Answered step by step
Verified Expert Solution
Question
1 Approved Answer
du.au/d2l/le/content/1357494/viewContent/6499127/View CS Maps Finding Casual Wor... java InsideSherpa - Virtu... 10 Common Misco... covid module OnTrack A Knight's Tour Large Knight's Tours O X
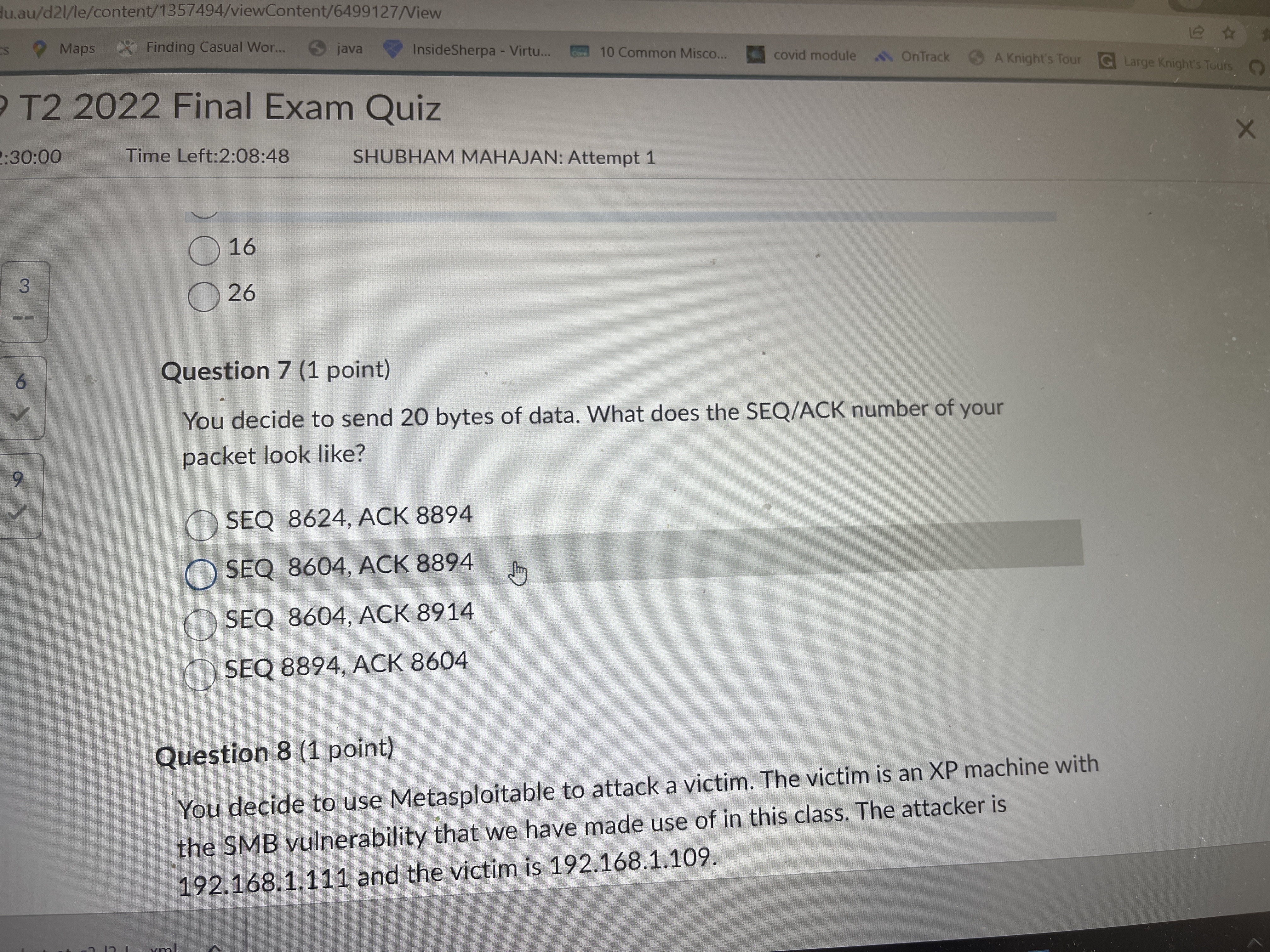
du.au/d2l/le/content/1357494/viewContent/6499127/View CS Maps Finding Casual Wor... java InsideSherpa - Virtu... 10 Common Misco... covid module OnTrack A Knight's Tour Large Knight's Tours O X 9 T2 2022 Final Exam Quiz 2:30:00 9 3 H Time Left:2:08:48 16 26 SHUBHAM MAHAJAN: Attempt 1 Question 7 (1 point) You decide to send 20 bytes of data. What does the SEQ/ACK number of your packet look like? SEQ 8624, ACK 8894 OSEQ 8604, ACK 8894 SEQ 8604, ACK 8914 SEQ 8894, ACK 8604 Question 8 (1 point) You decide to use Metasploitable to attack a victim. The victim is an XP machine with the SMB vulnerability that we have made use of in this class. The attacker is 192.168.1.111 and the victim is 192.168.1.109. r r
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


