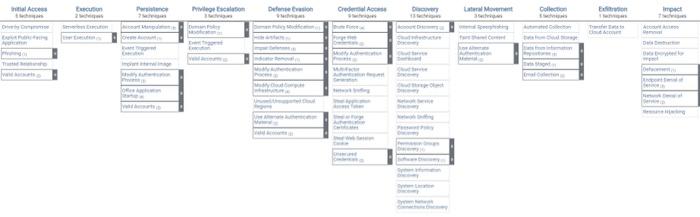
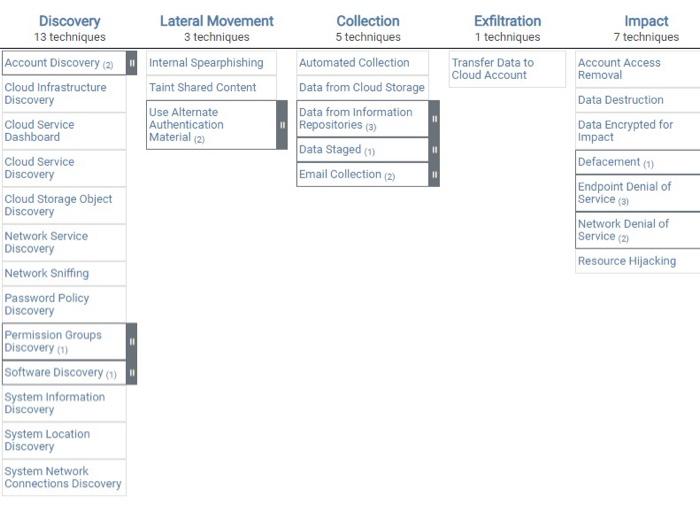
Question: Hello! Working on some Python coding and just wanted to know how I would go about getting the output in the second pic? In my
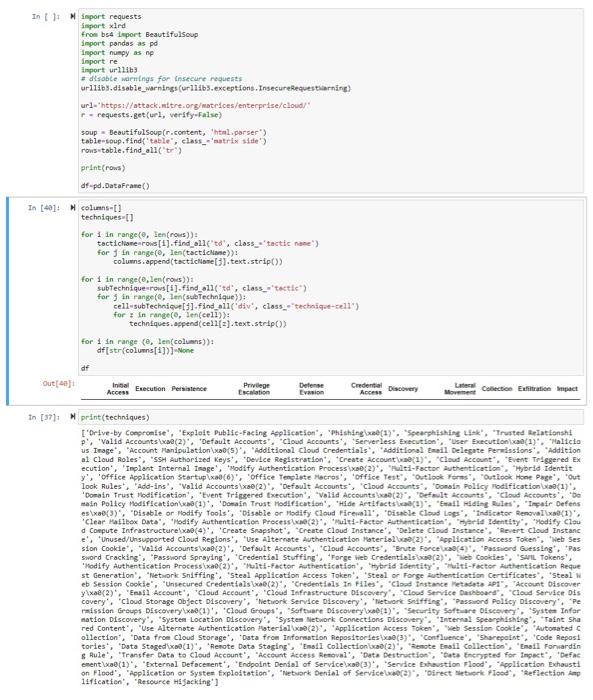
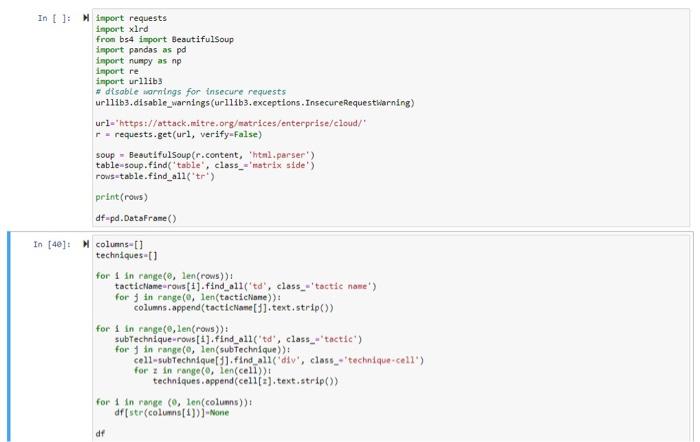

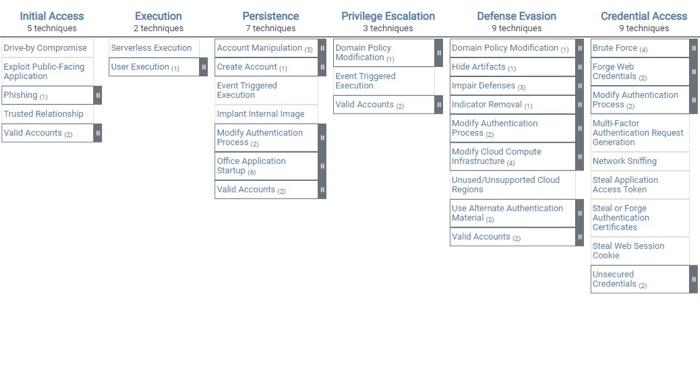
Di M print(techniques) us Inage", "Account Manipulation kxa0(5) ", "Additional Cloud Credentials", "Additional Emadl Delegrte Fermissions", "Addition al Cloud Roles", "SSH Authorized Keys', "Devlce Regfstration", "Create Account luaer1)". "Cleud Account", "Event. Triggered Ex ecution", "Inplant Internal Inage', 'Modify Authenticstion Processixae(2)", "Multi-Factor Authentication", "Ilybrid . Identit. look Rules", "Add-ins", "Volid Accountslxoe(2)", "Defsult Accounts", "Cloud Accounts", "Donsin Folify Modificationlxiag(1)", "Doeain Trust Hodification", "Event Triggered trecuthon", "Valid Accounts base(2)" " "Ceefault Accounts", "Cloud Accetunts", "Do main Policy Medificatianikag(1)', 'Domain Trust Modification", "Hide Artifactslucadi]". "Emall Midthe Rules"; "Imour Defens es'xaer3)", "Disable or Modify Tools", "Disable or Modify Cloud Firewal11", "Disable clsud Logs", "Tindicator kenovallaadi\}", e', "Unused/Unsupported Cloud Reglons", "Use Alternate Authentication Material bead(2)", "Applicathon Access Token", "Web Ses sion Cookle', "Walid Accountslowae(2)', "Default Accounts", "Cloud Accounts", "Brute Forcelura9(4)", "Passiond Gutssing', 'Pas sword Cracking", "Password Spraying", "Credentisl stuffing", "Forge web Credentislsiase(2)", "Meb Cookies", "SwIL. Tokens", "Modify Authentication Processixab(2)", "/ulti-factor Aatheoticatfon", "Hydrid Identity", "ihulti-factor Authentication Aeque st Generation', "Wetiork Sniffing', 'Steal Applicstion Access Token', "Steal. or Forge Authentication Certificates", 'Steal W eb Session Cookie", "Unsecured Credentfalsloae(2)", "CredentHols In Files", "Cloud instance Metadata apt". "Account Discover ylxae(2)", "Enafl Acceunt", 'Cloud Account", "Cleud Infrastructure DYscevery". "Cleud Service Paskbeard". "Cleud Service DIs covery', "Cloud Storage Object Discovery', "Network Service Discovery", "hetuork Sndtfing", "Passiond Policy Discovery", "Pe mation. Discovery", "System Location Discovery", "System Metwork Connections Discovery". "Internal Spearphishing", "Taint Sha red Content." "Use Alternate Authentication Asteriallucag(2)", "Application Access" Token", "Web