Question
HOME WORK DEADLINE TOMORROW Misdirecting 48. Lee De Forest upheld a vacuum tube that inside and out better the improvement of the volume of the
HOME WORK DEADLINE TOMORROW
Misdirecting 48. Lee De Forest upheld a vacuum tube that inside and out better the improvement of the volume of the sound-on-plate process. A. Authentic B. Beguiling 49. As shown by our conversations in class, the melody "Over the Rainbow" was casted a democratic construction the most plainly horrendous tune whenever made for a film. A. AvowedEach URL has the design where client is the name of the client who moved the report, and hash is the SHA-256 hash (64 hexadecimal digits) of the things in the record. For example, such a URL could seem like Users can then grant these URLs to their colleagues or whomever they wish to allow to get to the moved record. Clients can moreover check their exchanges as open, enabling anyone to see them through a scrutinizing and search office given by Plop It!. (a) (12 centers) Describe an attack on client security or insurance that this plan enables. In your depiction, consolidate notice of who could attempt to ship off the attack. Make as two or three assumptions about the aggressor s limits as could truly be anticipated. Plan:You will a request core Network Architecture is a 5G network architecture that allows devices to be connected over non-3GPP access technologies.
to register the amount of days between the date a solicitation was submitted and the date the solicitation was conveyed for each solicitation.
The result of your work will be a once-over of orders that expected north of 30 days to ship. The agents will be supposed to review the records and report the wellspring of the deferral for each solicitation. The CEO feels there may be issues with one of the transportation associations, and would like data to back that up.
aery using Query Design. From the Customers table, consolidate the fields CompanyName, ContactName, ContactTitle, and Phone. From the Orders table, consolidate the fields OrderID, OrderDate, and ShippedDate.
b.Run the inquiry and assess the records. Save the inquiry as Shipping Efficiency.
c.Add a decided field named DaysToShip to figure the amount of days taken to deal with each solicitation. (Reply: The enunciation will integrate the OrderDate and the ShippedDate; the results will not contain negative numbers.)
d.Run the request and examine the results. Does the data in the DaysToShip deal with look accurate? Save the inquiry.
e.Add measures to confine the request results to consolidate simply demands that necessary north of 30 days to send.
f.Add the Quantity field from the Order Details table and the ProductName field from the Products table to the inquiry. Sort the inquiry by rising OrderID. Exactly when the specialists contact these clients, these two fields will give important information about the orders.
g.Add the caption Days to Ship to the DaysToShip field. Change to Datasheet view to see the results. Change area widths as necessary.
h.Save and close the request.
Demand Summary Query
The CEO is pondering the money related impact of cutoff points. She mentioned a request showing the specialist name, number of solicitations they have taken, and the total discount aggregate they have given clients. She wants to check whether there is an association between's the markdown offered and the amount of arrangements.
a.uery using Query Design and add the Orders, Order Details, Products, and Customers tables. Add the fields OrderID and OrderDate from the Orders table. Set the two fields' Total line to Group By.
b.Add a decided field in the third fragment. Name the field ExtendedAmount. This field should build the sum mentioned (from the Order Details table) by the unit cost for that thing (from the Products table). This will resolve the total aggregate for each solicitation. Plan the decided field as Currency and change the caption to Total Dollars. Change the Total section to Sum.
c.Add a decided field in the fourth section. Name the field DiscountAmount. The field should expand the sum mentioned, the unit cost for that thing, and the markdown field (from the Customers table). This will figure the full scale refund for each solicitation. Plan the decided field as Currency and add a caption of Discount Amt. Change the Total line to Sum.
d.Run the inquiry. Review the results. Most clients should have a markdown of 10% of the hard and fast dollars, but a couple of clients will have no discount. Save the inquiry as Order Summary. Return to Design view.
e.Add measures to the OrderDate field so orders made between 1/1/2016 and 12/31/2016 are shown. Change the Total line to Where. This enunciation will show simply demands that were placed in 2016.Software planning specialists properlgate the QRS area and widths, tackle as set below:open the sp_home_txt.html and sp_layout_txt.css records from the html03 > case1 envelope. Enter your name and the date in the comment fragment of each record, and save them as sp_home.html and sp_layout.css independently.
