Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Explain the following security principles. For each, give one example of how they are used in real - life. Do NOT re - use the
Explain the following security principles. For each, give one example of how they are used in reallife. Do NOT reuse the examples in lecture PPT
a Least privilege.
b Privilege separation.s
c Failsafe default.
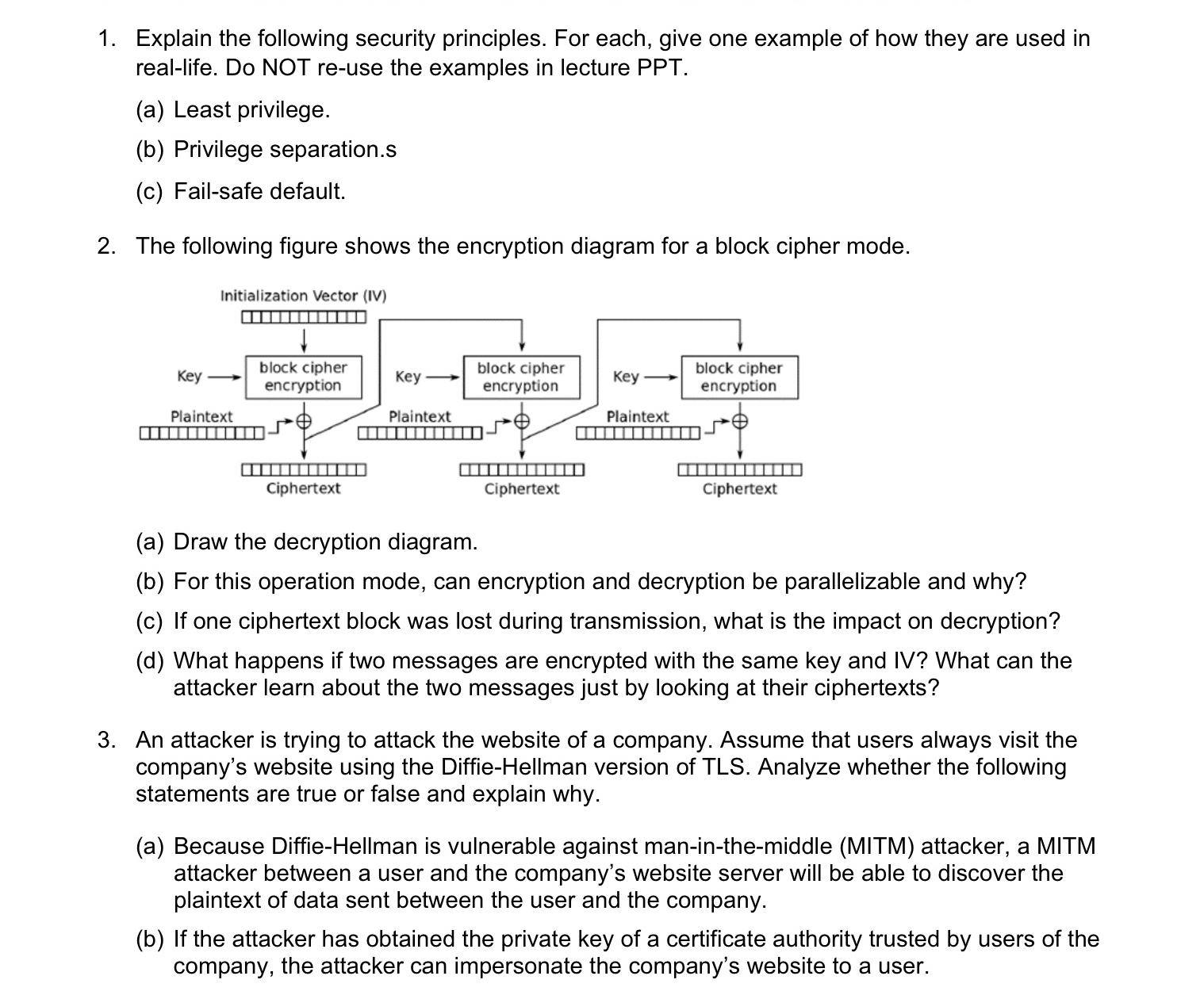
The following figure shows the encryption diagram for a block cipher mode.
a Draw the decryption diagram.
b For this operation mode, can encryption and decryption be parallelizable and why?
c If one ciphertext block was lost during transmission, what is the impact on decryption?
d What happens if two messages are encrypted with the same key and IV What can the attacker learn about the two messages just by looking at their ciphertexts?
An attacker is trying to attack the website of a company. Assume that users always visit the company's website using the DiffieHellman version of TLS Analyze whether the following statements are true or false and explain why.
a Because DiffieHellman is vulnerable against maninthemiddle MITM attacker, a MITM attacker between a user and the company's website server will be able to discover the plaintext of data sent between the user and the company.
b If the attacker has obtained the private key of a certificate authority trusted by users of the company, the attacker can impersonate the company's website to a user.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