Session Cookle", "Automated C ollection", "Dats from Cloud Storage", "Data from Inforeatlon hepositorfespeae(3)", "Confluence", "Sharepalst", "Code Reposi tories", "Data Stagedluxa(1)", "Renote Data Staging", "Endi Collectionlacad(2)", "Aenote Enail Collection", "Enail Fonvardin g. Rule", "Transfer Data to Cloud Account", "Accourt Access Renoval", 'Data Destruction", "bat. Encrypted for Impect", "Defac ement'lxad(1)", "External Defocenent', 'Endpodint Dendal of Servicelxad(3)", "Sendice Exhaudtion Flood", "Application Exhausti 1ificatien", "Aescurce Hijacking'] ['Drive-by Compromise', 'Exploit Public-Facing Application', 'Phishing'wa0(1)", 'Spearphishing Link', 'Trusted Relationshi p', 'Valid Accountslxae(2)', 'Default Accounts', 'Cloud Accounts', 'Serverless Execution', 'User Executionlxae(1)', 'Malicio us Image', "Account Manipulationlxa0(5)', 'Additional Cloud Credentials', 'Additional Enail Delegate Pernissions", "Addition al Cloud Roles", 'SSH Authorized Keys', "Device Registration', 'Create Accountlxae(1)', 'Cloud Account', 'Event Trggered Ex ecution", "Implant Internal Image', "Modify Authentication Processlxae(2)", "Multi-Factor Authentication', "Hybrid Identit y, 'Office Application Startuplxa@(6)', 'Office Tenplate Macros', 'office Test', 'Outlook Forns', 'Outlook Home Page', 'Out 'Domain Trust Hodiflcation', 'Event Triggered Executlon', 'Valid Accounts lxao(2)', 'Default Accounts', 'Cloud Accounts', 'Do main Policy Modificatianlxae(1)", "Domain Trust Modification', 'Hide Artifactslxae(1)', 'Emafl Hiding Rules", "Impair Defens eslxae(3)' "Disable or Modify Tools", "Disable or Modify Cloud Firewall', 'Oisable Cloud Logs", 'Indicator Renovallxa0(1)', 'Clear Mailbox Data', "Modify Authentication Processlxae(2)', "Multi-Factor Authentication", 'Hybrid Identity', "Modify Clou d Compute Infrastructurelxae(4)", "Create Snapshot', 'Create Cloud Instance', "Delete Cloud Instance', 'Revert Cloud Instanc e, 'Unused/Unsupported Cloud Regions', "Use Alternate Authenticatian Materiallxa0(2)', 'Application Access Token', 'Web Ses sion Cookie", "Valid Accountsixae(2)", "Default Accounts", 'Cloud Accounts", "Brute Forcelxao(4)', 'Passward Guessing', 'Pas sword Cracking", 'Password Spraying", 'Credential Stuffing', "Forge lieb Credentials bxae(2)", 'Heb Cookies', 'SAll Tokens", 'Modify Authentication Processlxao(2)', "MultI-Factor Authentlcatlon', 'Hybrid Identity', "Multl-Factor Authentication Aeque st Generation', 'Network Snifflng', 