help with these matchings pls
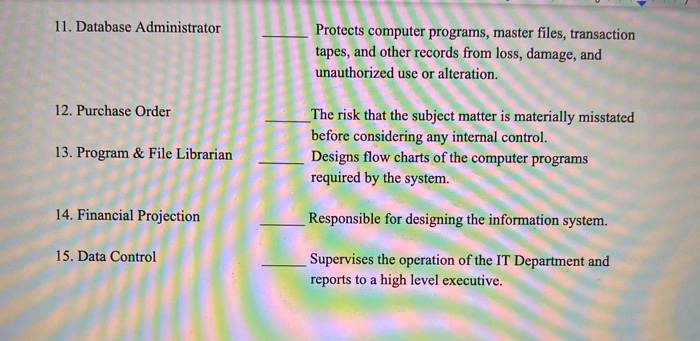
III. Matching - There are two columns below. The numbered column on the left corresponds to an answer on the right. In the space provided on the right column, please place the number from the left that corresponds to the correct answer. (20 matches, 1 points each, 20 points total). 1. Information Systems Manager Reviews and tests all input procedures, monitors processing, reviews exception reports, handles the reprocessing of exceptions detected by the system, and reviews and distributes all IT output. 2. Application programming Presents information about the entities expected financial position 3. Attestation Risk Responsible for planning and administering the 1 company's database. 4. Receiving Report Responsible for troubleshooting the operating system or systems in use, upgrading them when new software releases are provided by the vendor, company's database. 4. Receiving Report Responsible for troubleshooting the operating system or systems in use, upgrading them when new software releases are provided by the vendor, and working with application system programs when the applications interact with the operating system in a non-standard or problematic way. 5. Purchase Requisition The risk that internal control will fail to prevent or detect a material misstatement of the subject matter. 6. Systems Programming Selling company 7. IT Operations Bookkeeper / Comptroller 8. Financial Forecast Runs and monitors central computers in accordance with standard instructions. 9. Systems Analysis Purchasing Agent 10. Inherent Risk Treasurer 11. Database Administrator Protects computer programs, master files, transaction tapes, and other records from loss, damage, and unauthorized use or alteration 12. Purchase Order 13. Program & File Librarian The risk that the subject matter is materially misstated before considering any internal control. Designs flow charts of the computer programs required by the system. 14. Financial Projection Responsible for designing the information system. 15. Data Control Supervises the operation of the IT Department and reports to a high level executive. 16.Request for Check Loading Dock Manager 17. Control Risk The risk that the practitioners procedures will fail to detect a material misstatement of the subject matter. 18. Vendor Invoice Production Manager 19. Detection Risk 20. Invoice Approval Presents expected results given one or more hypothetical assumptions. The risk that the practitioners will unknowingly fail to appropriately modify their report on subject matter that is materially misstated