Question
Help please I want to add zookeeper, admin, and veterinarian to this code. This is my assignment. THIS IS MY CODE import java.io.BufferedReader; import java.io.FileReader;
Help please I want to add zookeeper, admin, and veterinarian to this code.
This is my assignment.
THIS IS MY CODE
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
import java.util.Scanner;
//Define a class Authentication
public class Authentication
{
//Define main
public static void main(String[] args) throws IOException
{
//Call method
loginScreenpro();
}
//Define a method
public static void loginScreenpro()
{
//Define string variable
String genPass = "";
//Declare variables
int flag1 = 0,attmpts=3;
//Define reader
BufferedReader br1 = new BufferedReader(new InputStreamReader(System.in));
//Display message
System.out.println(" Login");
//Try block
try
{
//Do
do
{
//Decrement value
attmpts--;
//Display message
System.out.println("Enter Username");
//Store value
String userName = br1.readLine();
//Display message
System.out.println("Enter Password");
//Store value
String password = br1.readLine();
//Create an instance
MessageDigest MD1 = MessageDigest.getInstance("md5");
//Update
MD1.update(password.getBytes());
//Call method
byte[] bytes12 = MD1.digest();
//Create an instance
StringBuilder Sb1 = new StringBuilder();
//Loop
for (int k = 0; k
{
//Append
Sb1.append(Integer.toString((bytes12[k] & 0xff) + 0x100, 16).substring(1));
}
//Generate password
genPass = Sb1.toString();
//Declare variable
String CurrLne;
//Define an instance
BufferedReader bin1 = new BufferedReader(new FileReader("/Users/Jess/NetBeansProjects/Final_Project/src/Credentials.txt"));
//Loop until end of file
while ((CurrLne = bin1.readLine()) != null)
{
//Split each line of file
String[] strArr = CurrLne.split("\t");
// If user name matches
if (strArr[0].equals(userName))
{
//If password matches
if (strArr[1].equals(genPass))
{
//Assign value
flag1 = 1;
//Break
break;
}
}
}
//If attempt is 0
if(attmpts==0)
{
//Display message
System.out.println("login more times");
//Display message
System.out.println("Exit...");
//Exit
System.exit(1);
}
//If flag is 1
if (flag1 == 1)
{
//Call method
AdminScrn();
//Break
break;
}
//Otherwise
else
{
//Display message
System.out.println("Invalid Username or Password.");
//Display message
System.out.println(" try again.");
//Display message
System.out.println(attmpts+" more attemptes left. ");
}
}
//Loop
while(attmpts>0);
}
//Define catch
catch (NoSuchAlgorithmException e1)
{
//Trace
e1.printStackTrace();
}
//Define catch block
catch (IOException e1)
{
//Trace
e1.printStackTrace();
}
}