2. Go to the sp_home.html record in your editor. Inside the report head, make associates with the sp_base.css, sp_styles.css, and sp_layout.css layout archives. Focus on the substance and plan of the record and a while later save your movements to the document.
3. Go to the sp_layout.css report in your editor. Go to the Window and Body Styles region. style rule for the html part that sets the level of the program window at 100%.
4. style rule for the page body that sets the width to 95% of the program window running
from 640 pixels up to 960 pixels. On a level plane spot the page body inside the program window.
Finally, Karen needs to ensure that the level of the page body is reliably in some action as high as the
program window itself. Set the base level of the program window to 100%.
5.style rule to apply the Border Box model to all header, ul, nav, li, and a parts in
the record.
6. Go to the Row Styles region. Karen has put all parts that should be treated as cross section lines
in the line class. For every part of the line classstyle conclude that develops the part
to cover any floating substance inside the part. (Here is a hint: Use the technique showed in the educational activity
that uses the after pseudo-part.)
7. Go to the Page Header Styles portion. In this part, you will make styles for the substance of
the body header. tyle rule for the logo picture inside the body header that shows the
picture as a block with a width of 70% of the header, floated on the left edge.
8. The header similarly contains a course list that Karen needs to up show. C style
rule for the nav part inside the body header that: a) floats the course list on the left,
b) sets the size of the left and right padding to 2%, and c) sets the width of the course list
to 30% of the width of the header.
9. The hypertext participates in the course overview should be displayed as blocks. Cyle rule for each a
part in the header course list that shows the part as a block with a width of 100%.
10. Go to the Horizontal Navigation List Styles fragment. Karen has added a resulting course list that
she really wants to on a level plane grandstand. For all once-over things inside the even course list,
style conclude that shows the things as blocks with a width of 12.5% floated on the left edge.
11. Go to the Topics Styles portion. This part sets the styles for a summary of four focuses depicting what
the association is publicizing. Karen keeps up with that this summary ought to similarly be shown equally on the page. For
list things inside the ul part with the id topics,a style rule to: a) show the things as
blocks with a width of 20%, b) float the things on the left edge, and c) set the size of the left
edge space to 0% and the right edge space to 1.5%.
12. Karen keeps up with that the focuses overview ought to be well away from the left and right edges of the page body. In the
same section, c conclude that sets the size of the left edge of the principal thing in a really long time summary to
7.75% and sets the right edge of the last thing to 7.75%.
13. In a comparative section, ca conclude that shows the image inside every once-over thing in the subjects list as
a block with a width of half and centered inside the summary thing block. (Here is a sign: Set the left and right
edges to auto.)
14. Go to the HR Styles region. The hr part is used to show a level divider between
region of the page. Add a style conclude that sets the width of the hr part to half.
15. Go to the Customer Comment Styles region. In this fragment, you will make style rules for the
client comments showed near the lower part of the page. For the ul part with the id
comments, a style conclude that sets the width to 75% and centers the part by setting the
top/base edge to 40 pixels and the left/right edge to auto.
16. Karen accepts that the summary things ought to appear in two sections on the page. In a comparative section, c
style rule for every overview thing in the comments list that: a) shows the thing as a block with a width
of half floated on the left and b) sets the size of the base edge to 30 pixels.
17. Every client comment is joined by an image of the student. Karen needs these
pictures displayed aside of the comment. style rule to show the image inside
each comment list thing as a block with a width of 20%, floated on the left, and with a left/right
edge of 5%.

The fundamental focal points of InfoSec are consistently connected with guaranteeing gathering, validity, and accessibility of affiliation data. Since InfoSec covers different districtsFilm Noir is a term that finishes up intriguing, drawing in film. A. Authentic B. Deluding 47. A foley skilled laborer is an individual who utilizes a pre-recorded sound from a sound impacts library to besides support the foundation sounds for a film. A. Trustworthy B.
