of 10 features necessary for an effective Active Directory Baseline Design. Create a spreadsheet that shows each of the GPO
Create and compile a list of 10 features necessary for an effective Active Directory Baseline Design. Create a spreadsheet that shows each of the GPO settings for your Baseline Design/
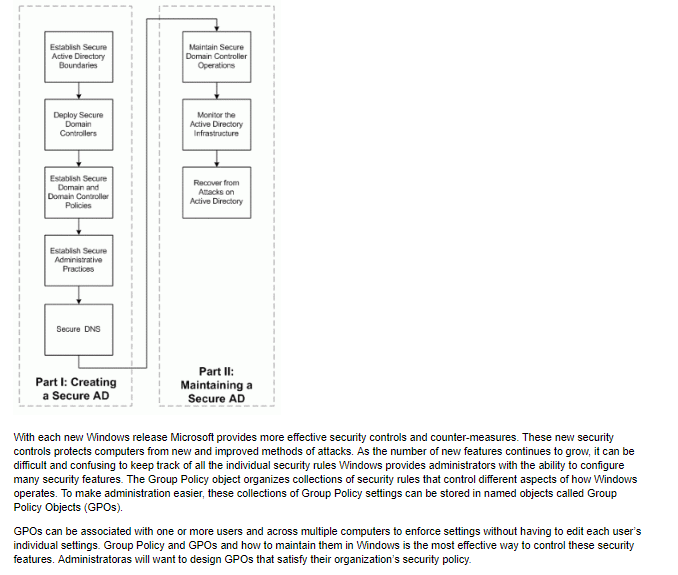
Estabish Secure Active Directory Maintain Secure Domain Controlier Deploy Secure Domain Monitor the Active Directory Doman and Domain Condroller Recover from Amacks on Active Direciory Estabish Secure Administrathve Secure DNS Part I: Creating a Secure AD Part I Maintaining a Secure AD With each new Windows release Microsoft provides more effective security controls and counter-measures. These new security controls protects computers from new and improved methods of attacks. As the number of new features continues to grow, it can be difficult and confusing to keep track of all the individual security rules Windows provides administrators with the ability to configure many security features. The Group Policy object organizes collections of security rules that control different aspects of how Windows operates. To make administration easier, these collections of Group Policy settings can be stored in named objects called Group Policy Objects (GPOs). GPOs can be associated with one or more users and across multiple computers to enforce settings without having to edit each user's individual settings. Group Policy and GPOs and how to maintain them in Windows is the most effective way to control these security features. Administratoras will want to design GPOs that satisfy their organization's security policy. Estabish Secure Active Directory Maintain Secure Domain Controlier Deploy Secure Domain Monitor the Active Directory Doman and Domain Condroller Recover from Amacks on Active Direciory Estabish Secure Administrathve Secure DNS Part I: Creating a Secure AD Part I Maintaining a Secure AD With each new Windows release Microsoft provides more effective security controls and counter-measures. These new security controls protects computers from new and improved methods of attacks. As the number of new features continues to grow, it can be difficult and confusing to keep track of all the individual security rules Windows provides administrators with the ability to configure many security features. The Group Policy object organizes collections of security rules that control different aspects of how Windows operates. To make administration easier, these collections of Group Policy settings can be stored in named objects called Group Policy Objects (GPOs). GPOs can be associated with one or more users and across multiple computers to enforce settings without having to edit each user's individual settings. Group Policy and GPOs and how to maintain them in Windows is the most effective way to control these security features. Administratoras will want to design GPOs that satisfy their organization's security policyStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