//Define a method
public static void AdminScrn()
{
//Declare variable
String logOut1;
//Define scanner variable
Scanner sc1= new Scanner(System.in);
//Display message
System.out.println(" Welcome Admin"); System.out.println(" Welcome Admin");
//Display message
System.out.println("user Press 99 for log out ");
//Do loop
do
{
//Store value
logOut1 = sc1.nextLine();
}
//Loop
while(!logOut1.equals("99"));
//If value is 99
if(logOut1.equals("99"))
{
//Call method
loginScreenpro();
}
}
}
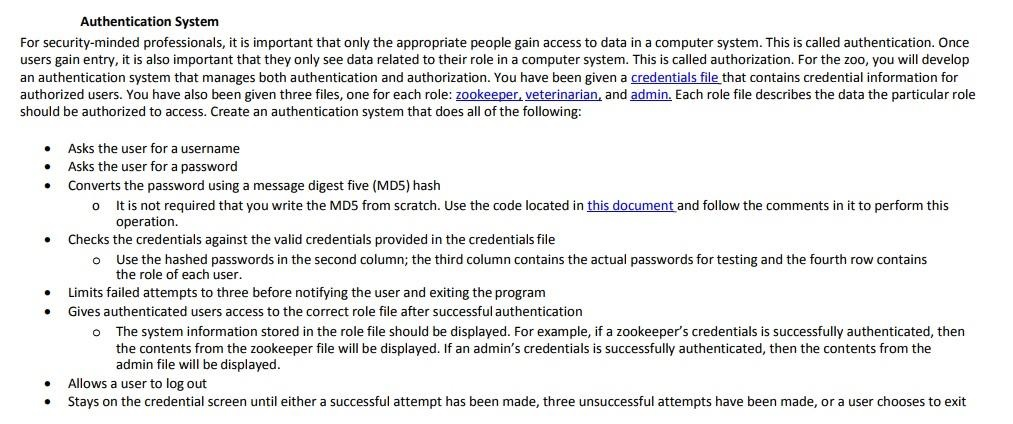
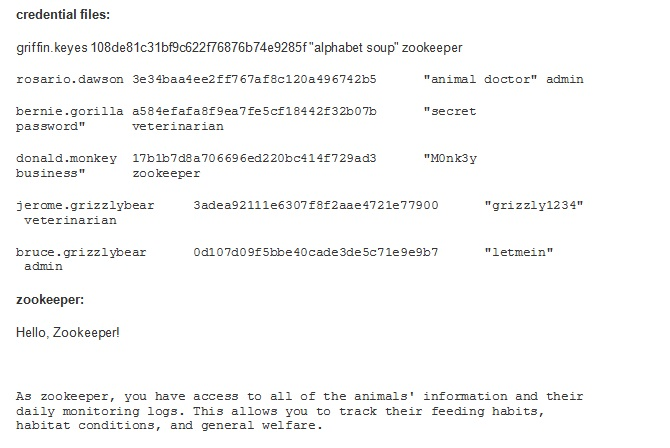
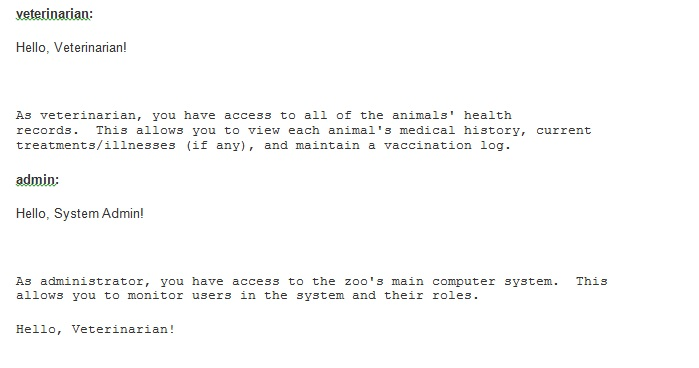
Authentication System For security-minded professionals, it is important that only the appropriate people gain access to data in a computer system. This is called authentication. Once users gain entry, it is also important that they only see data related to their role in a computer system. This is called authorization. For the zoo, you will develop an authentication system that manages both authentication and authorization. You have been given a credentials file that contains credential information for authorized users. You have also been given three files, one for each role: zookeeper,veterinarian, and admin, Each role file describes the data the particular role should be authorized to access. Create an authentication system that does all of the following: Asks the user for a username Asks the user for a password . Converts the password using a message digest five (MDS5) hash o t is not required that you write the MDS from scratch. Use the code located in this document and follow the comments in it to perform this operation. . Checks the credentials against the valid credentials provided in the credentials file Use the hashed passwords in the second column; the third column contains the actual passwords for testing and the fourth row contains the role of each user o .Limits failed attempts to three before notifying the user and exiting the program Gives authenticated users access to the correct role file after successful authentication The system information stored in the role file should be displayed. For example, if a zookeeper's credentials is successfully authenticated, then the contents from the zookeeper file will be displayed. If an admin's credentials is successfully authenticated, then the contents from the admin file will be displayed o Allows a user to log out Stays on the credential screen until either a successful attempt has been made, three unsuccessful attempts have been made, or a user chooses to exitStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