'Steal Application Access Token', 'steal or Forge Authentication Certificates', 'Steal W eb Session Cookle', 'Unsecured Credentlalslxa0(2)', 'Credentials In Files", 'Cloud Instance Metadota API', "Account Discover covery', 'Clowd Storage object Discovery', 'Network Service Discovery', "Network Sniffing', 'Password Policy Discovery', 'Pe relssion Groups Discoverylxa0(1)', "Cloud Groups", 'Softuare Discoverylxae(1)", 'Security Softuare Discovery', "Systei Infor mation Discovery', "System Location Discovery', "System Network Connectlons Olscovery", 'Internal Spearphishing", "Taint Sho red Content", "Use Alternate Authentication Materialleae(2)', 'Application Access Token', "Web Session Cookie', "Automated C ollection', 'Data from Cloud Storage", "Data from Informstion Repositoriesluad(3)", "Confluence', "Sharepoint', 'Code Reposi. tories", 'Data Stagedlxag(1)', "Remote Data Staging', 'Enall Collectlonixae(2)", "Remote Email Collectlon', 'Emall Forvardin g Rule', 'Transfer Data to Cloud Account", 'Account Access Renoval', "Data Destruction", "Data Enerypted for Inpact", 'Defac ementlxae(1)', "External Defacenent", 'Endpoint Denial of Servicelxae(3)", 'Service Exhaustion Flood', 'Application Exhausti on Flood', 'Application or Systen Exploitation', 'Network Denial of Servicelxae(2)', 'Direct Network, Flood', 'Reflection Anp Iification", 'Resource Hijacking'] Di M print(techniques) us Inage", "Account Manipulation kxa0(5) ", "Additional Cloud Credentials", "Additional Emadl Delegrte Fermissions", "Addition al Cloud Roles", "SSH Authorized Keys', "Devlce Regfstration", "Create Account luaer1)". "Cleud Account", "Event. Triggered Ex ecution", "Inplant Internal Inage', 'Modify Authenticstion Processixae(2)", "Multi-Factor Authentication", "Ilybrid . Identit. look Rules", "Add-ins", "Volid Accountslxoe(2)", "Defsult Accounts", "Cloud Accounts", "Donsin Folify Modificationlxiag(1)", "Doeain Trust Hodification", "Event Triggered trecuthon", "Valid Accounts base(2)" " "Ceefault Accounts", "Cloud Accetunts", "Do main Policy Medificatianikag(1)', 'Domain Trust Modification", "Hide Artifactslucadi]". "Emall Midthe Rules"; "Imour Defens es'xaer3)", "Disable or Modify Tools", "Disable or Modify Cloud Firewal11", "Disable clsud Logs", "Tindicator kenovallaadi\}", e', "Unused/Unsupported Cloud Reglons", "Use Alternate Authentication Material bead(2)", "Applicathon Access Token", "Web Ses sion Cookle', "Walid Accountslowae(2)', "Default Accounts", "Cloud