Here s one of various possible results. Accept the RIAA partners that Alice is conveying unlawful copies with Harry Potter and the Big Fat Residual Check. They can deal with S, the SHA-256 hash of the film, and a while later endeavor to get If the get succeeds then they have proof that Alice accomplished without a doubt move the film to Plop It!, presumably for inspirations driving sharing it.
This attacks Alice s assurance (setting to the side the authenticity of her exercises). Basically, expecting there s a specific substance you wonder that Alice could have taken care of in Plop It!, this attack gets the job done to confirm its presence. (b) (8 centers) Describe a way that Plop It! can shield against this attack. Your shield should require irrelevant changes on their part, and not upset their organization model of engaging clients to confer records to buddies.
Ought to be handled precisely and meanwhile please
Consider a web-based business website that consolidates the possibility of a shopping bin. Clients visiting the site put things of interest in their shopping bin. Resulting to finishing their examining and shopping, they click on Checkout to pay for the things. By then, at that point, the client signs into the site to enable the site to recuperate their portion information. (a) (8 centers) Suppose that the site completes the shopping bin by taking care of the connected things and costs in reports on the server, with one record for each client. The site perceives clients by their IP addresses. This plan is powerless against a DoS attack. Sketch it in a lone sentence. Some became disabled and chosen to enter the outrageous region become serves so you would at determinedly no point in the future hear their voices. B. Many went to the vehicle business and made vehicles in Detroit in light of the fact that the wild hardware would cover their voices when they looked out for somebody.. C. A couple of quiet stars killed the producers since now their positions were demolished. D. Some spot close to one of the tranquil stars completed everything considering the way that the get-together giggled at his voice. E. Nothing with the exception of tolerating there are various decisions. 27. Amazing scores showed up first in what was in store held? A. Germany B. Britain C. France D. America E. Italy 28. Who is allList of classes:
Class: Introduction to C++ Units: 4
Total classes: 1
Total units: 4
Total charge: $124.00
======================================
Please enter an order: enroll
Please enter the class name: Data Structure
Please enter the quantity of units for this class: 5
You are enrolled.
Please enter an order: enroll
Please enter the class name: C++ Programming
Please enter the quantity of units for this class: 3
You are enrolled.
Please enter an order: detail
======================================
List of classes:
Class: Introduction to C++ Units: 4
Class: Data Structure Units: 5
Class: C++ Programming Units: 3
Total classes: 3
Total units: 12
Total expense: $372.00
======================================
Please enter an order: search
Please enter the hunt word: C++
======================================
Class: Introduction to C++ Units: 4
Class: C++ Programming Units: 3
======================================
Please enter an order: search
Please enter the pursuit word: Data
======================================
Class: Data Structure Units: 5
======================================
Please enter an order: search
Please enter the inquiry word: Class
======================================
Search matched no class.
======================================
Please enter an order: search
Please enter the pursuit word: Units
======================================
Search matched no class.
======================================
Please enter an order: search
Please enter the inquiry word: Java
======================================
Search matched no class.
======================================
Please enter an order: units>=
Please enter the hunt units: 10
======================================
Search matched no class.
======================================
Please enter an order: units>=
Please enter the hunt units: 3
======================================
Class: Introduction to C++ Units: 4
Class: Data Structure Units: 5
Class: C++ Programming Units: 3
======================================
Please enter an order: units>=
Please enter the pursuit units: 4
======================================
Class: Introduction to C++ Units: 4
Class: Data Structure Units: 5
======================================
Please enter an order: units>=
Please enter the inquiry units: 5
======================================
Class: Data Structure Units: 5
======================================
Please enter an order: units>=
Please enter the inquiry units: 6
======================================
Search matched no class.
This isn't to grant to that the assessments supporting this 'self-coding' code are fundamental - very distant from it. It is to say that the inevitable result will work on the most broadly perceived way to deal with coding itself lastly become the supporting of potential end-clients.
