Answered step by step
Verified Expert Solution
Question
1 Approved Answer
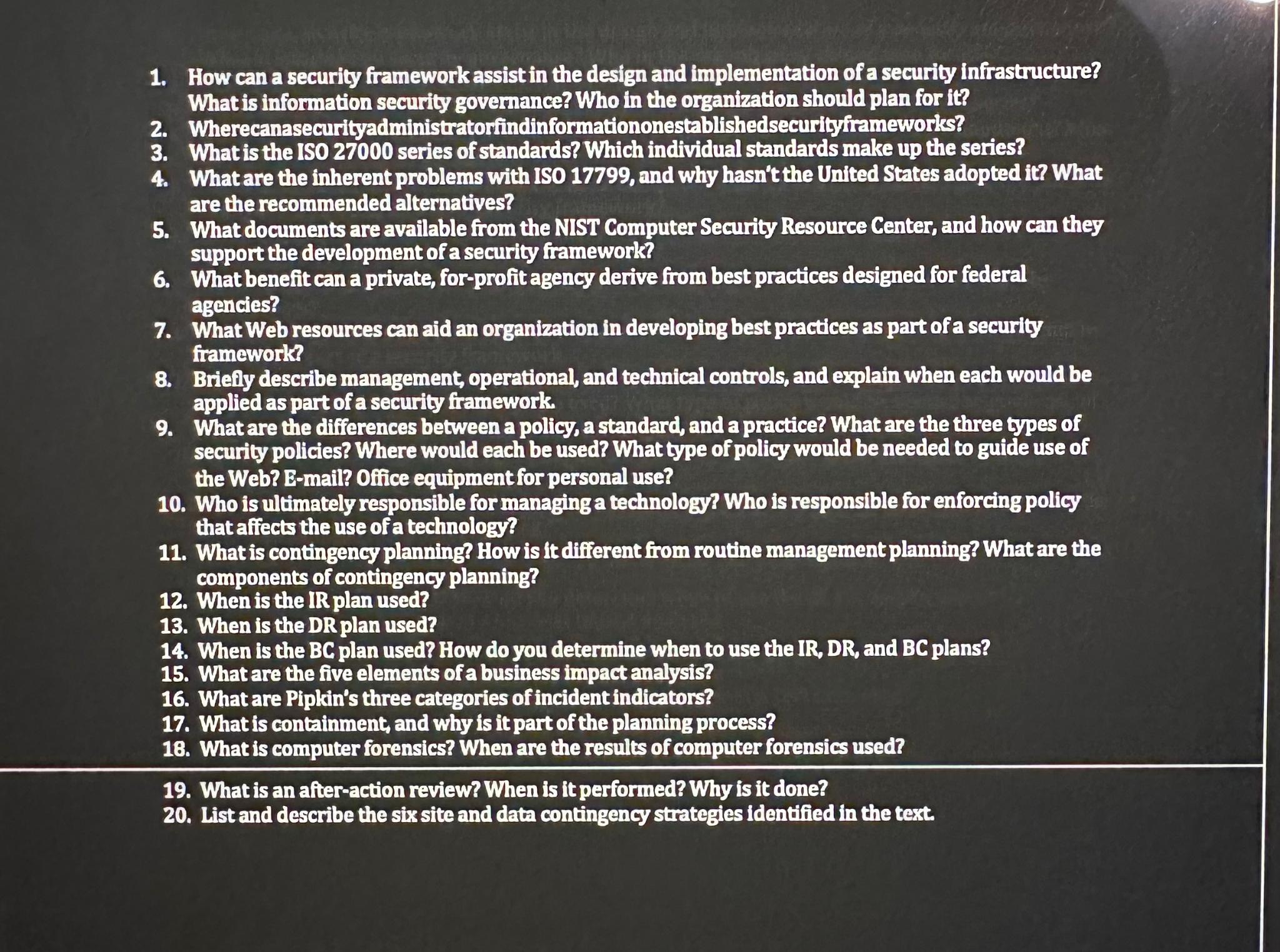
How can a security framework assist in the design and implementation of a security infrastructure? What is information security governance? Who in the organivation should
How can a security framework assist in the design and implementation of a security infrastructure? What is information security governance? Who in the organivation should plan for
Wherecanasecurityadministratorfindinformationonestablishedsecurityframeworks?
What is the series of standards? Which individual standards make up the series?
What are the inherent problems with ISO and why hasn't the United States adopted it What are the recommended alternatives?
What documents are available from the NIST Computer Security Resource Center, and how can they support the development of a security framework?
What benefit can a private, forprofit agency derive from best practices designed for federal agencies?
What Web resources can aid an organiration in developing best practices as part of a security framework?
Brielly describe management, operational, and technical controls, and explain when each would be applied as part of a security framework.
What are the differences between a policy, a standard, and a practice? What are the three types of security policies? Where would each be used? What type of policy would be needed to guide use of the Web? Email? Office equipment for personal use?
Who is ultimately responsible for managing a technology? Who is responsible for enforcing policy that affects the use of a technology?
What is contingency planning? How is it different from routine management planning? What are the components of contingency planning?
When is the IR plan used?
When is the DR plan used?
When is the BC plan used? How do you determine when to use the IR DR and BC plans?
What are the five elements of a business impact analysis?
What are Pipkin's three categories of incident indicators?
What is containment, and why is it part of the planning process?
What is computer forensics? When are the results of computer forensics used?
What is an afteraction review? When is it performed? Why is it done?
List and describe the six site and data contingency strategies identified in the text.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