Accounts", "Brute Forcelura9(4)", "Passiond Gutssing', 'Pas sword Cracking", "Password Spraying", "Credentisl stuffing", "Forge web Credentislsiase(2)", "Meb Cookies", "SwIL. Tokens", "Modify Authentication Processixab(2)", "/ulti-factor Aatheoticatfon", "Hydrid Identity", "ihulti-factor Authentication Aeque st Generation', "Wetiork Sniffing', 'Steal Applicstion Access Token', "Steal. or Forge Authentication Certificates", 'Steal W eb Session Cookie", "Unsecured Credentfalsloae(2)", "CredentHols In Files", "Cloud instance Metadata apt". "Account Discover ylxae(2)", "Enafl Acceunt", 'Cloud Account", "Cleud Infrastructure DYscevery". "Cleud Service Paskbeard". "Cleud Service DIs covery', "Cloud Storage Object Discovery', "Network Service Discovery", "hetuork Sndtfing", "Passiond Policy Discovery", "Pe mation. Discovery", "System Location Discovery", "System Metwork Connections Discovery". "Internal Spearphishing", "Taint Sha red Content." "Use Alternate Authentication Asteriallucag(2)", "Application Access" Token", "Web Session Cookle", "Automated C ollection", "Dats from Cloud Storage", "Data from Inforeatlon hepositorfespeae(3)", "Confluence", "Sharepalst", "Code Reposi tories", "Data Stagedluxa(1)", "Renote Data Staging", "Endi Collectionlacad(2)", "Aenote Enail Collection", "Enail Fonvardin g. Rule", "Transfer Data to Cloud Account", "Accourt Access Renoval", 'Data Destruction", "bat. Encrypted for Impect", "Defac ement'lxad(1)", "External Defocenent', 'Endpodint Dendal of Servicelxad(3)", "Sendice Exhaudtion Flood", "Application Exhausti 1ificatien", "Aescurce Hijacking'] ['Drive-by Compromise', 'Exploit Public-Facing Application', 'Phishing'wa0(1)", 'Spearphishing Link', 'Trusted Relationshi p', 'Valid Accountslxae(2)', 'Default Accounts', 'Cloud Accounts', 'Serverless Execution', 'User Executionlxae(1)', 'Malicio us Image', "Account Manipulationlxa0(5)', 'Additional Cloud Credentials', 'Additional Enail Delegate Pernissions", "Addition al Cloud Roles", 'SSH Authorized Keys', "Device Registration', 'Create Accountlxae(1)', 'Cloud Account', 'Event Trggered Ex ecution", "Implant Internal Image', "Modify Authentication Processlxae(2)", "Multi-Factor Authentication', "Hybrid Identit y, 'Office Application Startuplxa@(6)', 'Office Tenplate Macros', 'office Test', 'Outlook Forns', 'Outlook Home Page', 'Out 'Domain Trust Hodiflcation', 'Event Triggered Executlon', 'Valid Accounts lxao(2)', 'Default Accounts', 'Cloud Accounts', 