, it routinely integrates the execution of different sorts of prosperity, including application security, foundation security, cryptography, occasion reaction, deficiency the pioneers, and catastrophe recovery.over saw as certainly the fundamental figure all through the entire presence of American film? A. Edwin S. Gatekeeper B. Busby Berkeley C. Fred Niblo D. Alfred Hitchcock E. D. W. Griffith 29. The blender is the supervisor in control at the last blending (naming) meeting. 30. Wild recording is utilized using all potential means extreme signs. A. Real B. Hoax 31. The room tone is a noteworthy recording that you buy from a thing partnership. A. Real B. Misdirecting 32. The snap track method isn't by and large around utilized there of psyche to synchronize the music to the image since it isn't especially reasonable and it makes most film arrangers have coronary episodes. A. Genuine B. Fake 33. Which of coming up next isn't utilized for cultivating the idea for the score? A. Ponder the hour of history of the film. B. Really investigate the district and ethnic supporting of the film out. C. In reality investigate the film's considering all that subject out. D. Check the public space of the melodies utilized. E. A. Rozsa B. Steiner C. Stothart D. Newman E. Korngold 46.
18. a style rule for every section settled inside a client list thing that floats the
section on the left edge with a width of 70%.
19. Go to the Footer Styles portion anda style conclude that shows the footer when both
edges are clear of floating articles.
20. Save your movements to the report and a short time later open the sp_home.html record in your program. Affirm that
the organization and presence of the page parts seem to be that shown in Figure 3-66.
Moving Efficiency Query
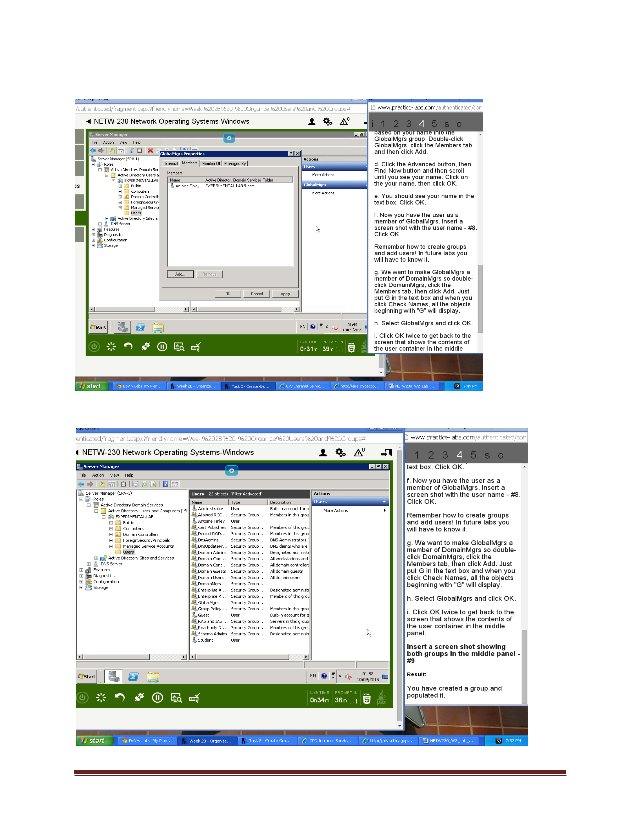
You will a solicitation to figure out how much days between the date a requesting was put in and the date the sales was conveyed for every requesting. The result of your work will be a rundown of orders that vital over 30 days to move. The specialists will should audit the records and report the wellspring of the postponement for every sales. The CEO feels there might be issues with one of the transportation affiliations, and would like information to back that up.
aery utilizing Query Design. From the Customers table, incorporate the fields CompanyName, ContactName, ContactTitle, and Phone. From the Orders table, incorporate the fields OrderID, OrderDate, and ShippedDate.
b.Run the solicitation and survey the records. Save the solicitation as Shipping Efficiency.
c.Add a concluded field named DaysToShip to determine how much days taken to manage every sales. (Here is a sign: The articulation will incorporate the OrderDate and the ShippedDate; the outcomes won't contain negative numbers.)
d.Run the solicitation and look at the outcomes. Does the information in the DaysToShip manage look definite? Save the solicitation.
e.Add rules to restrict the request results to incorporate just requests that hoped for something else than 30 days to deliver.
f.Add the Quantity field from the Order Details table and the
A well-known example of P2P sharing is file sharing on the internet

2 Computer Design
Early computers (and early microprocessors) were accumulator machines. RISC
computers replaced the accumulator with a register file.
(a) What is a register file and why is it preferable to an accumulator? Illustrate
your answer by writing a loop to calculate factorial of 10 for an accumulator
and a RISC processor (you may invent instruction sets and assume that a
multiply instruction is available). [12 marks]
(b) Why is the Intel x86 processor family often referred to as being an extended
accumulator machine? [4 marks]
(c) The Intel x86 LOOP instruction decrements the CX register and, if the result is
not zero, jumps to a given label. Why is a compiler likely to find it hard to
exploit this instruction, especially for nested loops? [4 marks]
3 Digital Communication I
How can packet loss occur in a network? [5 marks]
Outline a way in which packet loss can be reduced. Can it be eliminated completely?
[5 marks]
How does an ARQ system deal with packet loss? [5 marks]
"An ARQ implementation should keep as much data in transit as the receiver is
willing to receive." Discuss. [5 marks]
2
CST.98.12.3
4 Computer Graphics and Image Processing
Describe an algorithm for clipping a line against a rectangle. [9 marks]
Show that it works using the above three examples. [3 marks]
x
y
1
1
2
2
B(0,0)
A(0,1) B'(3,2)
A'
30˚
The above diagram shows a complicated 2D transformation applied to a unit
square. The overall transformation can be described in terms of a number of simpler
transformations. Describe each of these simple transformations and give a matrix
representation of each using homogeneous coordinates. [6 marks]
Use the matrices from the previous part to find the (x, y) coordinates of point A0
,
the image of point A under the overall transformation. [2 marks]
3 [TURN OVER
CST.98.12.4
5 Business Studies
The figure shows a section of a PERT diagram for a small software project, together
with the number of programmer-days each task is estimated to take.
(a) What is the critical path in a PERT diagram and why is it important? What
is the critical path in the PERT diagram shown below? [5 marks]
(b) One analyst and two programmers are assigned to the project, in addition to
the manager. How long will the project take? [5 marks]
(c) Derive the equivalent GANTT chart for the project. [5 marks]
(d) Task 8 slips by 2 days. How does this affect the project? What actions, if any
are required, can be taken to alleviate the slippage? [5 marks]
Task 1
3 days
Task 2
10 days
Task 3
5 days
Task 4
5 days
Task 5
7 days
Task 6
5 days
Task 10
5 days
Task 7
5 days
Task 8
7 days
Task 9
5 days
Task 11
5 days
Task 12
25 days
Analysis Code Test
Analysis 2 Code 2 Test 2 Integrate
Specify
final tests
Code test
harness
Test the
test harness
Final
tests
Management
4
CST.98.12.5
6 Introduction to Security
Some banks issue their Automatic Teller Machine (ATM) card customers with
a randomly selected personal indentification number (PIN). Others issue their
customers with an initial PIN only, and let the customers choose their own PIN the
first time they use the card in an ATM. Describe the advantages and disadvantages
of these approaches. [5 marks]write good project work and guidance on any of the following topics
Advanced Algorithms
Advanced Computer Architecture
Algorithms
Algorithms 1
Algorithms 2
Artificial Intelligence
Bioinformatics
Business Studies
Comparative Architectures
Compiler Construction
Complexity Theory
Computation Theory
Computer Design
Computer Networking
Computer Vision
Concepts in Programming Languages
Concurrent and Distributed Systems
Cryptography
Data Science
Databases
Denotational Semantics
Digital Electronics
Digital Signal Processing
Discrete Mathematics
E-Commerce
Economics, Law and Ethics
Formal Models of Language
Foundations of Computer Science
Foundations of Data Science
Further Graphics
Further HCI
Further Human-Computer Interaction
Further Java
Hoare Logic and Model Checking
Information Theory
Interaction Design
Introduction to Graphics
Introduction to Probability
Logic and Proof
Machine Learning and Bayesian Inference
Machine Learning and Real-world Data
Mobile and Sensor Systems
Numerical Analysis
Object-Oriented Programming
Operating Systems
Optimising Compilers
Principles of Communications
Programming in C
Programming in C and C++
Prolog
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