'Do main Policy Modificatianlxae(1)", "Domain Trust Modification', 'Hide Artifactslxae(1)', 'Emafl Hiding Rules", "Impair Defens eslxae(3)' "Disable or Modify Tools", "Disable or Modify Cloud Firewall', 'Oisable Cloud Logs", 'Indicator Renovallxa0(1)', 'Clear Mailbox Data', "Modify Authentication Processlxae(2)', "Multi-Factor Authentication", 'Hybrid Identity', "Modify Clou d Compute Infrastructurelxae(4)", "Create Snapshot', 'Create Cloud Instance', "Delete Cloud Instance', 'Revert Cloud Instanc e, 'Unused/Unsupported Cloud Regions', "Use Alternate Authenticatian Materiallxa0(2)', 'Application Access Token', 'Web Ses sion Cookie", "Valid Accountsixae(2)", "Default Accounts", 'Cloud Accounts", "Brute Forcelxao(4)', 'Passward Guessing', 'Pas sword Cracking", 'Password Spraying", 'Credential Stuffing', "Forge lieb Credentials bxae(2)", 'Heb Cookies', 'SAll Tokens", 'Modify Authentication Processlxao(2)', "MultI-Factor Authentlcatlon', 'Hybrid Identity', "Multl-Factor Authentication Aeque st Generation', 'Network Snifflng', 'Steal Application Access Token', 'steal or Forge Authentication Certificates', 'Steal W eb Session Cookle', 'Unsecured Credentlalslxa0(2)', 'Credentials In Files", 'Cloud Instance Metadota API', "Account Discover covery', 'Clowd Storage object Discovery', 'Network Service Discovery', "Network Sniffing', 'Password Policy Discovery', 'Pe relssion Groups Discoverylxa0(1)', "Cloud Groups", 'Softuare Discoverylxae(1)", 'Security Softuare Discovery', "Systei Infor mation Discovery', "System Location Discovery', "System Network Connectlons Olscovery", 'Internal Spearphishing", "Taint Sho red Content", "Use Alternate Authentication Materialleae(2)', 'Application Access Token', "Web Session Cookie', "Automated C ollection', 'Data from Cloud Storage", "Data from Informstion Repositoriesluad(3)", "Confluence', "Sharepoint', 'Code Reposi. tories", 'Data Stagedlxag(1)', "Remote Data Staging', 'Enall Collectlonixae(2)", "Remote Email Collectlon', 'Emall Forvardin g Rule', 'Transfer Data to Cloud Account", 'Account Access Renoval', "Data Destruction", "Data Enerypted for Inpact", 'Defac ementlxae(1)', "External Defacenent", 'Endpoint Denial of Servicelxae(3)", 'Service Exhaustion Flood', 'Application Exhausti on Flood', 'Application or Systen Exploitation', 'Network Denial of Servicelxae(2)', 'Direct Network, Flood', 'Reflection Anp Iification", 'Resource Hijacking']
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


